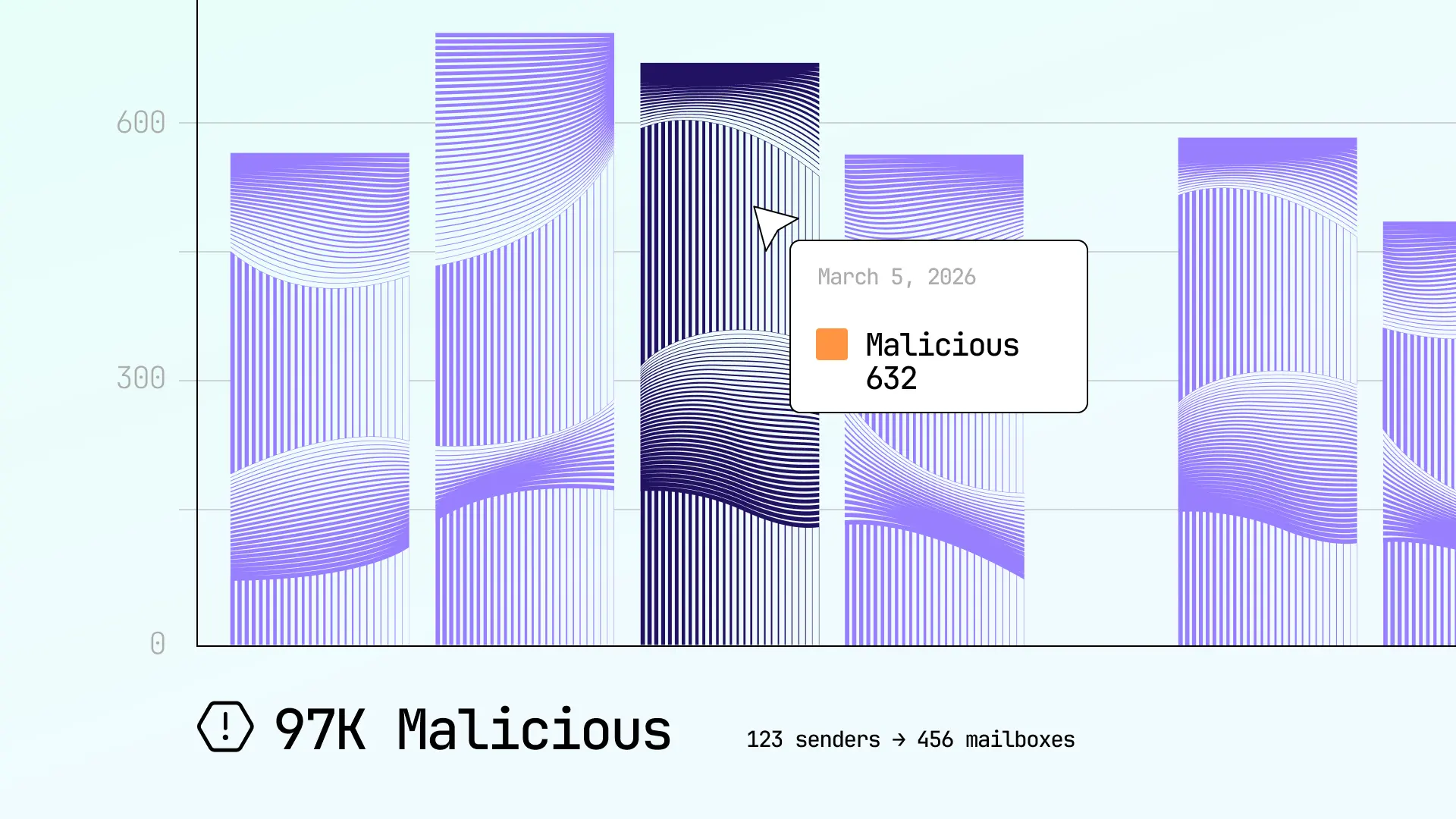
Hang up on callback phishing with Sublime
A single successful callback phishing attack opens the door for financial scams, ransomware, and more. Sublime's AI-powered callback phishing detection keeps callback phish out of inboxes and safely in quarantine.

