Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.

No Results Found
Oops! No Blog found for this category.
Get the latest
Sublime releases, detections, blogs, events, and more directly to your inbox.
Oops! Something went wrong while submitting the form.
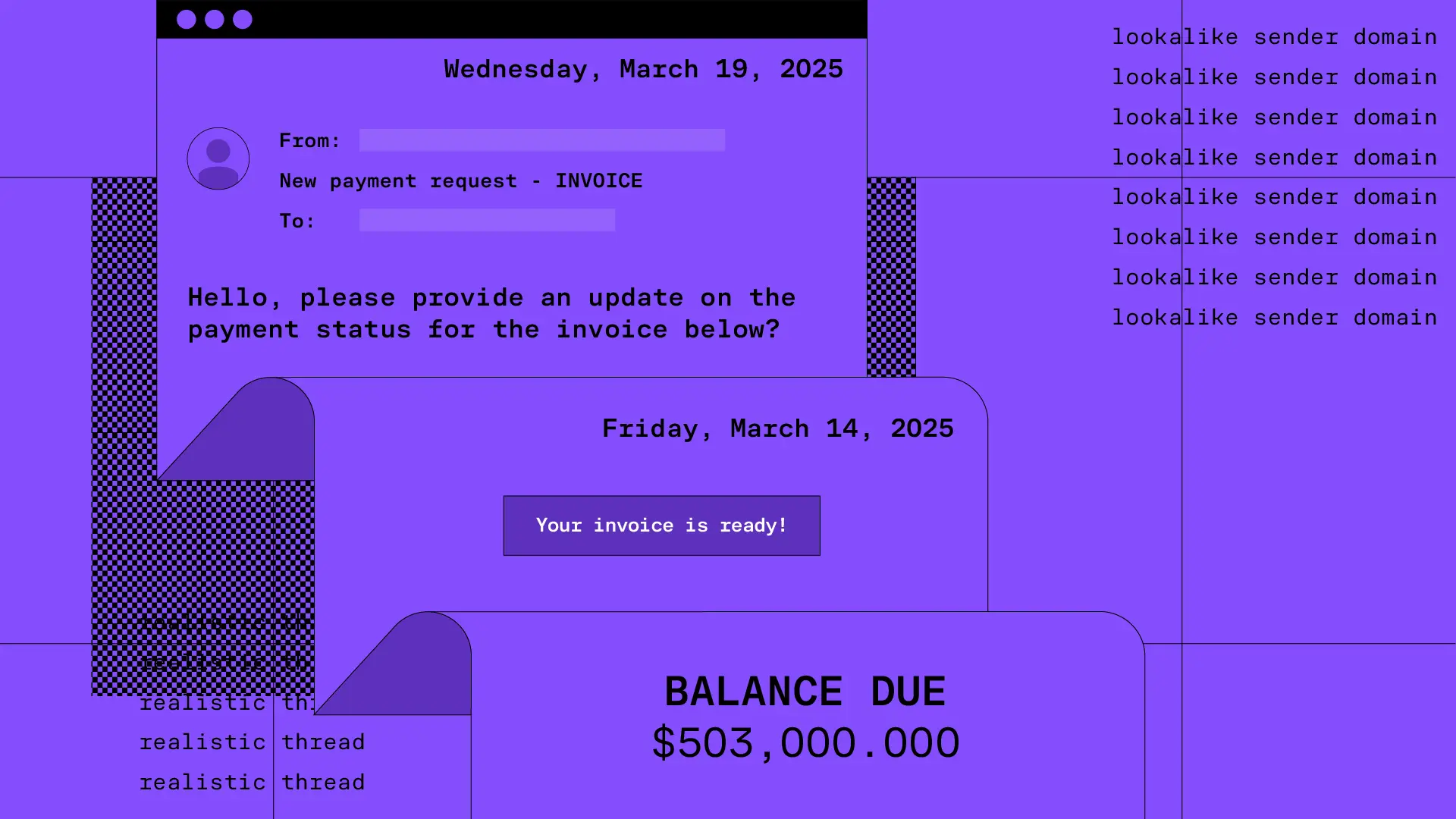
