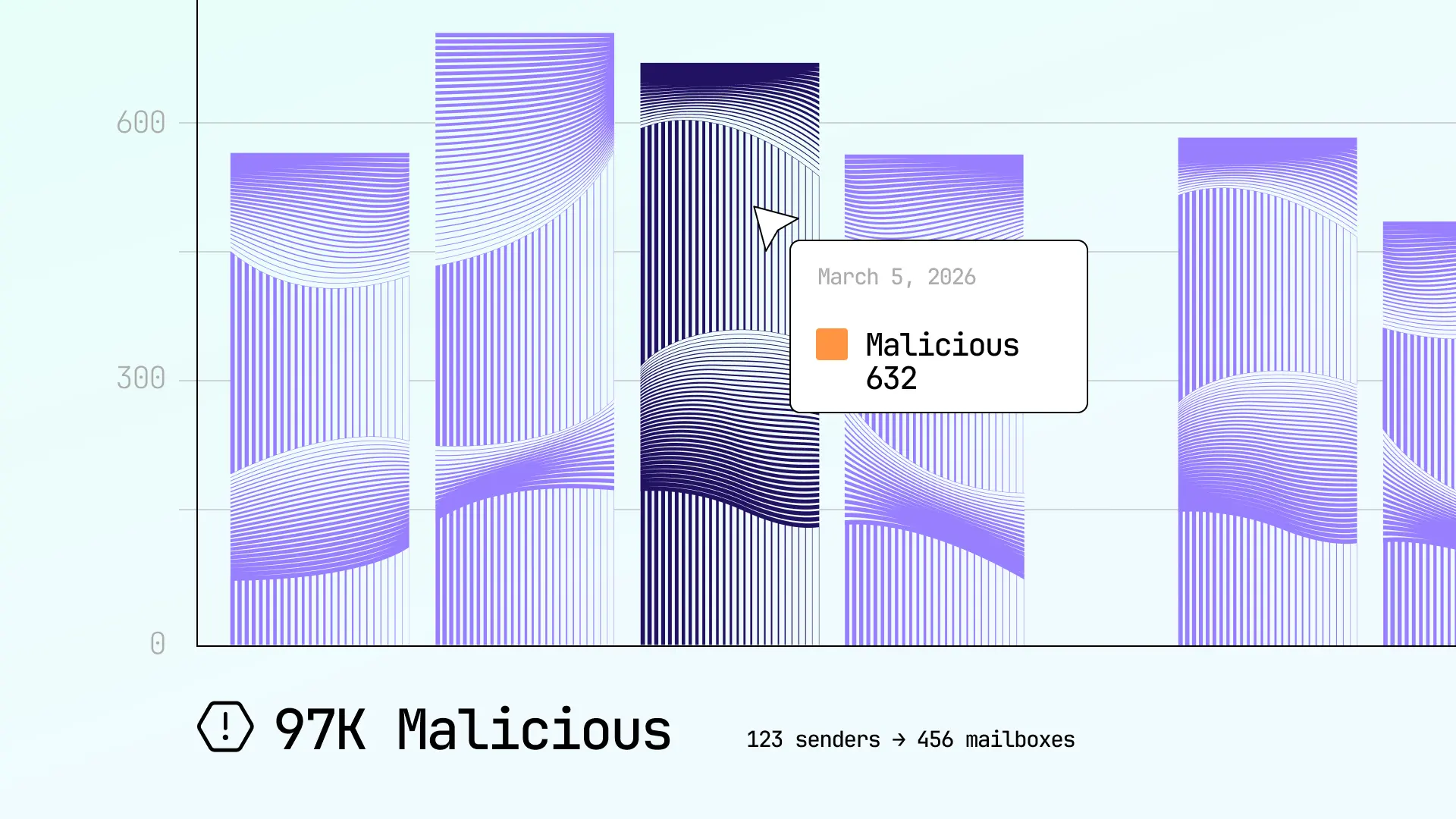
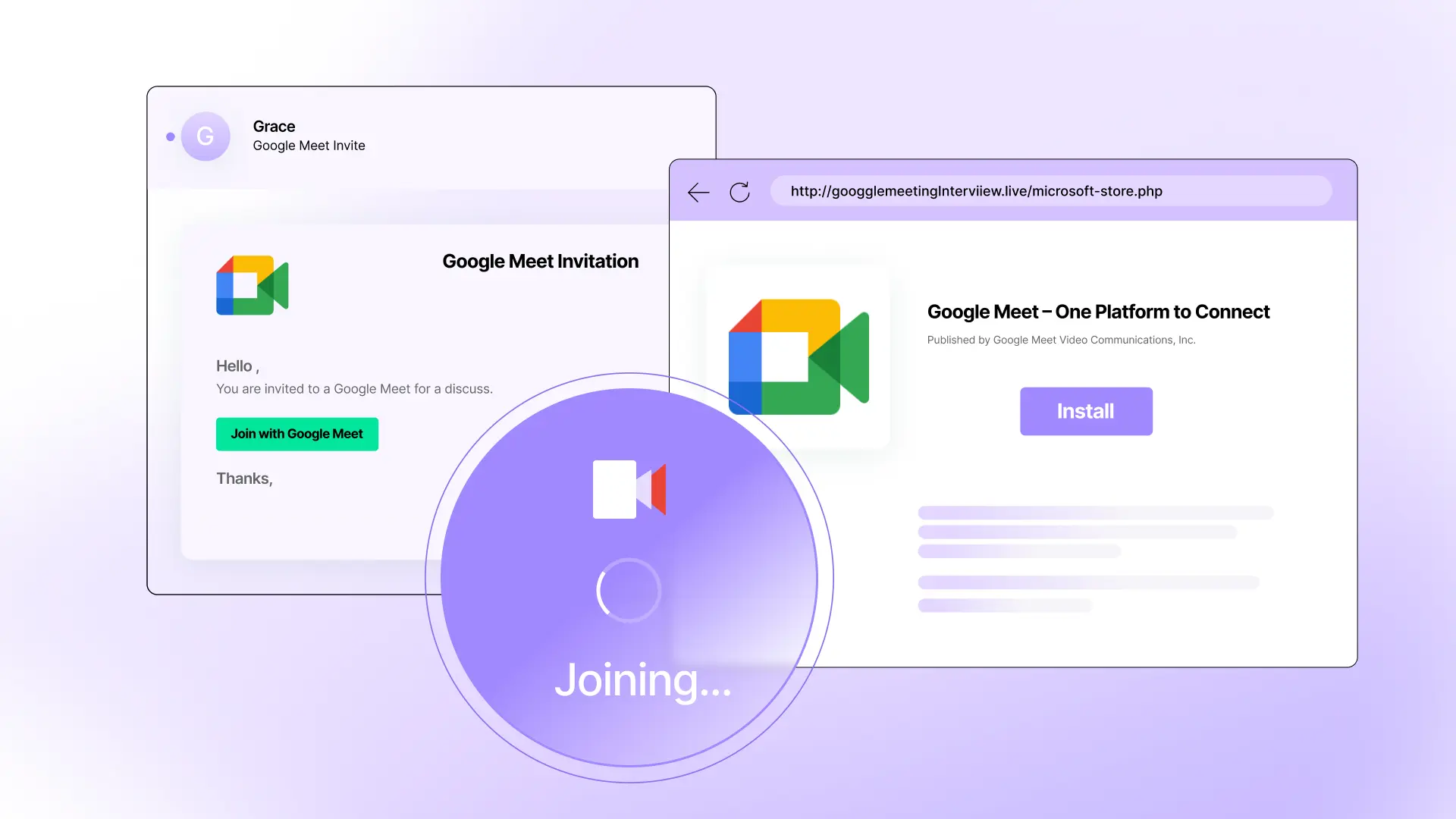
Don’t compromise on BEC and fraud protection
Organizations lose billions to BEC and fraud attacks every year. Sublime's AI-powered BEC coverage can detect and prevent these deceptive attacks.

.svg)
Sublime's platform was the only one that consistently identified the sophisticated social-engineering attacks that others missed. It passed every scenario we built.
BEC/fraud in a nutshell

Business email compromise (BEC) and fraud attacks rely on deception, impersonation, and social engineering to trick targets into sharing sensitive information or transferring funds.
These attacks can bypass traditional security tools because the emails often seem harmless, with initial messages often used to collect information for a complex operation.
Fake invoices, manufactured threads, urgent wire transfers, payment updates, and more are used to start a conversation that can lead to wire fraud, compliance violations, and damage to an organization's reputation.
What makes BEC/fraud attacks so effective
BEC attacks play the long game. There isn't a link to click or a file to download, just a conversation that leads to a socially engineered fraud.

GenAI
With LLMs, attackers can create, deliver, and iterate on attacks at a speed and scale beyond traditional security.

