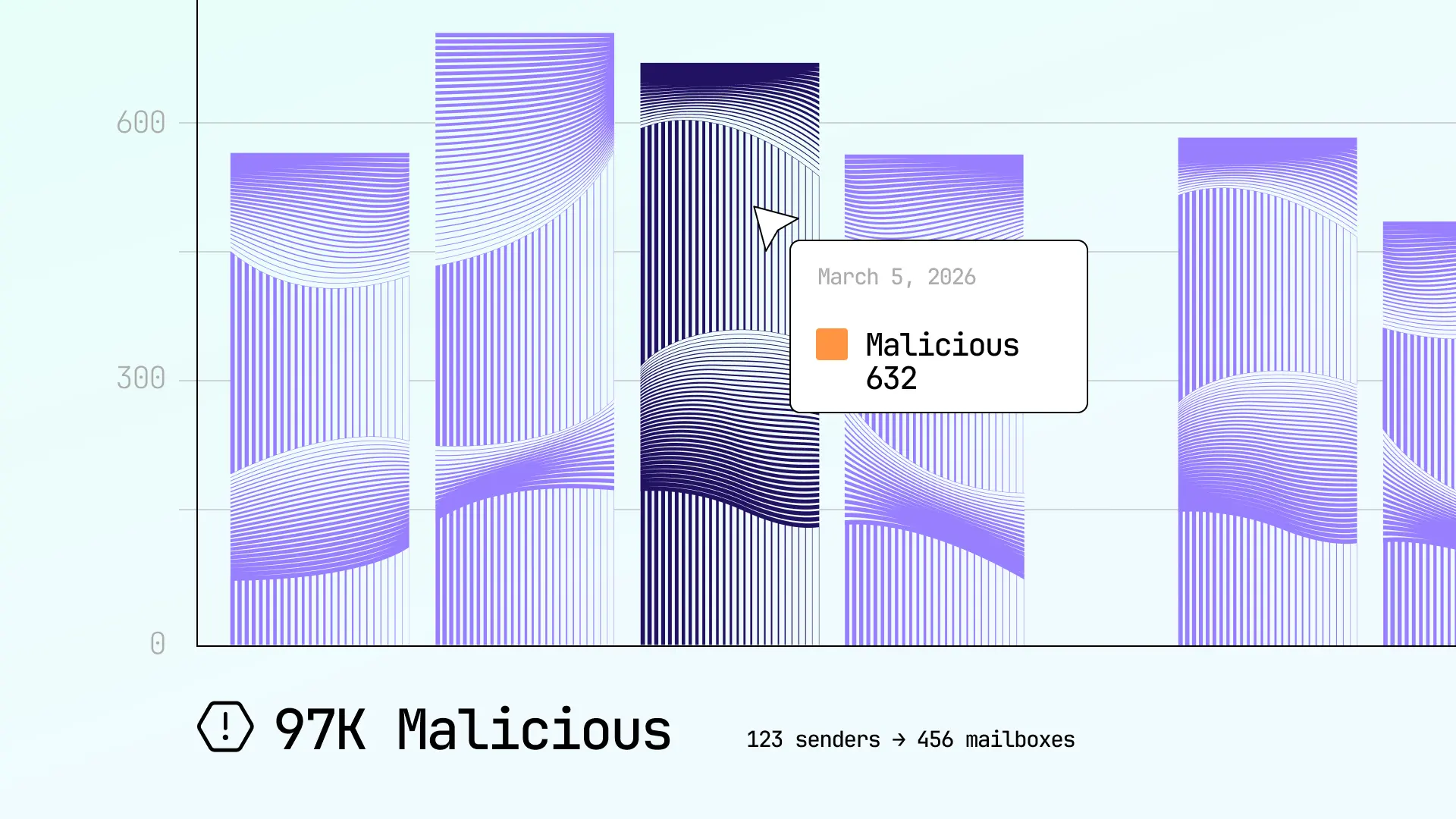
Shut down credential phishing with Sublime
A single successful credential phishing attack opens the door for financial scams, data exfiltration, and more. Sublime's AI-powered adaptive email security keeps credential phishing out of inboxes and safely in quarantine.

.svg)
Our previous solution delivered a well-crafted phishing email to our technology team, but Sublime identified it as malicious immediately. That was our first 'oh yeah, Sublime is way better' moment.
