July 24, 2025
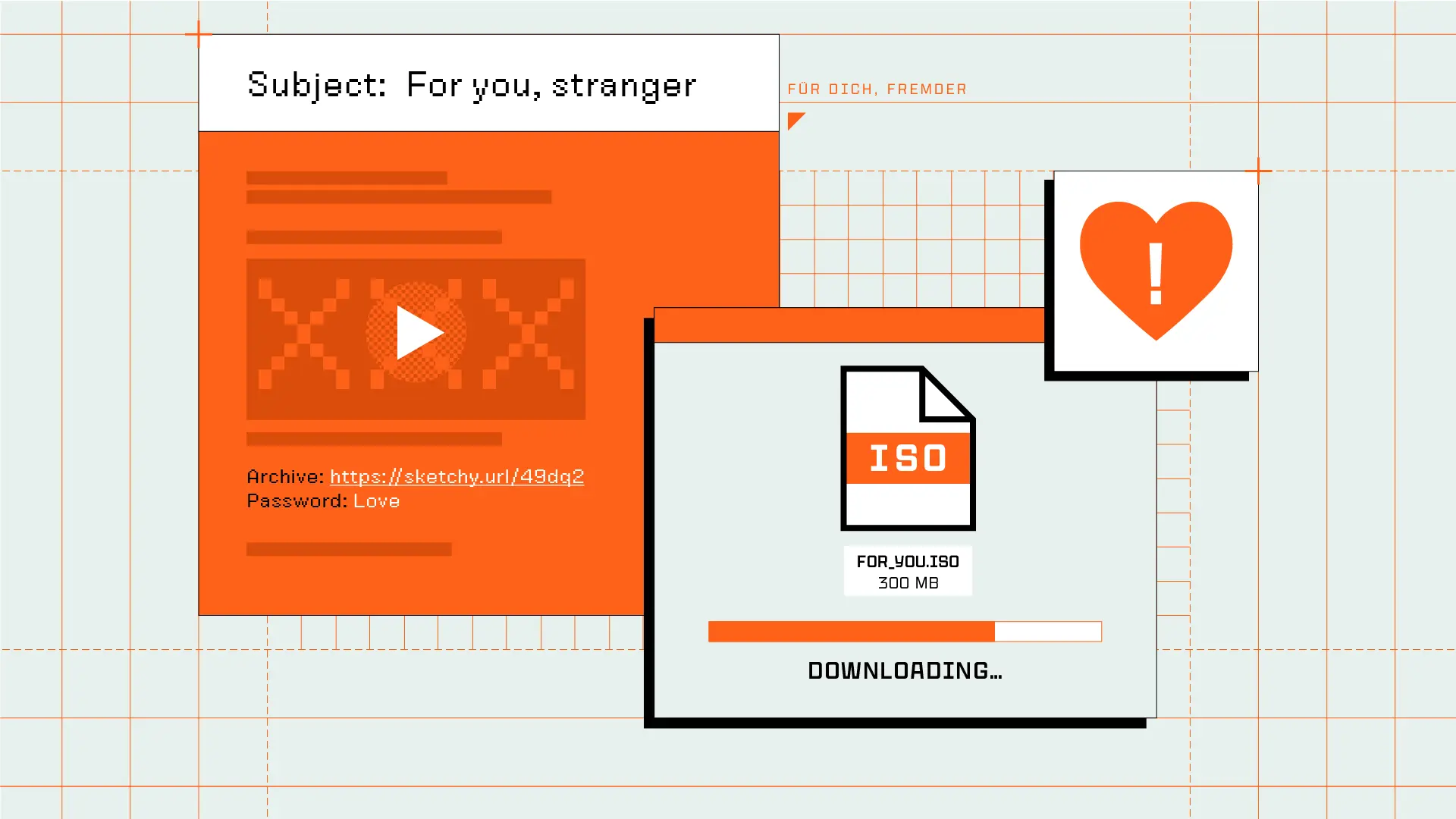
Malicious AutoIT payload hidden as explicit content delivered with anti-analysis tactics over a commercial TDS
Sublime recently identified an attack campaign targeting German speakers with a romance/adult-themed scam. The attack emails used explicit language, conflicting identity details, and redirects to malicious domains using a commercial Traffic Distribution Service (TDS) named Keitaro TDS to deliver a malicious payload. Here’s what one of the messages looked like:
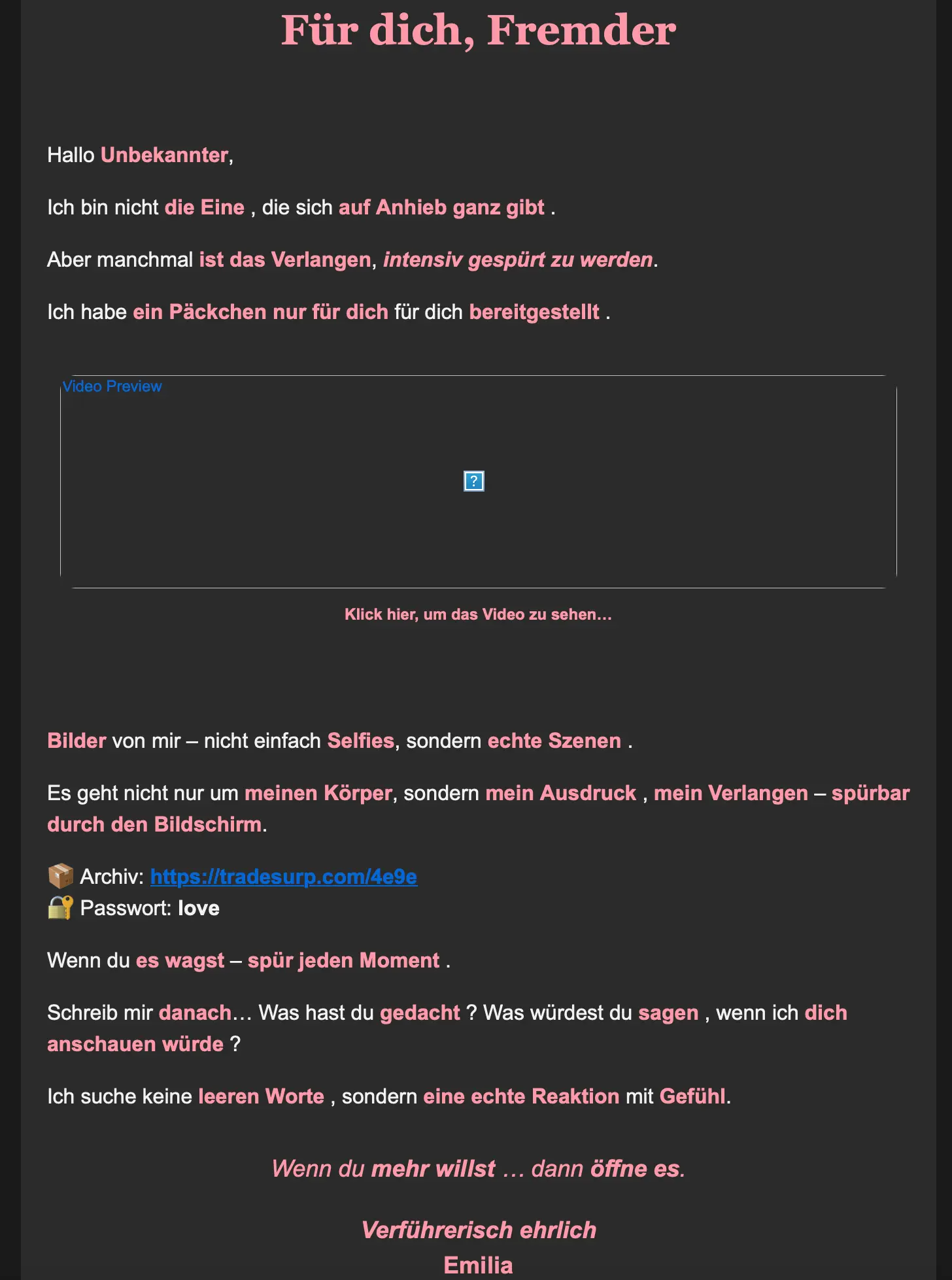
These emails contain two malicious URLs. The first link is on the video preview image embedded in the message. In the above instance, it is to a suspicious MP4 file hosted at https://files.catbox[.]moe. At the time of the analysis, both the MP4 and the JPG preview image were unavailable.