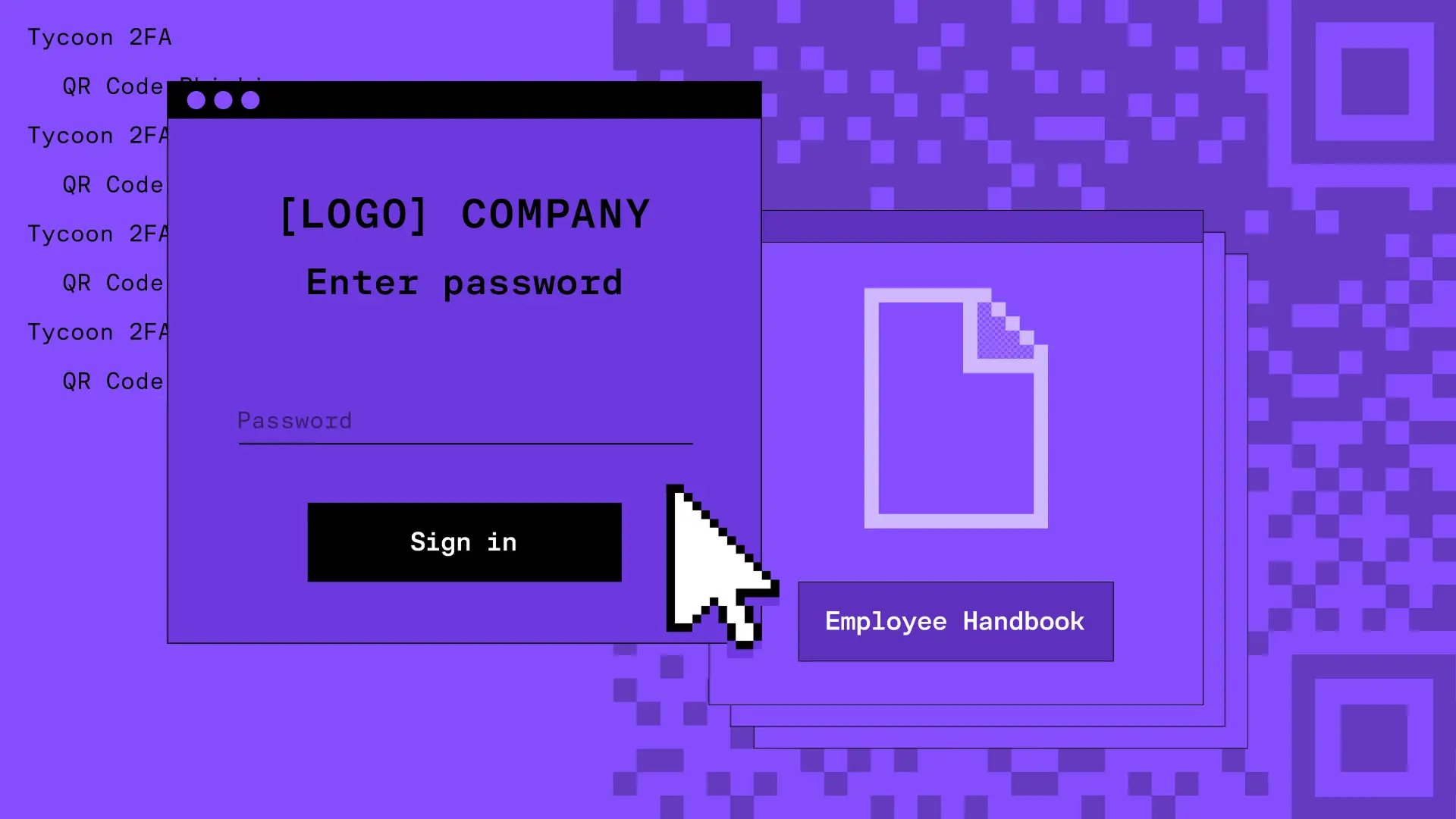
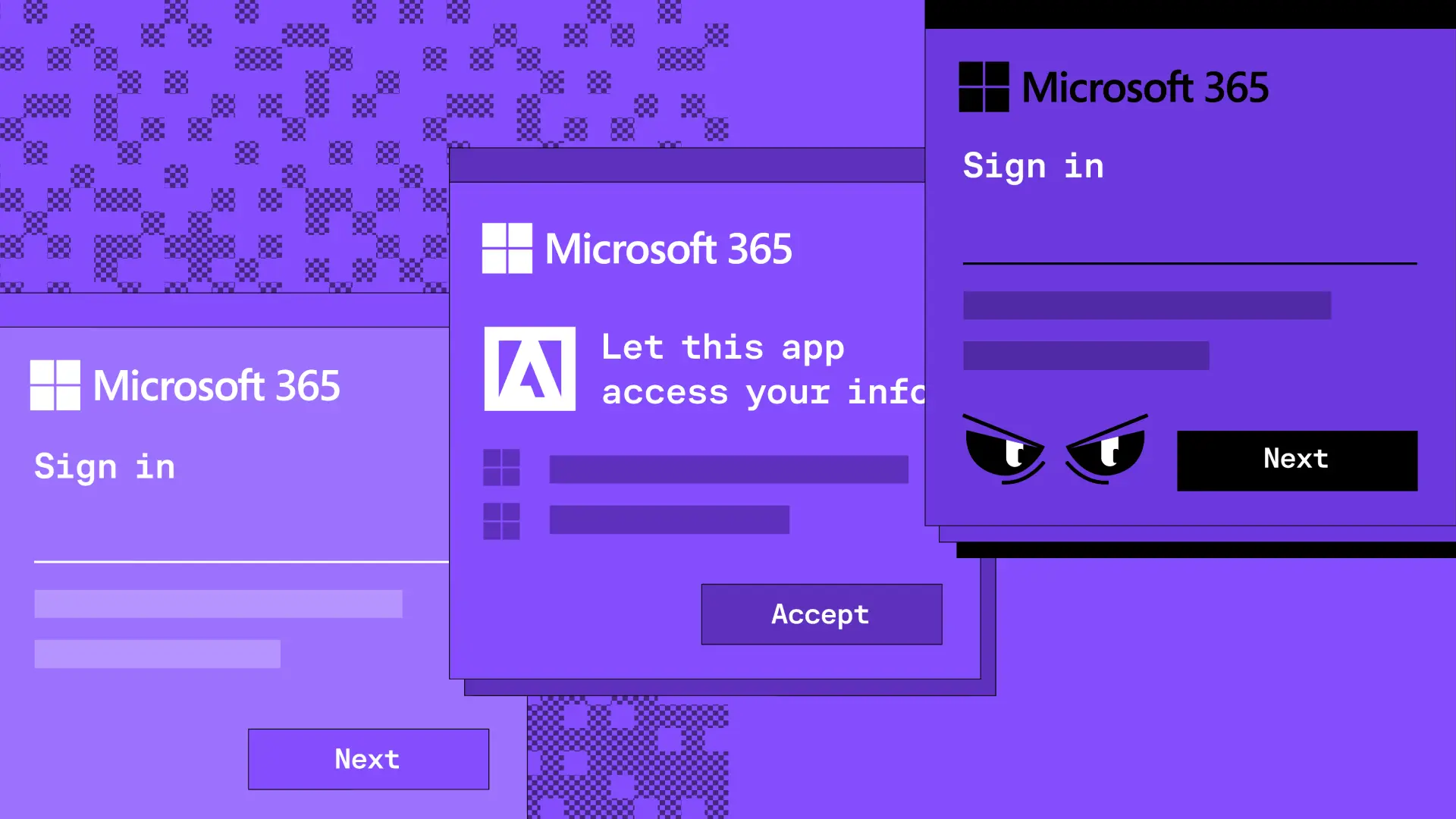
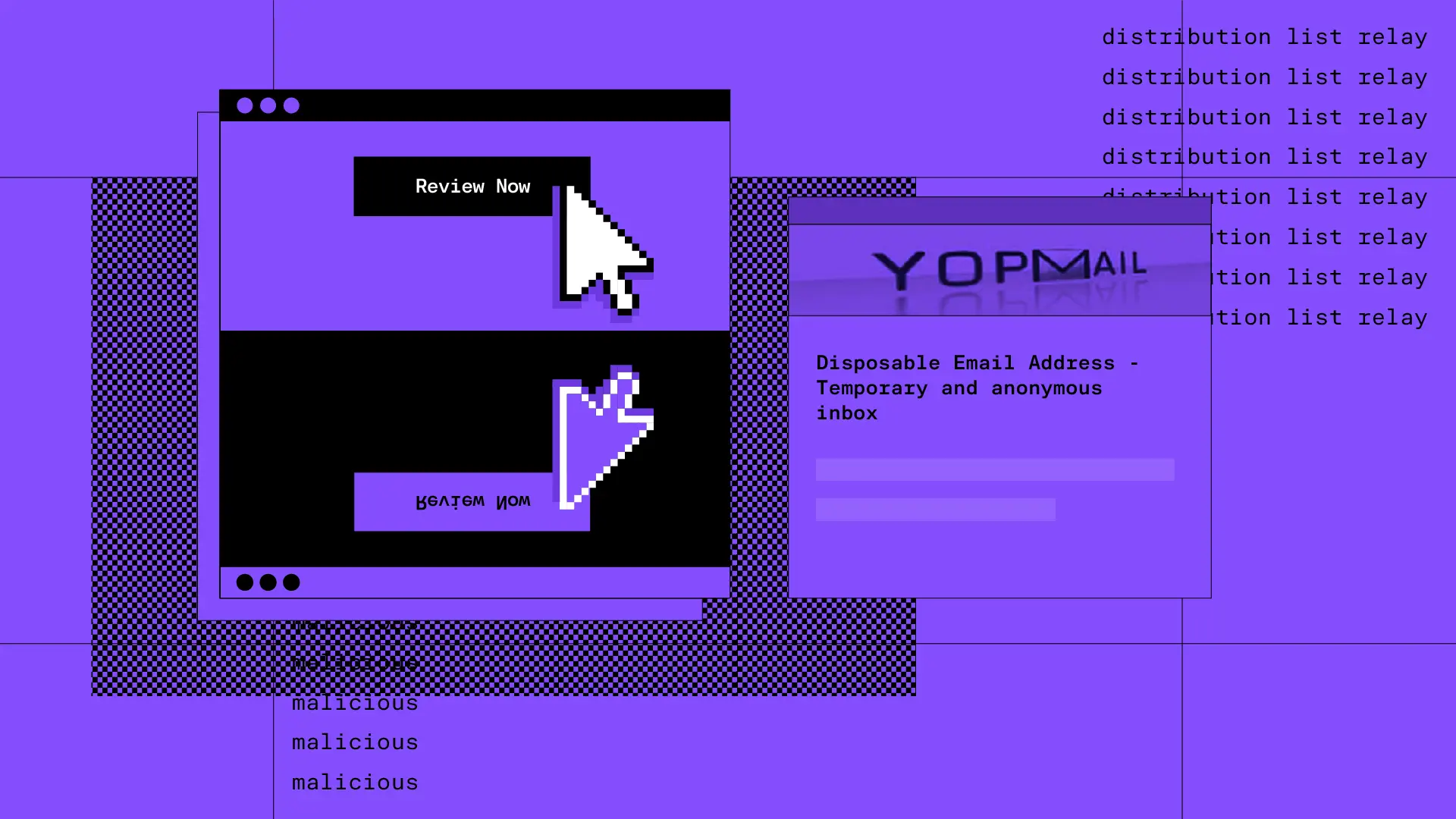