Credential phishing in a nutshell

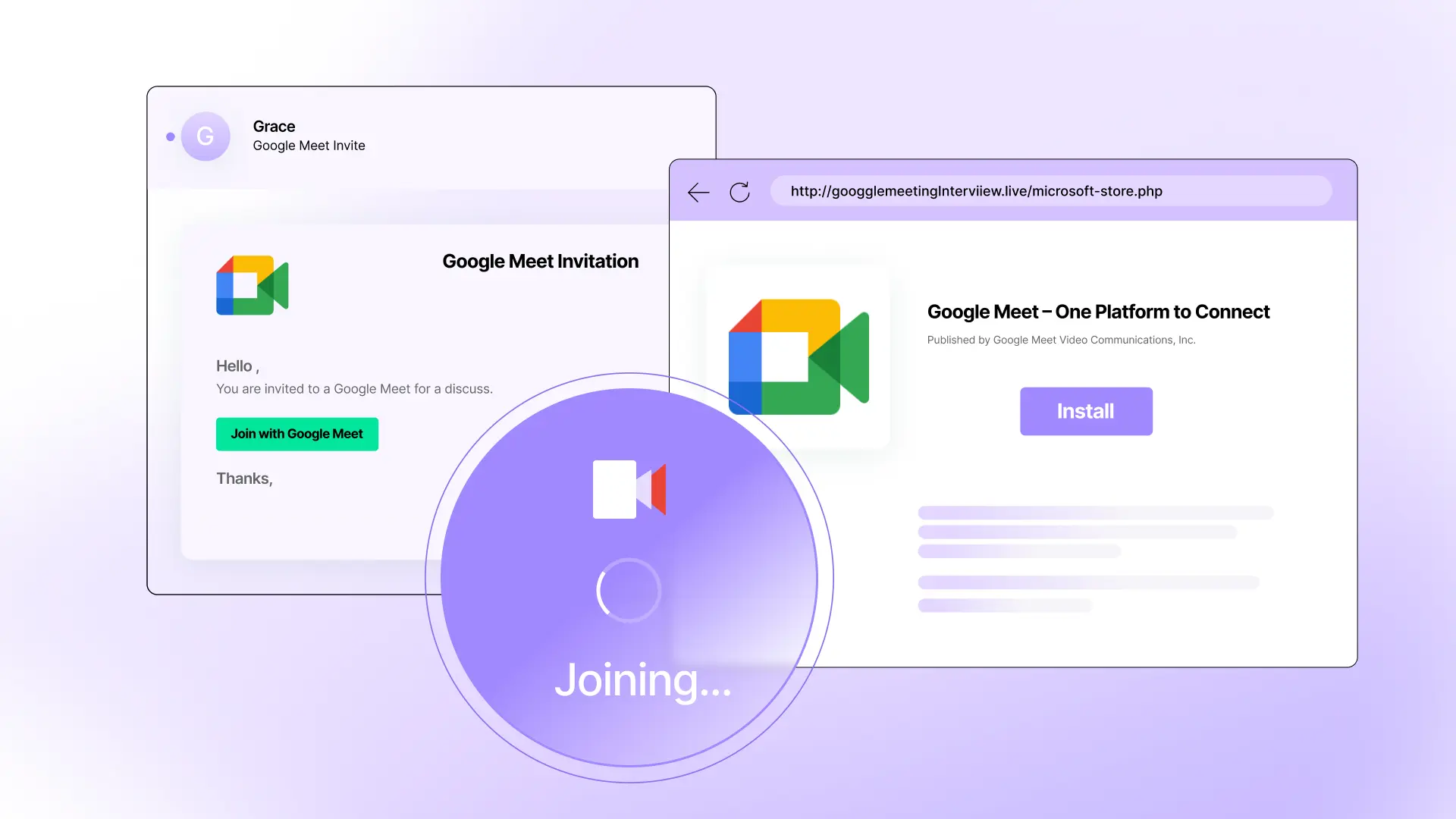
Credential phishing attacks are designed to steal login information with fake login pages.
These emails impersonate trusted services and use urgent language to lead targets to a convincing, fake login page.
If credentials are entered, the attacker captures them immediately. The damage doesn't stop at just stealing logins. Once attackers gain access, they can move through an organization, steal sensitive data, send internal phishing emails, or more.
What makes credential phishing so effective
Credential phishing can be difficult to catch when emails appear authentic and malicious links lead to legitimate looking login pages.

Expert impersonation
Credential phishing attacks will clone real notification emails and login pages in order to create authenticity and improve click rates.
.svg)
Adversary in the middle
Credential phishing attacks can leverage AITM techniques, passing login info from their fake page to a real auth service to bypass suspicion and MFA.

