Automate email detection and response
Detect, triage, investigate, and remediate email-based threats faster than ever with Sublime.
.svg)
.svg)
M-SOAR with Sublime
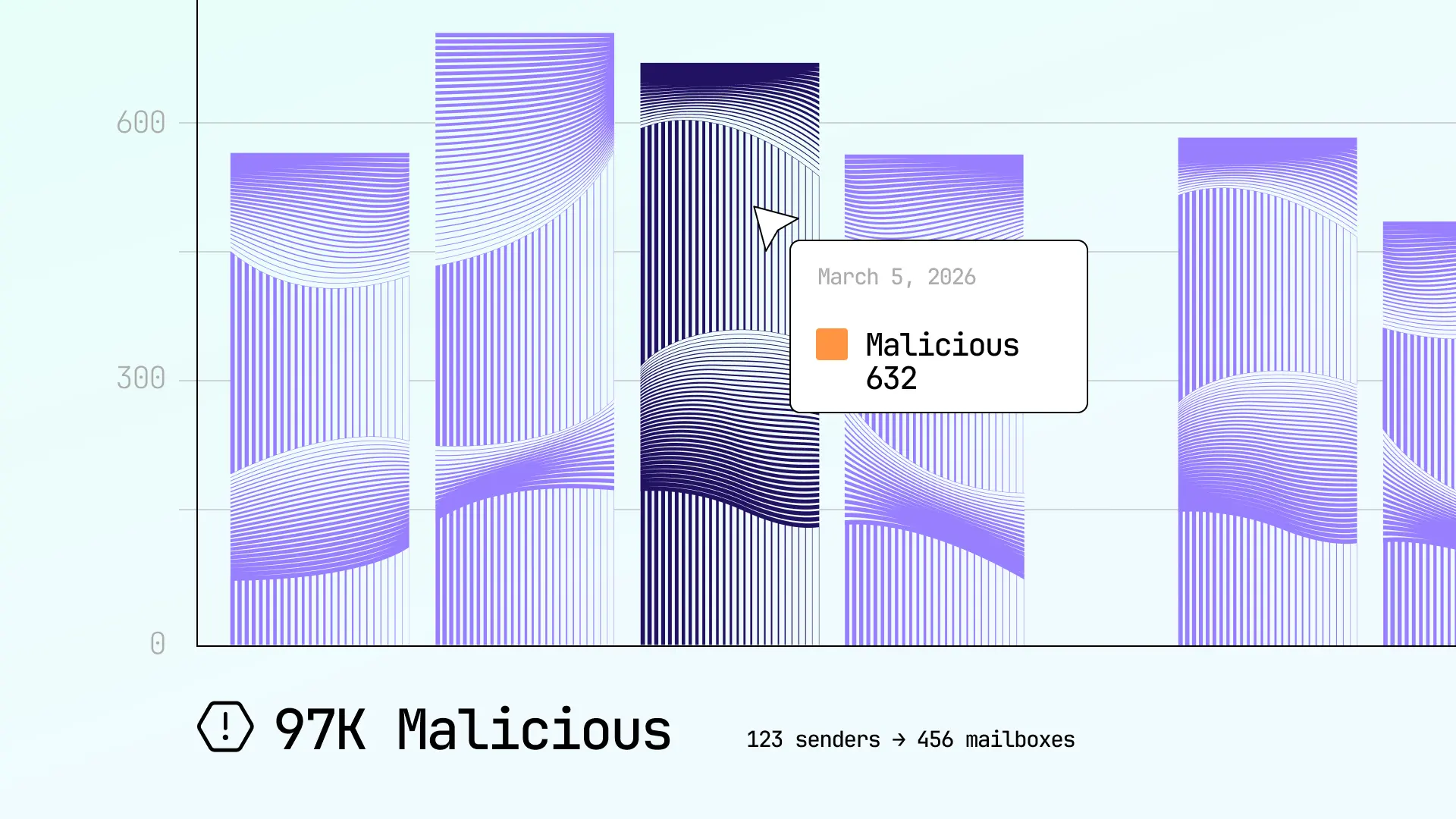
Sublime streamlines email security operations by automating the handling of user reports and automating the investigation, containment, and remediation of email-borne threats to reduce response times and analyst fatigue.