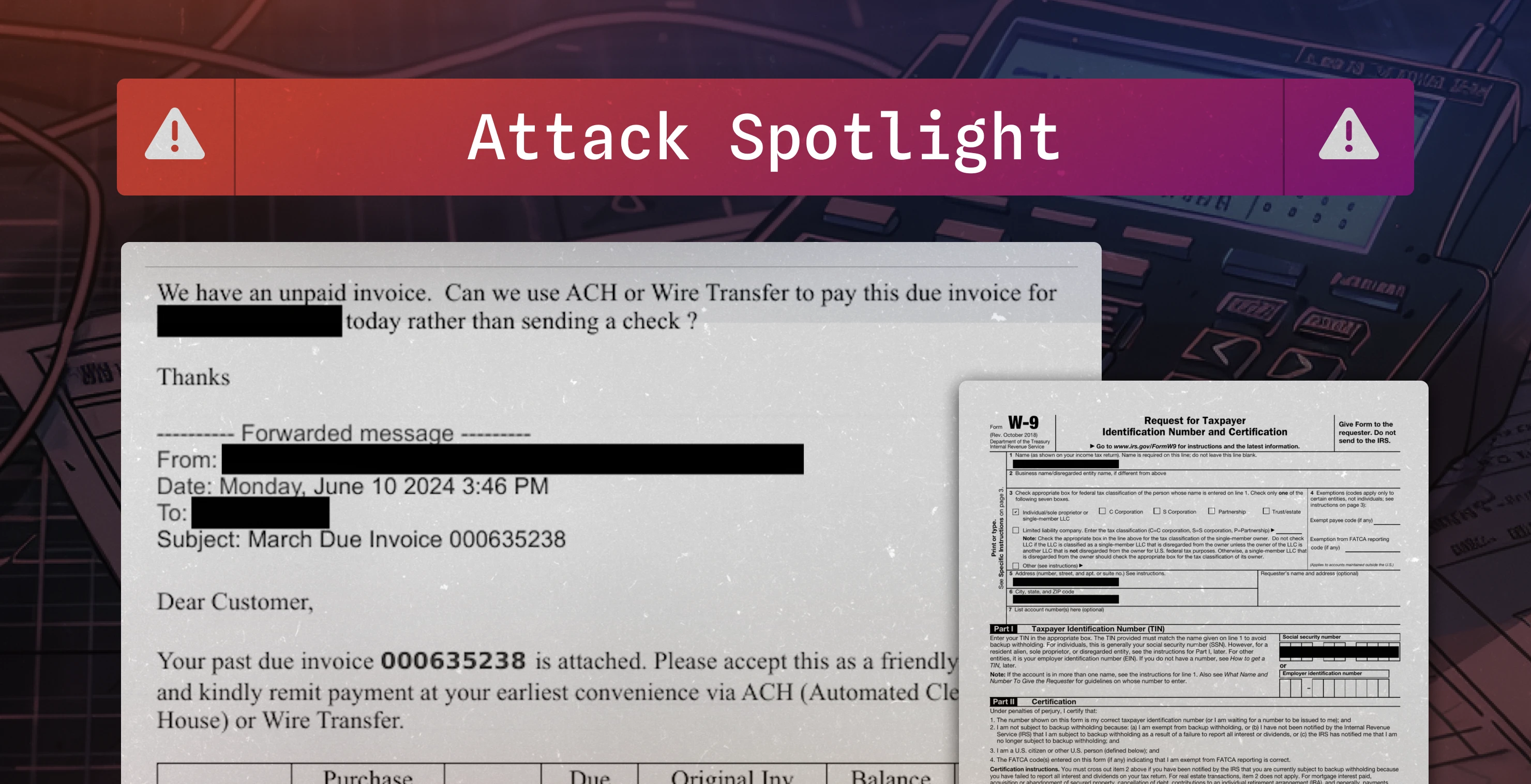
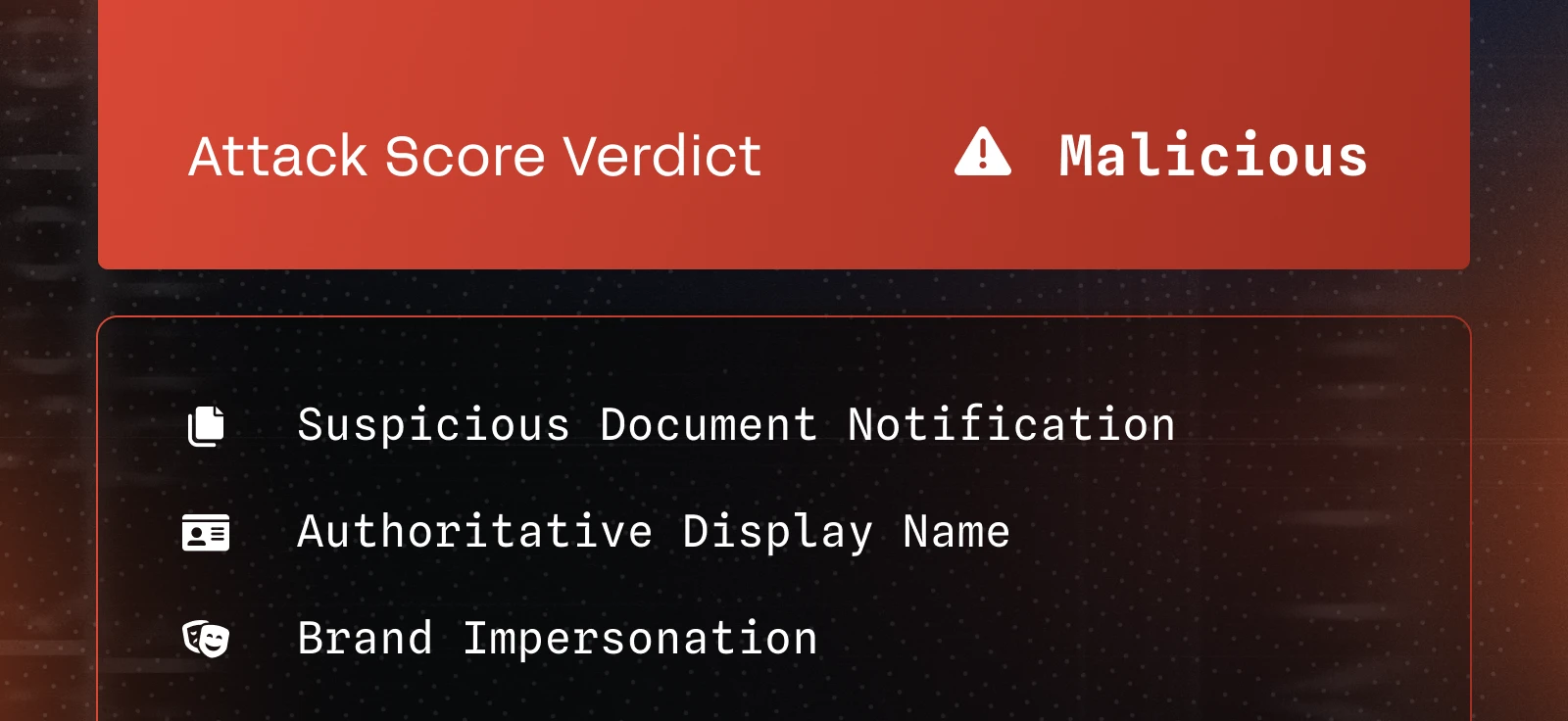
Now is the time.
See how Sublime delivers autonomous protection by default, with control on demand.