Impersonation
BEC attacks will often impersonate trusted people or institutions, leveraging trust to start the attack.

Manipulation
Attackers will use coercion, urgency, and other methods of manipulation to provoke engagement.

Multiple stages
BEC attacks can start with recon and artifact gathering, helping adversaries build out fake threads and narratives.
Tools for keeping BEC/fraud out of inboxes
BEC and fraud attacks can be difficult for security platforms to detect and prevent, but Sublime uses a layered combination of AI, machine learning, and org-specific detections to catch these threats.
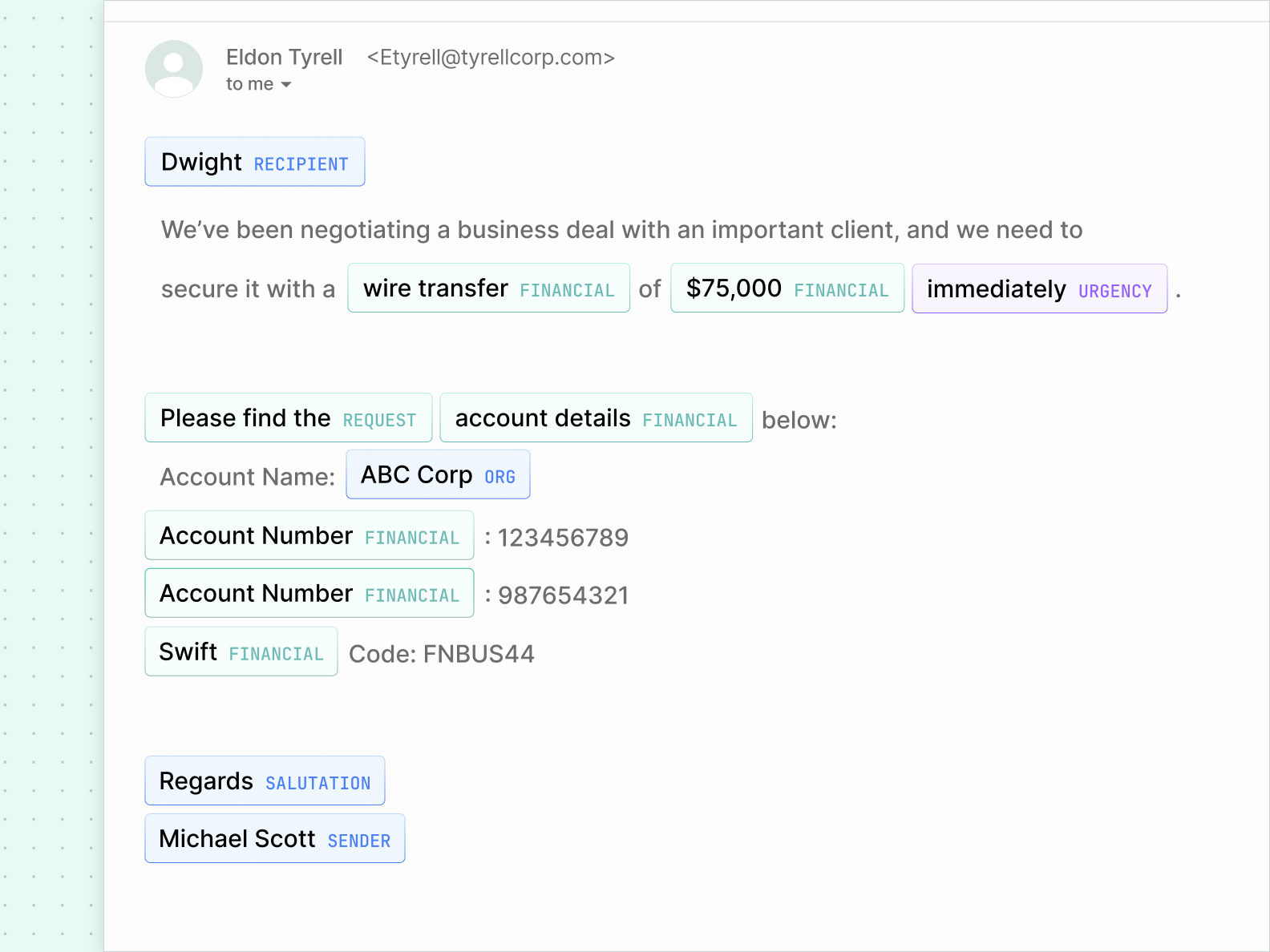
Natural Language Understanding
Sublime's BEC protection uses Natural Language Understanding (NLU) to understand the intent of a message. By comparing the intent with the data and metadata of an email, Sublime can develop a picture of fraud from hundreds of small signals.