Autonomous Security Analyst (ASA)
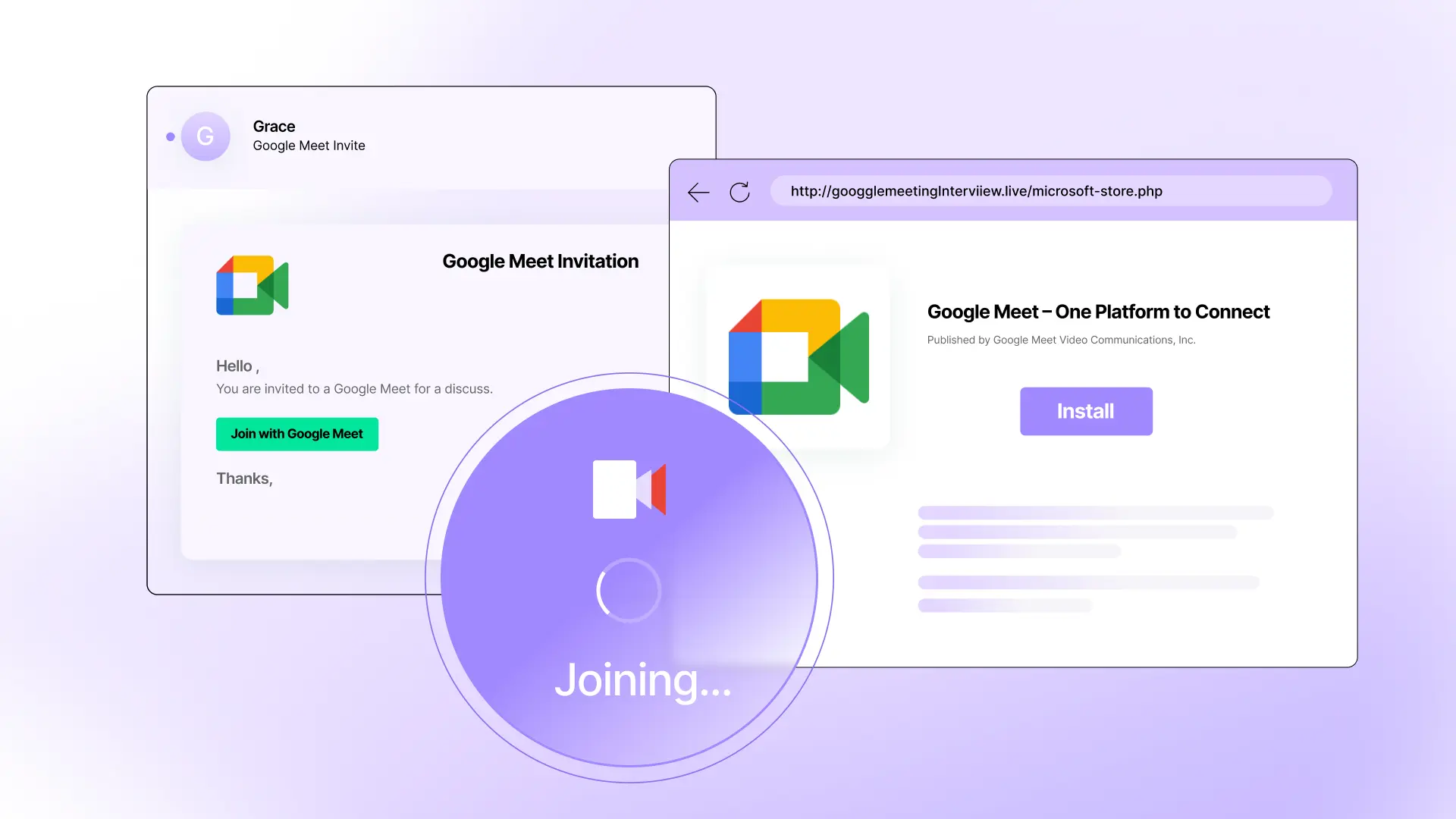
ASA is an AI Agent that acts as a Layer 1 / Layer 2 Analyst to deeply triage, investigate, and respond to suspicious messages and user reports end-to-end.

Built-in automation
Sublime’s Automations feature enables customizable actions and auto-review based on verdicts including Malicious, Graymail, Spam, and Phishing Simulations.

Flexible response
Quarantine, insert warning banners, alert, reply to user reports, and more based on verdict and confidence.
Orchestration
Sublime integrates with SOARs & SIEMs, ticketing systems, threat intelligence platforms, and more to automate workflows and enrich downstream systems.
Ready to transform your email security operations?
Experience how Sublime can reduce MTTR and streamline your threat response workflows.
Complete M-SOAR capabilities
Advanced features designed for modern security operations teams who need comprehensive email threat management.

Automated detection and response
Trigger immediate remediation actions when threats are detected automatically.
SIEM and SOAR integrations
Connect seamlessly with existing security orchestration platforms and workflows.

Flexible response actions
Quarantine, move to spam, insert warning banners, and more.

End-user behavior
Natively track opens, replies, and more to determine if further IR is needed.
Webhook and API connectivity
Integrate with ticketing systems and custom security workflows easily.

Historical threat investigation
Search, analyze, and remediate past attacks to improve future response.
Real-time alert management
Receive instant notifications when critical threats are detected.
Custom response playbooks
Build automated workflows tailored to your organization's security requirements.
What our customers are saying

The black box approach to email security no longer works.
It reduces visibility on how
Brex may be attacked and
the tactics and techniques
used by attackers.
With Sublime, we now have transparency and the confidence to keep up with emerging threats.

The ability to automate remediations with high confidence and minimize manual reviews unlocks a new level of efficiency in our SOC. It’s hard to imagine going back to life before Sublime.

What I love about the platform is that it just works. I’m so tired of all these tools I have to futz with, and Sublime is just easy.

With Sublime, we no longer wait weeks for vendor updates. Our team reacts instantly - which is critical for our fast-moving environment.
Latest from Sublime
Frequently asked questions
Now is the time.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)