.svg)
Our previous solution delivered a well-crafted phishing email to our technology team, but Sublime identified it as malicious immediately. That was our first 'oh yeah, Sublime is way better' moment.
Callback phishing in a nutshell

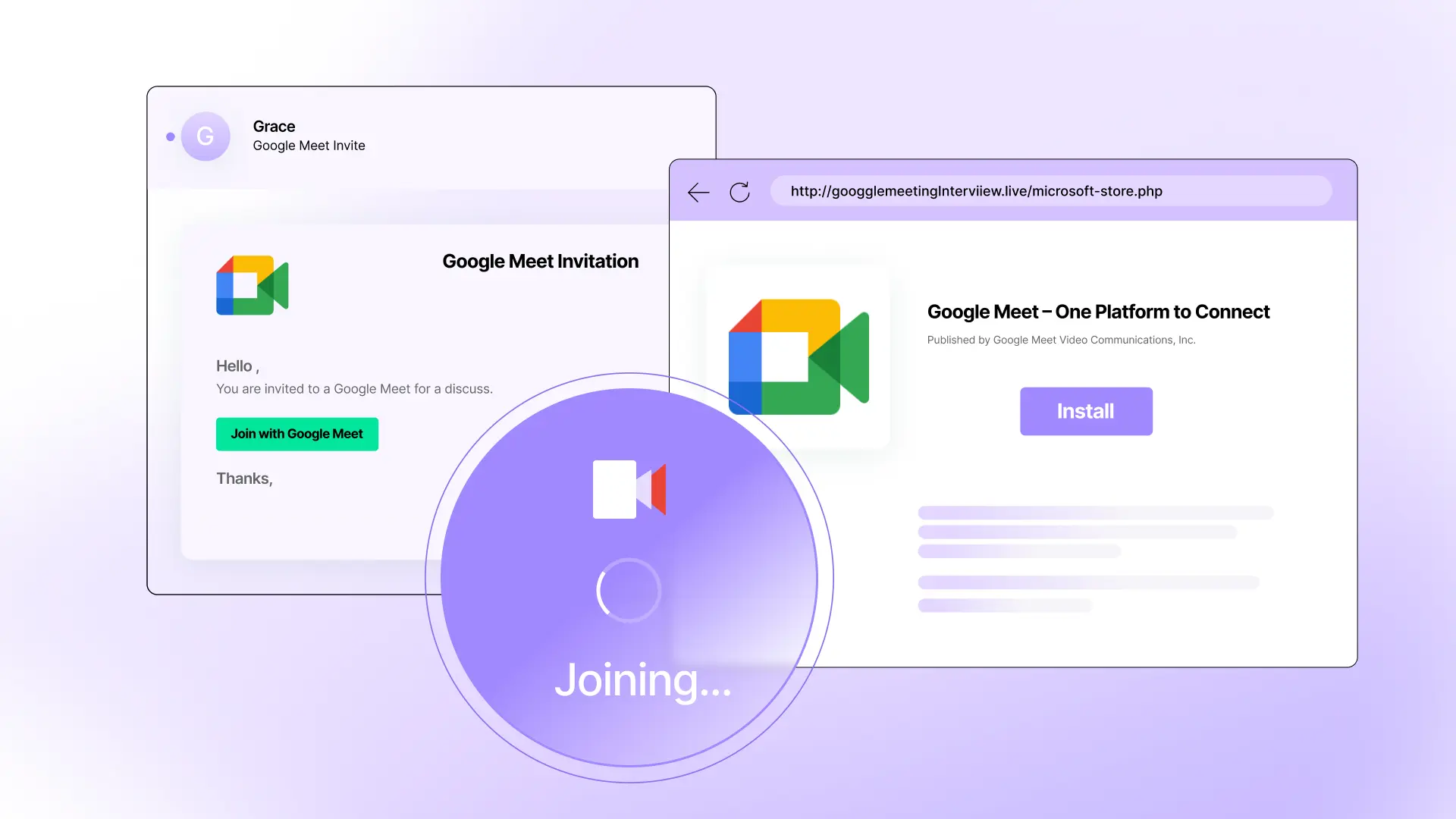
Callback phishing, or telephone-oriented attack delivery (TOAD), is an attack that usually begins with a fake invoice or receipt.
These attacks often appear to be a charge from a well-known company, and the goal is to get a target to call a number for assistance. Once on the phone, the attacker often poses as a customer service representative, asking for personal information, offers to help "cancel the charge," or convinces the target to install remote support software.
From there, they can access the device, steal sensitive data, or walk a target through a fake refund process that results in real financial loss.
What makes callback phishing so slippery
Callback phishing attacks can be difficult to catch when security tools are looking for some of the traditional indicators of attacks.

Linkless legitimacy
Callback phishing attacks don't have a traditional malicious URL or payload, requiring specialized scanning to detect.

Embedded callbacks
To further evade security tools, adversaries will often put the callback information in embedded images, so as not to be picked up by body text analysis.