Further down, there is a malicious link to an “archive” hosted at https[:]//tradesurp[.]com/4e9e. We have seen different domains used to deliver the payload.
If clicked, this link will first determine if the victim is from a German locale. Then, using information encoded in a Keitaro TDS configuration, a malicious payload is downloaded in the background: a 300MB ISO file delivered from a Russia-based host.
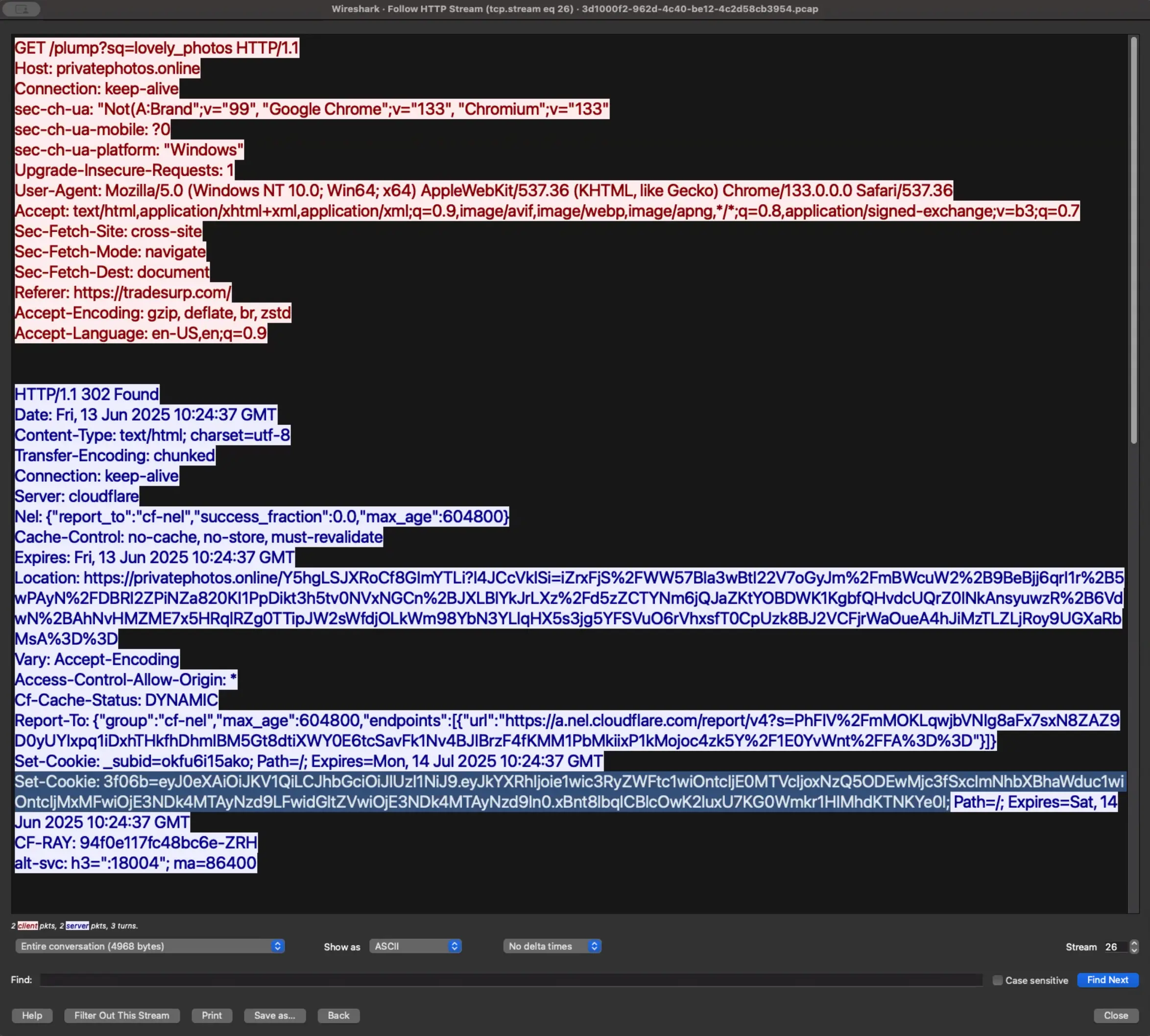
While the malicious ISO payload downloads in the background, a separate connection to https://privatephotos[.]online/plump?sq=lovely_photos triggers a content review by a TDS. When reviewing the HTTP network traffic to the TDS we can try to determine any specific service being run on the remote server, even if just for common redirects.