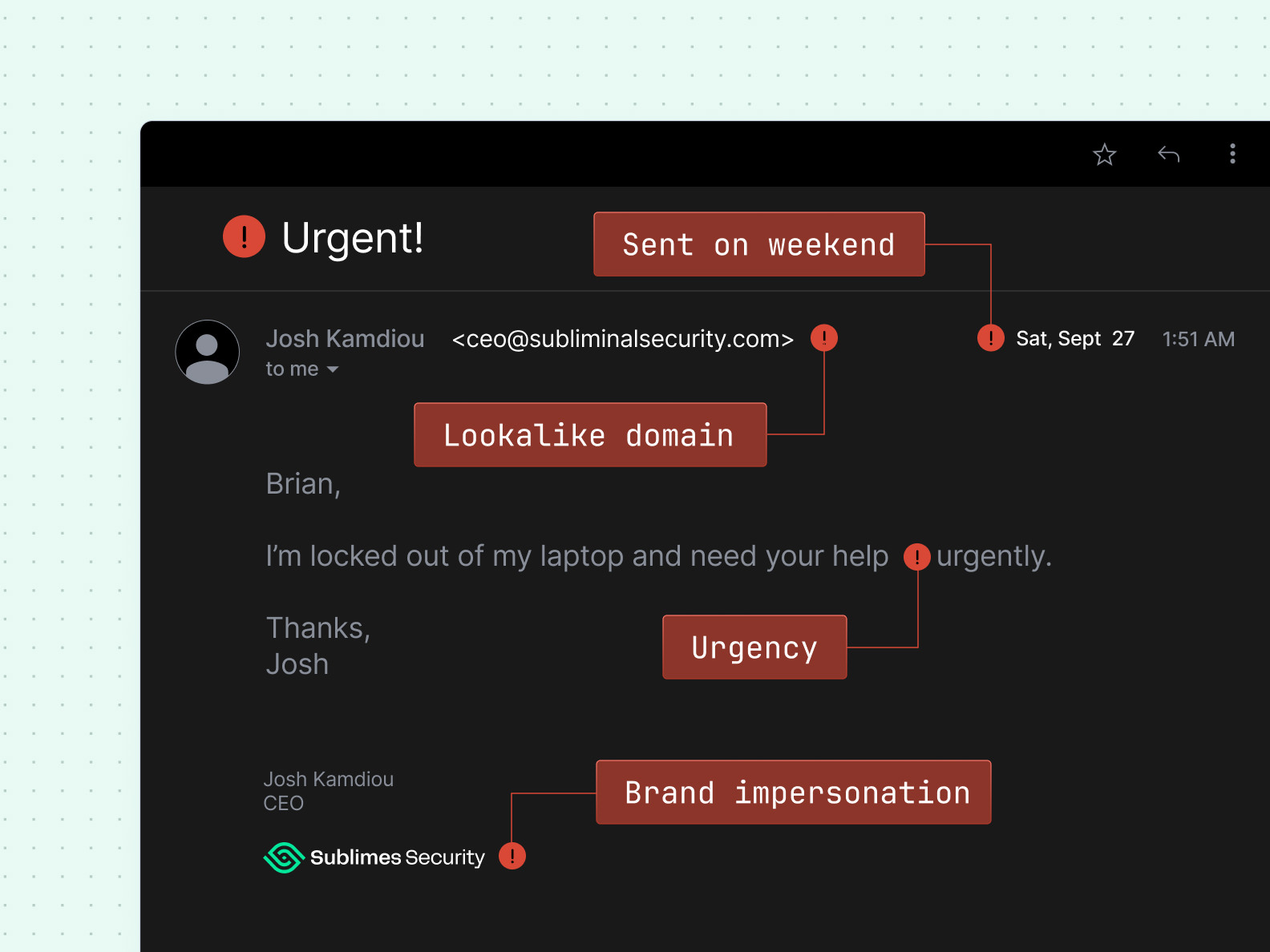
Impersonation detection
Sublime's business email compromise detection leverages a variety of org-specific signals, such as known VIPs, that can be used in comparative analysis against sender data. This includes domain lookalike identification, misspelling-based evasion detection via Levenshtein distance, and more.
