Prevent email bomb attacks - the DDoS of email
Email bombs disable mailboxes and provide cover for machine and account takeovers. Sublime can prevent them from ever reaching an inbox.

.svg)
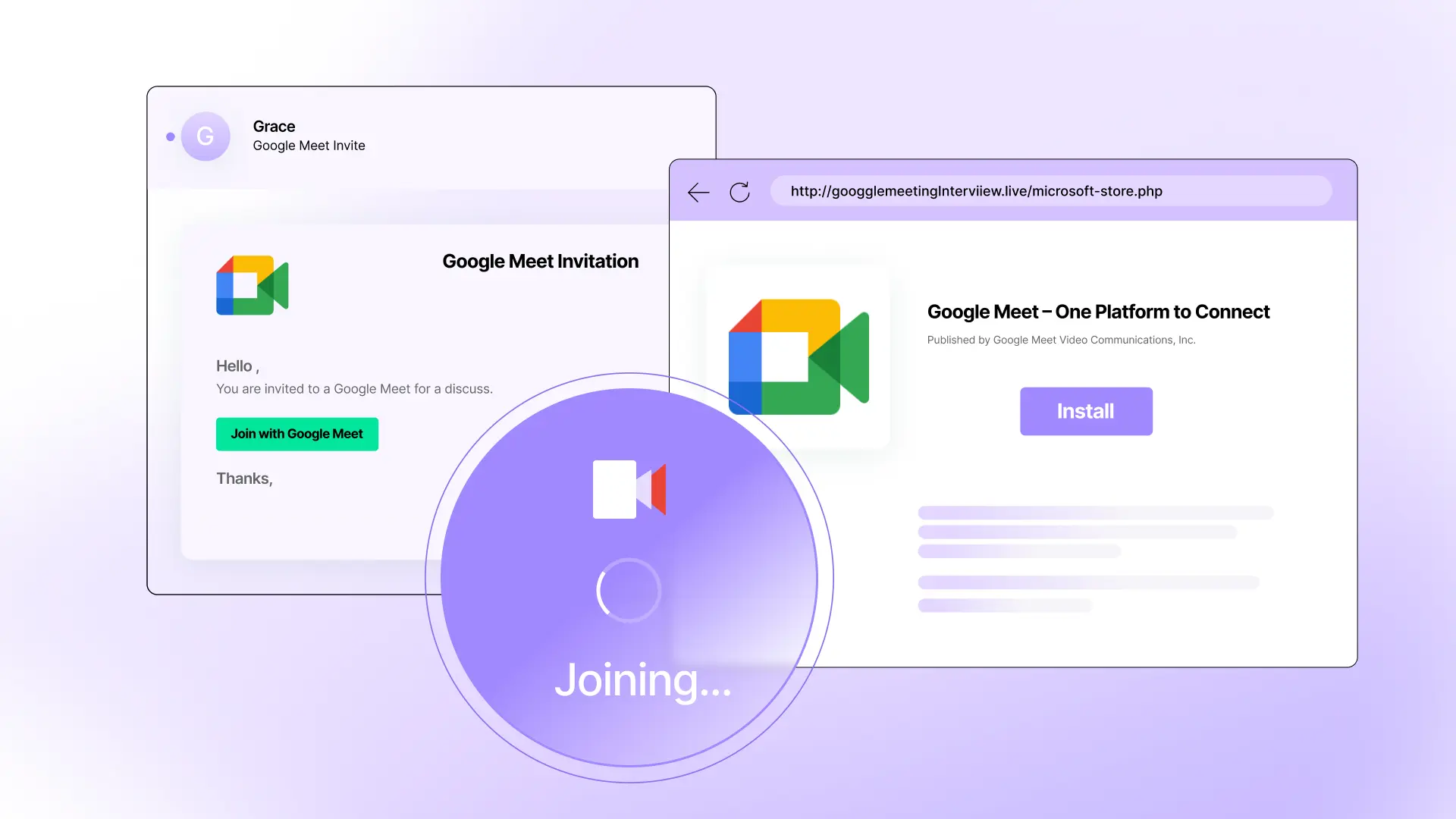
Our previous solution delivered a well-crafted phishing email to our technology team, but Sublime identified it as malicious immediately. That was our first 'oh yeah, Sublime is way better' moment.
Email bombs in a nutshell

Email bombs are the DDoS of email. They occur when an adversary uses an avalanche of email to overwhelm a mailbox, disrupt service, evade security, or more.