Sublime was able to confirm the use of Keitaro TDS by the use of the cookies it creates. The Set-Cookie value highlighted below shows a block of Base64 encoded data set to a variable named 3f06b. This is a notable indicator of Keitaro TDS, a known platform used for advertisement tracking.
As a TDS, Keitaro is able to view many characteristics of the computer making the request and provide connection paths. For example, any computer accessing a page from a specific set of countries or in a specific time range could be redirected to a unique page. On the flip side, a TDS like Keitaro can be used extensively by threat actors to create complex campaigns that only allow targeted victims, such as only allowing connections from Germany during its standard work hours.
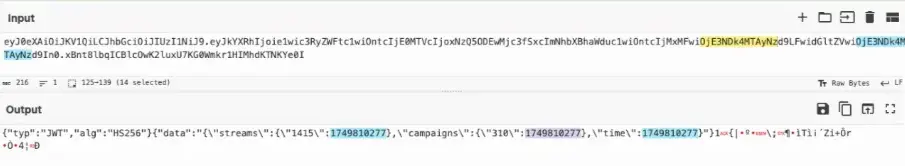
We can identify the campaign associated with the TDS by decoding the Base64 value to a configuration structure.
The delivered ISO container uses a known counter analysis technique where it increases its file size to an arbitrary large amount that is too large for analysis by most security platforms. When removing the excess junk data, the remainder is a standard container that can be mounted to the system as a drive image for files. This is the metadata of the ISO:
The ISO file, once mounted contain another 300MB executable and a text document that contains the password to the self extracting archive. Upon execution, lovely_photos.exe will prompt the user to enter a password. Upon entering the password (contained in both the original email and in the extracted Pass.txt), the program will begin extracting and executing multiple files.
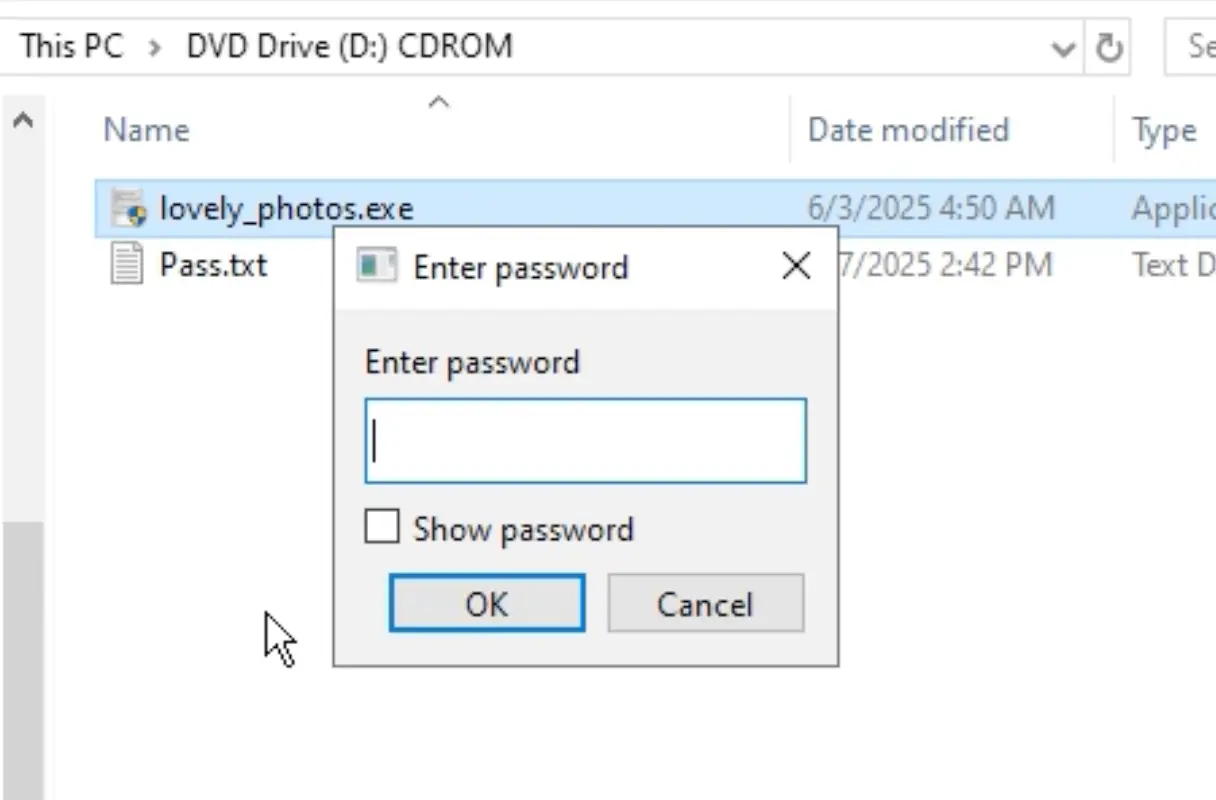
During extraction, the program will create multiple explicit images (.png or .jpg) with an IMG<4 digit number> naming structure. It will also drop many additional files to the current user’s Temporary file directory (%LocalAppData%). The first file in use is a batch script that is renamed from Burden.mil.
This batch script uses variable obfuscation and junk data, assigning meaningless and confusing variables to names. It also contains a unique logic branch that sets the name of the dropped files and how they execute. A portion of this code is shown below.
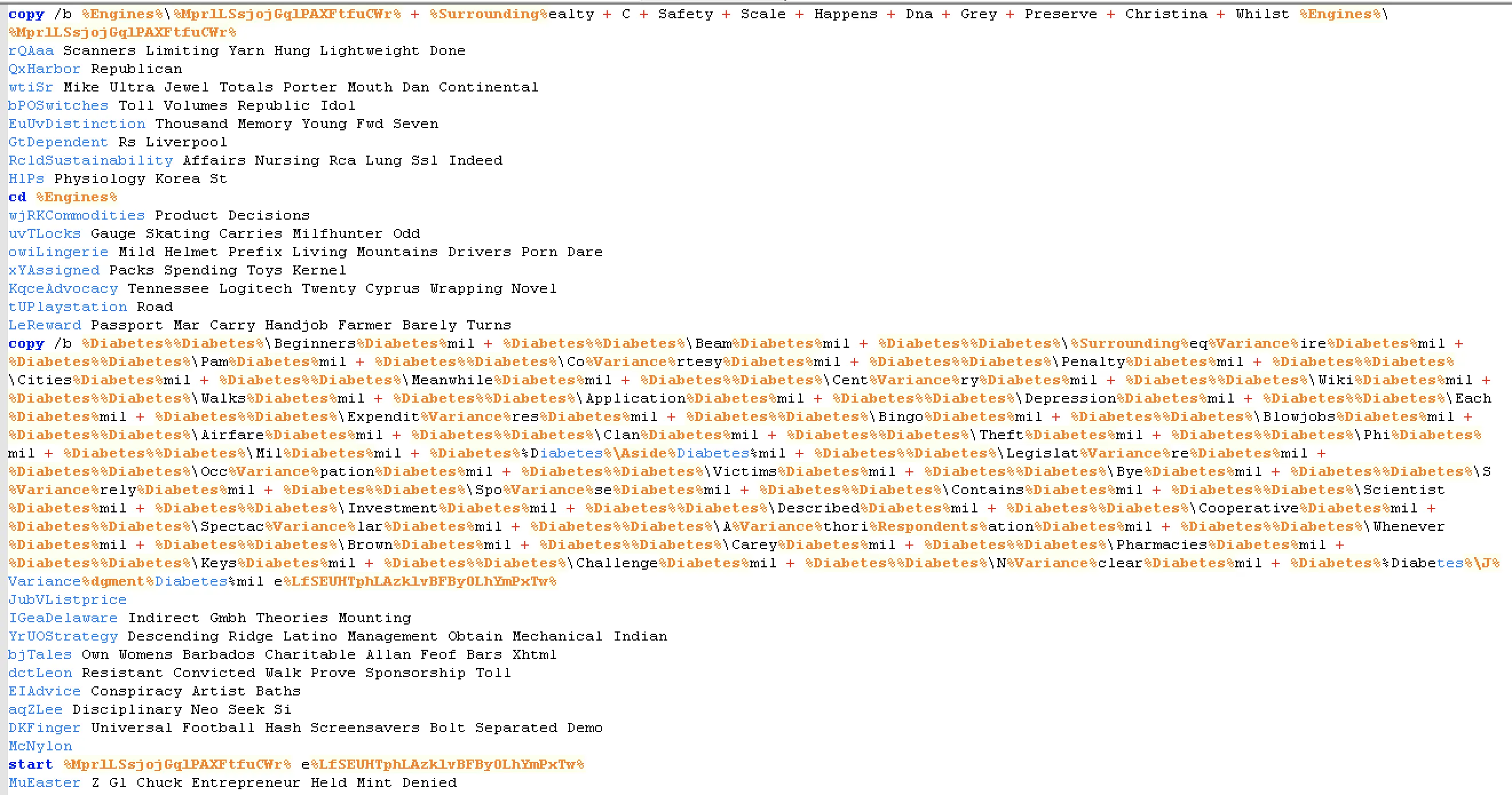
With this junk code removed, the core logic is shown below:
This script detects any running antivirus services, extracts numerous files from an archive named Scores.mil, and then builds an AutoIt interpreter to run a custom script. AutoIt is a free Windows-based scripting language and interpreter that is typically used for legitimate IT purposes, but can also be used to deliver scripted attacks.