Rapid iteration
Attackers will use phishing kits to rapidly deliver, iterate, and vary attacks, allowing them to learn what techniques get them past security and into inboxes.
Tools to protect against credential phishing
Sublime uses a layered combination of AI, machine learning, and org-specific detections to catch the credential phishing attacks.
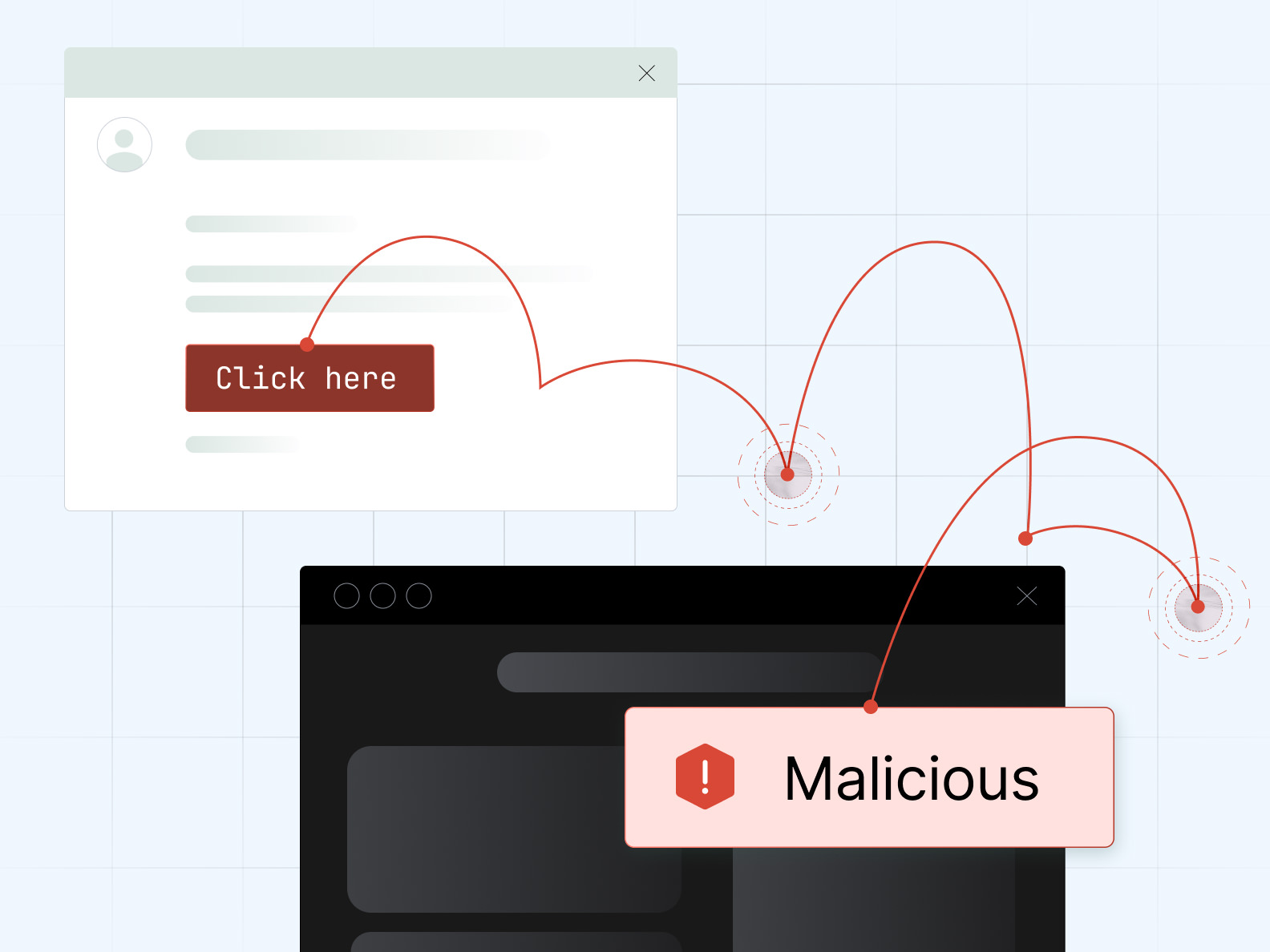
Link analysis
Sublime uses a browser emulation sandbox and machine learning to follow links through redirects to resolve the effective URL and collect a screenshot for further analysis.