The barrage of messages in an email bomb creates a smokescreen of non-malicious messages to obscure the malicious intent or payload.
The sheer volume of an email bomb makes it difficult for security solutions to address each message individually.
Email bomb endgames
Adversaries can send email bomb attacks for a variety of reasons.

Disable mailboxes
Attackers can use email bombs to disable a target mailbox or make it otherwise unusable due to the volume of messages.

Machine takeover
Attackers will initiate an email bomb, call the target as “tech support” to “fix” the bomb, and then get the target to install a remote access tool.

Account takeovers
Attackers will initiate a password reset, use a bomb to hide the legit reset email, and then send a fake reset email that phishes credentials.
Email bomb prevention with Sublime
Sublime uses machine learning, message grouping, and bidirectional processing to detect and prevent email bombs and save teams time.
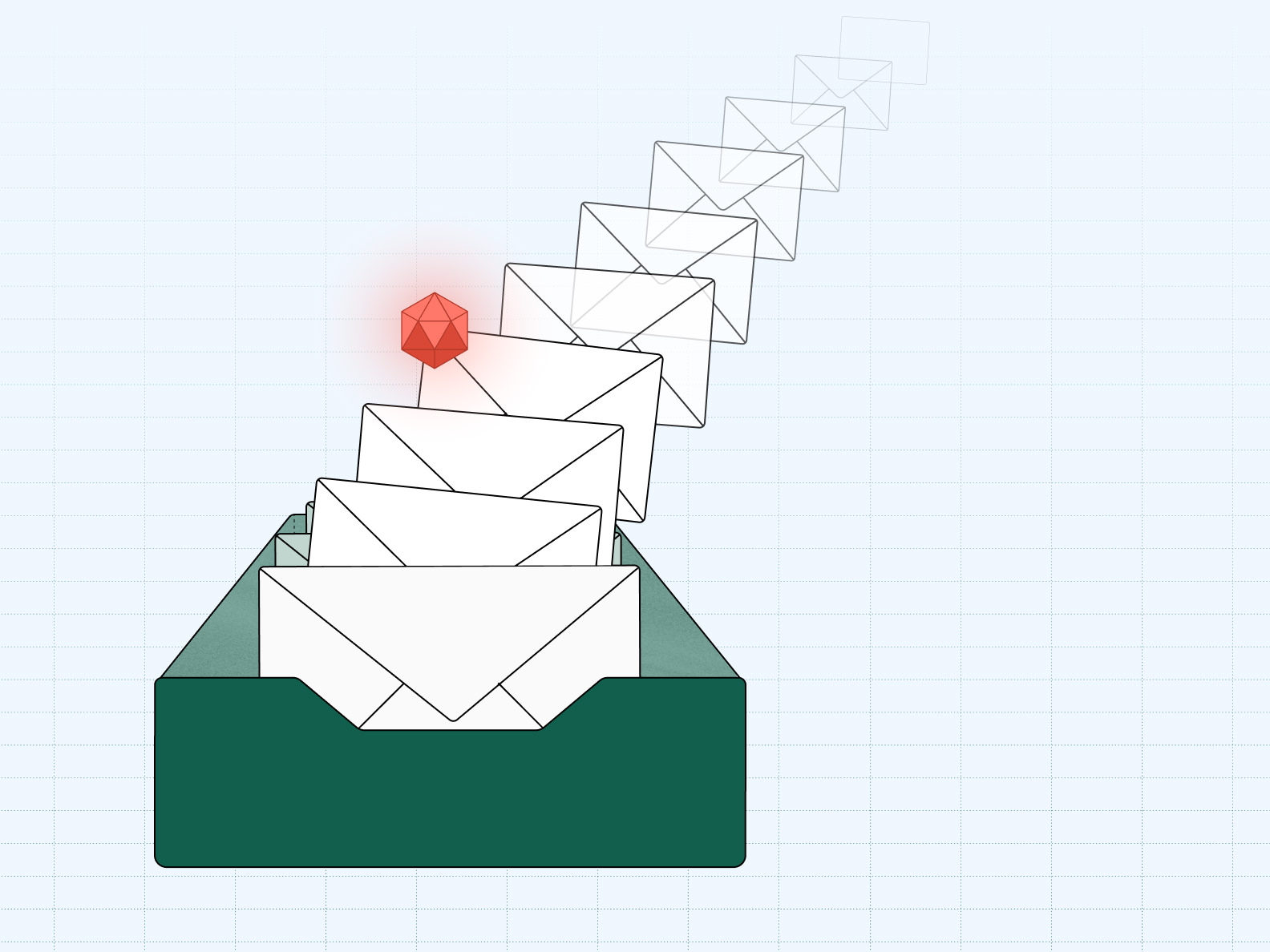
Email bomb detection
Sublime builds patterns of email volume and behavior for each mailbox at an organization. Once an email bomb spike reaches a mailbox-specific threshold, all the messages in the bomb are grouped and auto-remediated.