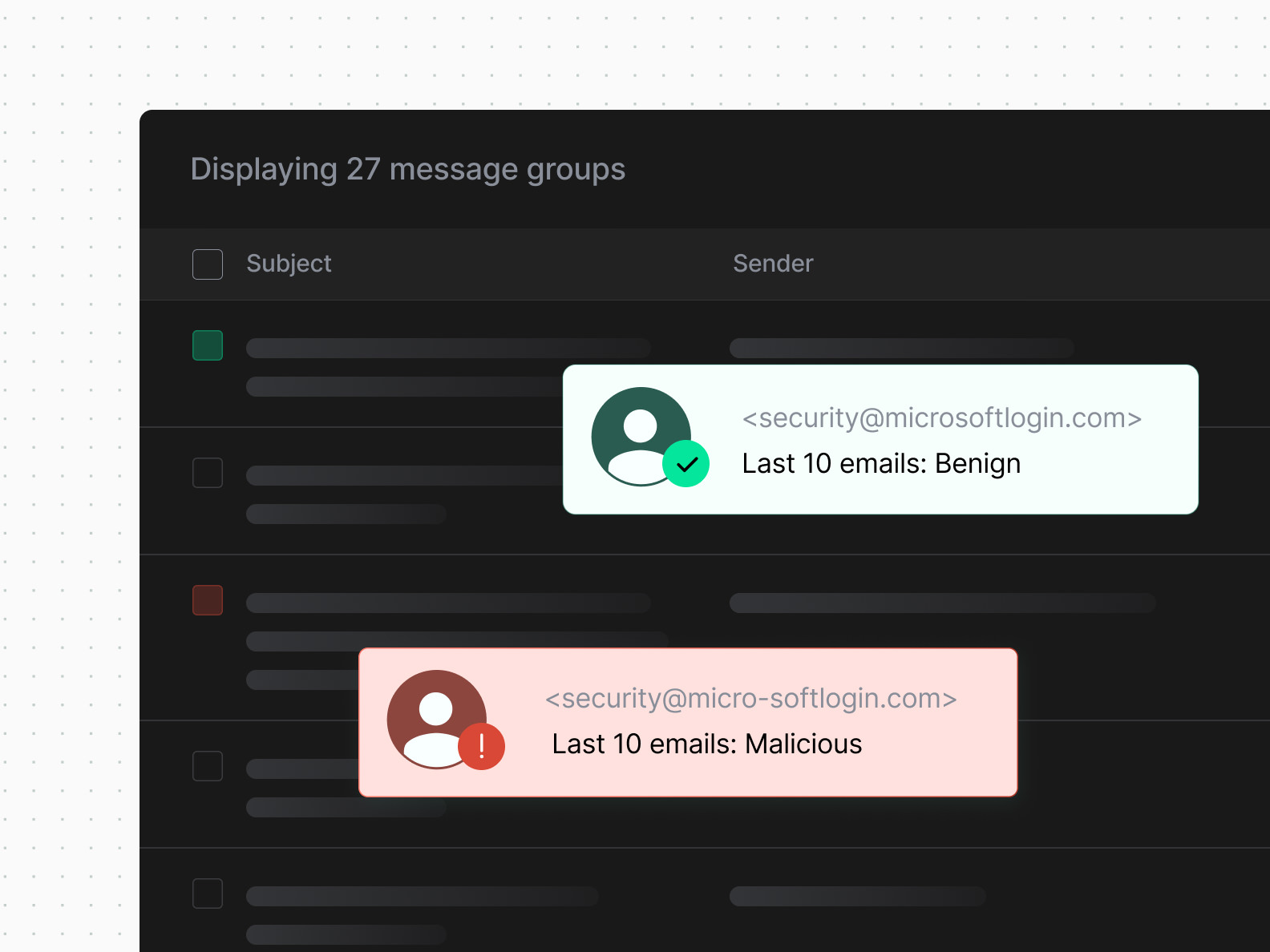
Sender metadata
Sublime's BEC protection uses sender behavior, WHOIS registration data, and more to determine the trustworthiness of a message.

Authentication results
Sublime analyzes DKIM, DMARC, and SPF status of an email to clearly indicate if a sender has been spoofed rather than compromised.
Advanced BEC protection for your organization
See how Sublime's comprehensive business email compromise software can safeguard your business from BEC and fraud attacks.
Latest on BEC/fraud attacks
The latest news, research, and attack spotlights about BEC/fraud attacks.
Frequently asked questions
Now is the time.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)