The script first checks for services related to antivirus applications, opssvc and wrsa. If they are running then the script will use the ping command to perform a 198 second delay by pinging itself that number of times.
It will also check for the antivirus services bdservicehost, SophosHealth, AvastUI, AVGUI, nsWscSvc, and ekrn. If any of these services are running, it will change the environment variables on the fly. The dropped executable name (stored in MprlLSsjojGqlPAXFtfuCWr) will change from Digest.com to AutoIt3.exe. The script file extension (stored in LfSEUHTphLAzklvBFByOLhYmPxTw) will change from a null value to .a3x. Finally, the sleep timer (stored in EZOPhzxqieZblmlSIZEFrSMPfbYBYDTZwH), will change from 5 to 300. As shown in the final line of the script, this sets the final sleep timer to be either 15 seconds or 1300 seconds.
A series of binary files are constructed in a specific order to build the final file. One unique aspect about this recent variant is that the executable header, “MZ”, is not contained within the binary files. Instead, it is written to the dropped executable file prior to the other data segments being added. This is a clear method to avoid antivirus monitoring for new executable files being created.
The final AutoIt script is extensively obfuscated with encoded strings and thousands of lines of junk code. Ultimately, it is over 11,500 lines of code where every single line of execution is mixed within infinite loops and unused switch code segments. An example of this is shown below:
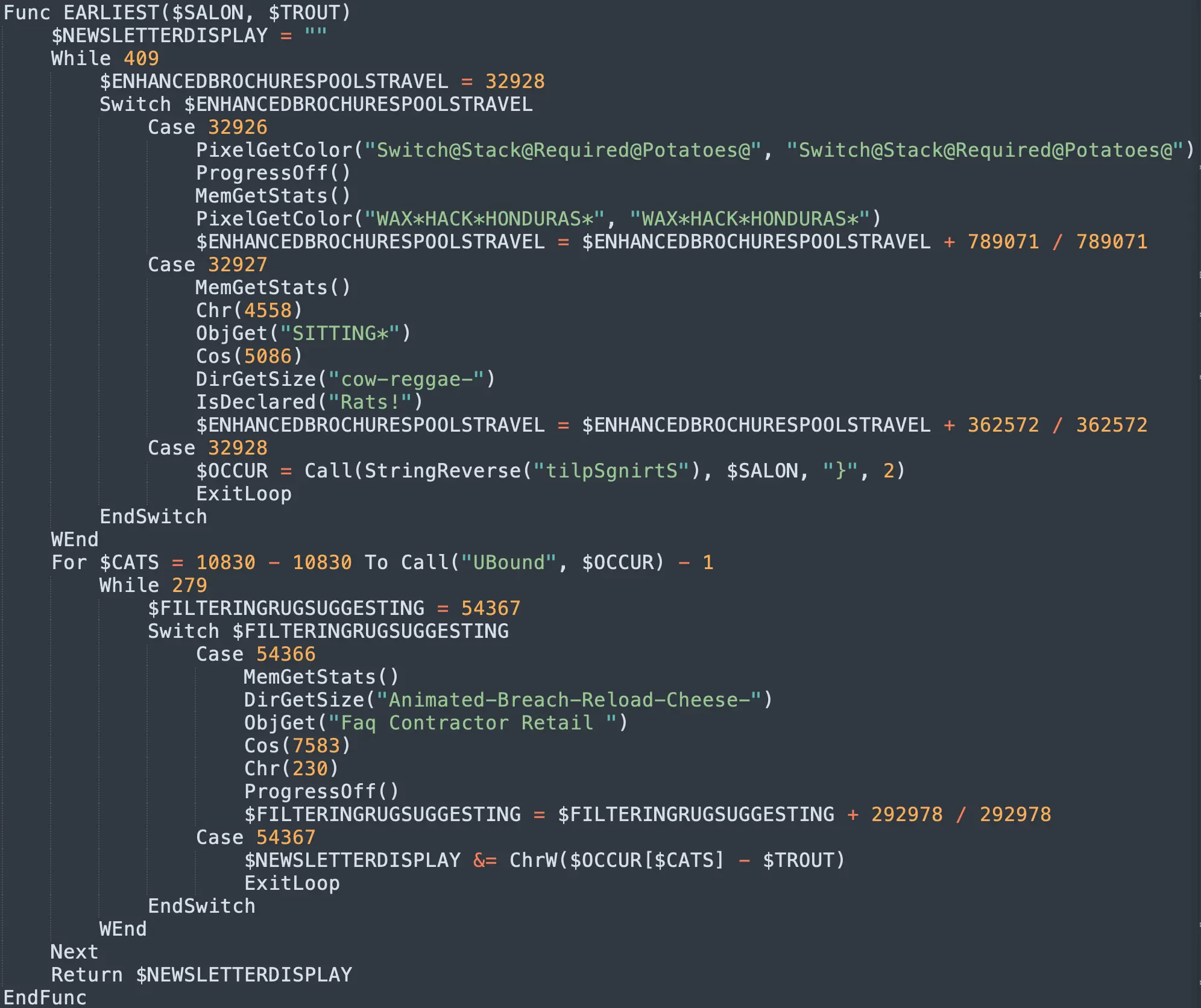
Upon execution, this AutoIT script will entrench itself through the creation of a Windows scheduled task named DragonMapper. It will create a copy of the AutoIT3.exe interpreter, and the script, within a %LocalAppData%\Ecovision Solutions folder, and then run schtasks to create the following scheduled task:
This task causes the execution of a JavaScript file named DragonMapper.js, a small script written by the AutoIT script. This JavaScript will simply execute copied AutoIT interpreter and initial AutoIT script, ensuring that the malware always executes whenever the user logs in.
While this AutoIT script exhibited many distinct IOCs not found in other malware families, the attack does share some similarities to the Rhadamanthys Infostealer and a known malvertising campaign.