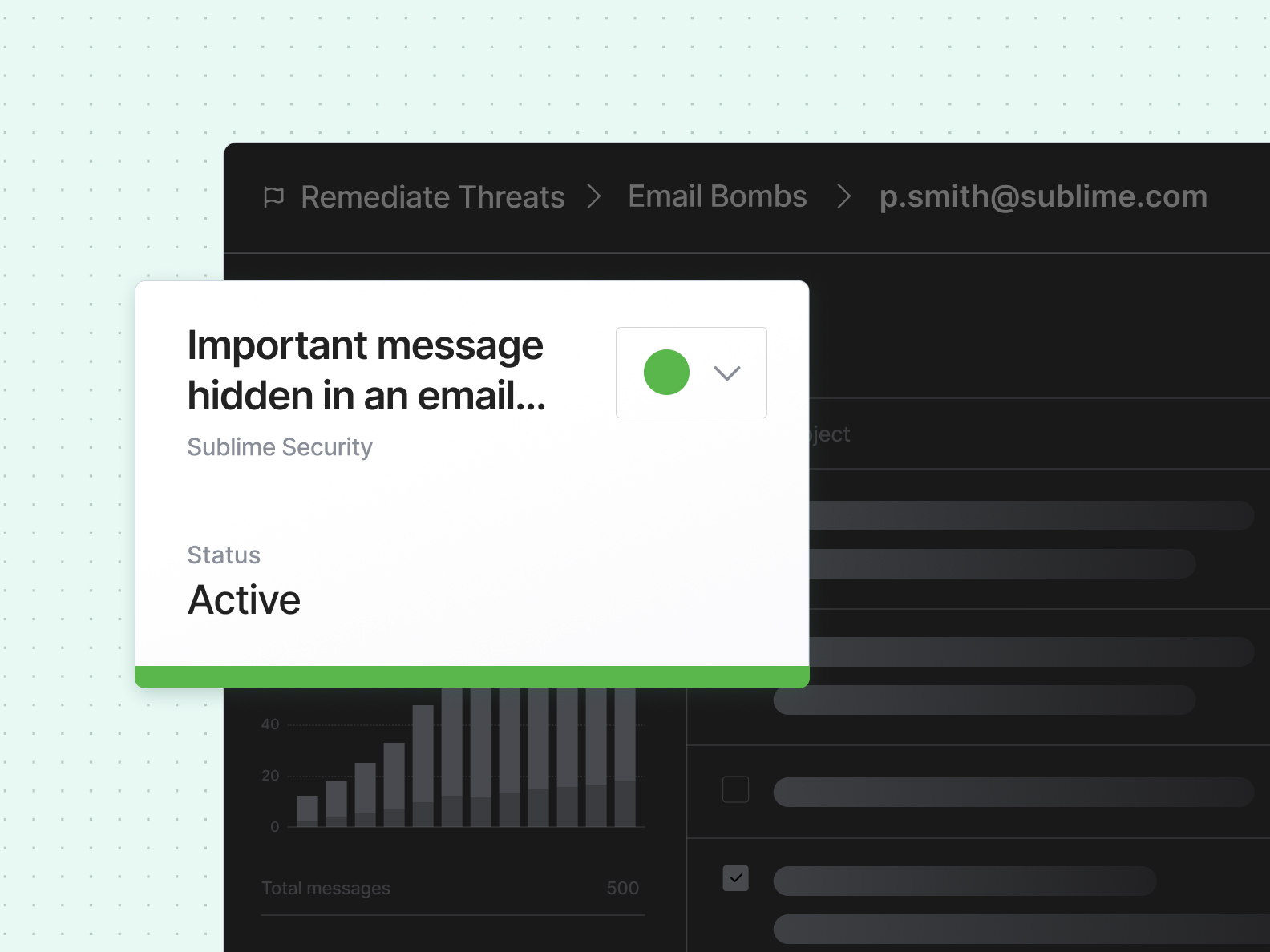
Auto-remediation & fast triage
Sublime auto-remediates messages in an email bomb and provides an intuitive interface for quickly triaging any outliers. Our interface includes in-depth details about the email bomb so security teams can move quickly and precisely.