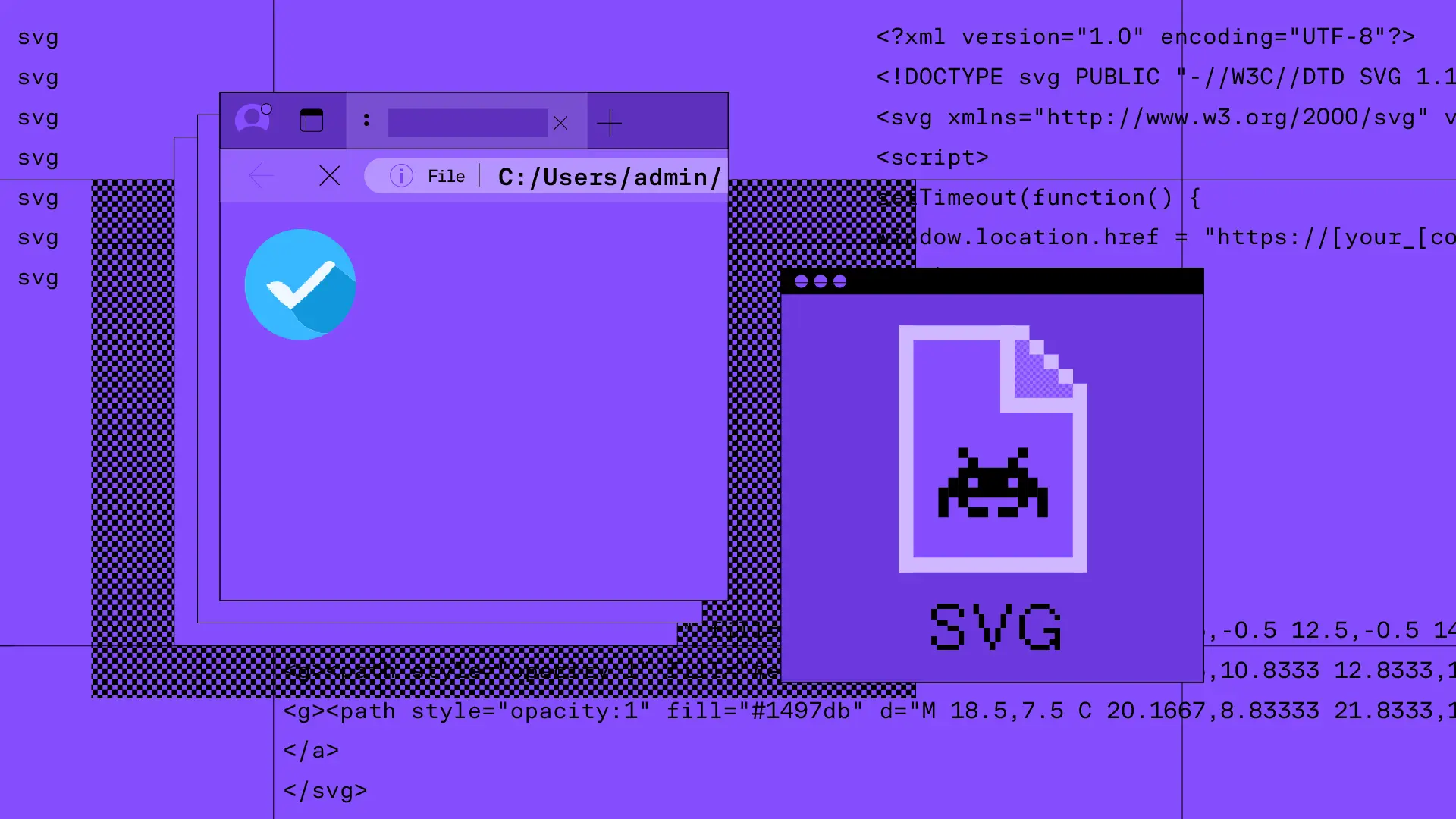
.svg)











.png)













.png)