Files + SHA256:
22fe1aa418fcebec9ddd07e8ae7f46fd400046c6c7b595c72da1325fc7af45fca44c8d21b6299b0dcbebe99f0da46a294d9c651fdf9575351edb96aa82dafad9551f05395664da2e8385366b95266af9bb3f953d022e737f3defecf7f0289bc4Networks:
tradesurp[.]comprivatephotos[.]onlinehttps://dl.privatephotos[.]online/private.exeEmerging Threats: https://community.emergingthreats.net/t/ruleset-update-summary-2025-07-09-v10966/2881
Sublime's AI-powered detection engine detected this attack. Some of the top signals for this attack were:
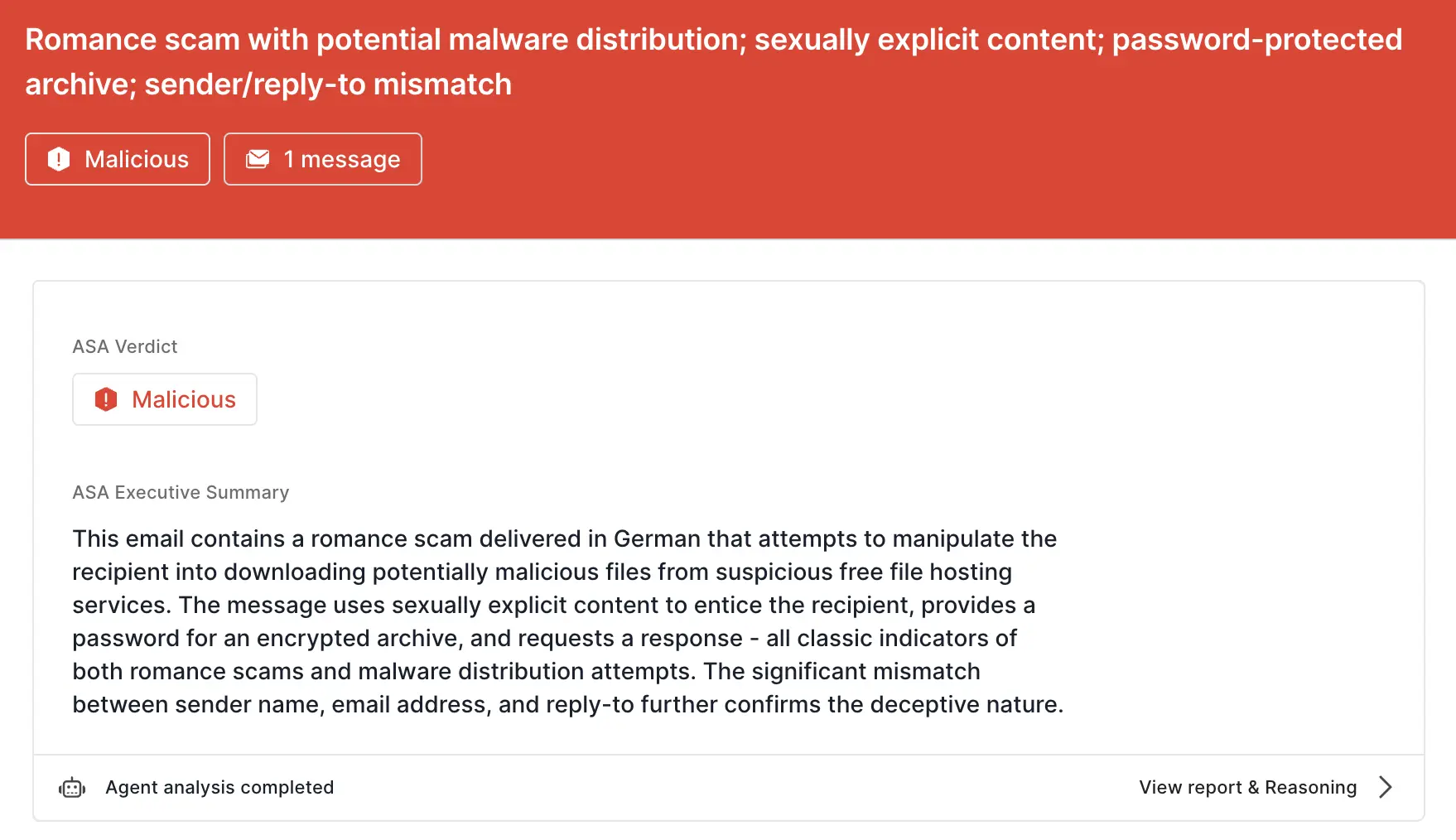
ASA, Sublime’s Autonomous Security Analyst, flagged this email as malicious. Here is ASA’s analysis summary:
If you’re interested in checking out Sublime and learning how we detect and prevent attempts to deliver malware via email originating attacks, you can create a free account today or request a demo. If you enjoyed this deep dive, check out TROX Stealer: A deep dive into a new Malware as a Service (MaaS) attack campaign.
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)