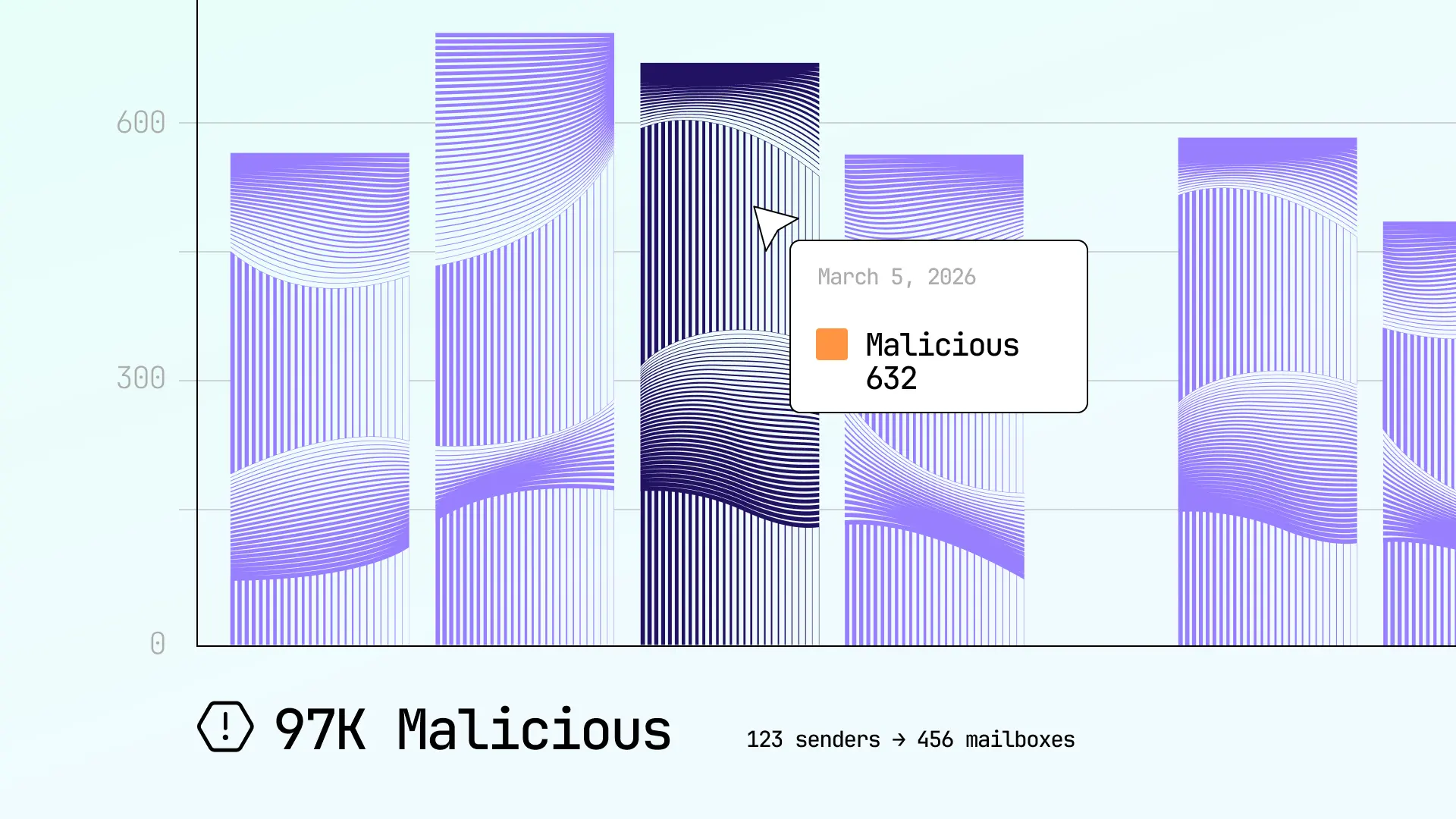
Email bomb overview
Security teams get a view of historical and ongoing email bombs, their status, and other important information.
.jpg)
Automated handling
For teams that want to go further, they can view and modify the Automation logic used to catch email bombs.
See how Sublime stops email bombs
Experience how our email security platform prevents email bombs.
Latest from Sublime
The latest news, research, attack spotlights, and product updates.
Frequently asked questions
Now is the time.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)