Computer vision
Sublime uses computer vision to detect logos, identify CAPTCHAs, and recognize login forms. When combined with other suspicious signals, credential stealing phishing messages go straight to quarantine.
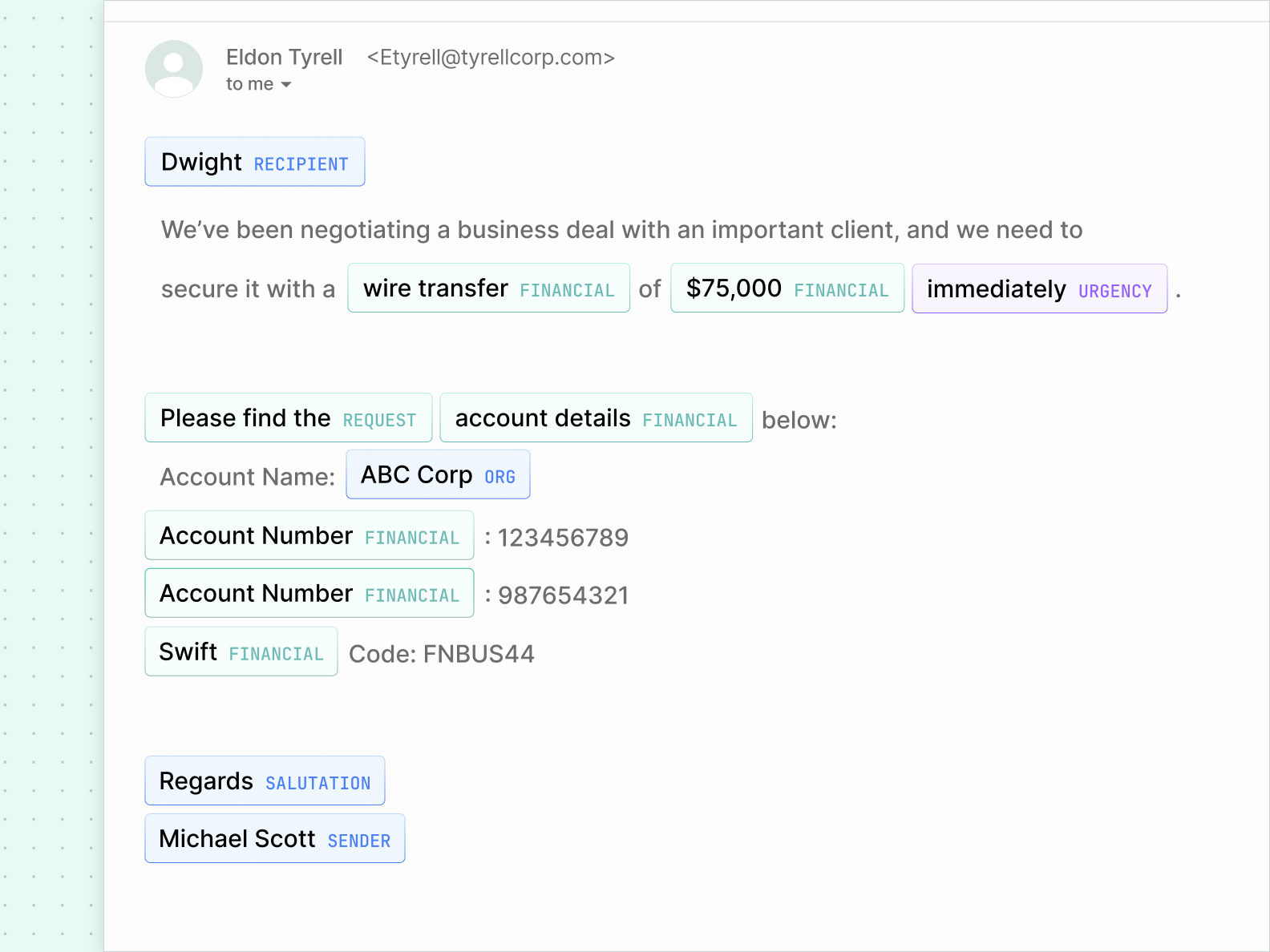
Intent analysis
Sublime uses Natural Language Understanding (NLU) to understand the intent behind a message. By comparing the intent with the context of an email, credential phishing quickly comes into focus.
Advanced credential phishing protection for your organization
See how Sublime's comprehensive platform can safeguard your business from credential phishing campaigns and similar threats.
Latest on credential phishing
The latest news, research, and attack spotlights about credential phishing.
Frequently asked questions
Now is the time.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)