Attacks in attachments
Attackers will put callback information within attachments, sometimes nested within archives, to make it easy for humans to find but difficult to detect.
Tools for catching callback phishing
Callback phishing can be difficult for most security platforms, but Sublime uses a layered combination of AI, machine learning, and org-specific detections to catch the phish.
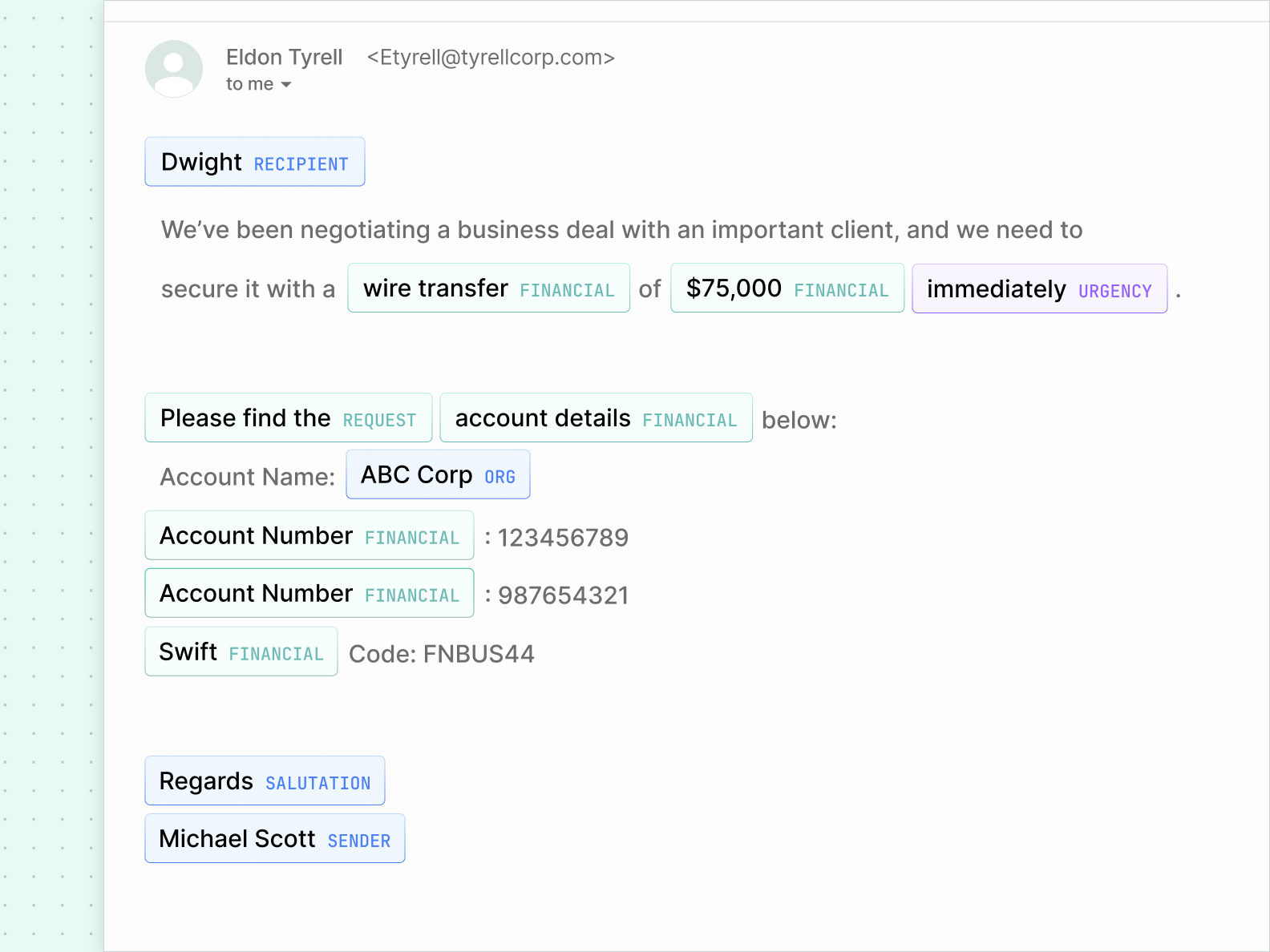
Intent analysis
Sublime uses Natural Language Understanding (NLU) to understand the intent of a message. By comparing the intent with the data and metadata of an email, callback phish quickly come into focus.

Computer vision
Sublime takes a screenshot of messages and attachments and looks for brand logos, QR codes, and runs it through Optical Character Recognition (OCR). These analyses let us catch brand impersonations and text embedded as images to avoid body scanning – common evasions for attackers.
Attachment analysis
Sublime analyzes attachments and images with OCR and intent analysis the same way it analyzes the email body. This includes recursive analysis of archives, scanning all files within regardless of depth.
Advanced callback phishing detection for your organization
See how Sublime's comprehensive callback phishing platform can safeguard your business from callback phishing attacks.
Latest on callback phishing
The latest news, research, and attack spotlights about callback phishing.
Frequently asked questions
Now is the time.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)