March 23, 2024

A brief background of PikaBot with a focus on recently observed attack techniques and email detection methods.
PikaBot, despite its name, is primarily a backdoor or loader rather than a traditional botnet. The malware emerged and has been operational since early 2023.
High-level characteristics of PikaBot include:
Modular Nature: Designed for flexibility and extensibility, PikaBot allows attackers to easily add or update its functionalities. This adaptability makes it a highly versatile tool for cybercriminals, enabling the execution of various malicious activities, from ransomware to InfoStealers.
Infection Techniques: PikaBot's distribution is primarily via email campaigns, utilizing phishing techniques with malicious attachments or deceptive URLs that deliver the malware. These emails are crafted to exploit system vulnerabilities or trick unsuspecting users, prompting the execution of malware through seemingly harmless actions. Delivery of PikaBot has been observed exploiting several known vulnerabilities and techniques, including DLL Search Order Hijacking (T1574) and CVE-2023-33151.
Evasion Tactics: PikaBot delivery mimics legitimate correspondences and employs numerous social engineering tactics to disguise attachments and links as familiar and trustworthy content. There are numerous evasion mechanisms:
Secondary Payload Delivery: PikaBot frequently acts as a conduit for additional malware delivery through emails. This could encompass a variety of secondary payloads, such as further ransomware or infostealers.
PikaBot is primarily distributed through email attacks. Below, we’ll break down some of the techniques that have been observed and discuss detection strategies.
.png)
A technique not exclusive to PikaBot, link-based, multi-stage malware delivery has been observed in numerous campaigns delivering a variety of malware including QakBot and others.
URLs are linked in emails that, when clicked, auto-download a ZIP file, which contain malicious JavaScript, LNK files, or PDFs with malicious embedded URLs.
Sublime uses a variety of signals to detect this type of attack:
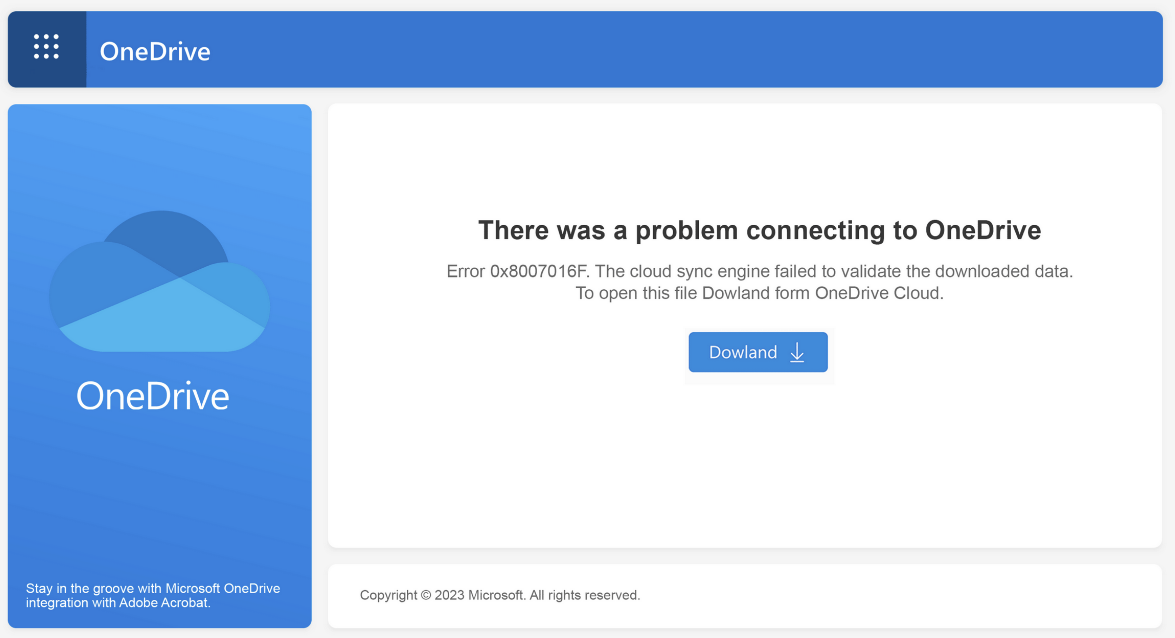
This attack chain begins with a common phishing technique, Brand Impersonation. The victim receives an email containing a PDF attachment that looks to be a Microsoft OneDrive share, with an error asking the user to “Dowland” the file instead.
Clicking this link will download a ZIP archive containing a JS file. If the user extracts and executes this JS file, it begins a fairly complex chain of procedures. First, it calls Windows Script Host ‘wscript.exe” to create a directory and then executes a curl command that downloads a DLL file. After a brief time delay, it then executes the obtained DLL files via ‘rundll32’.
Sublime uses a variety of signals to detect this type of attack:
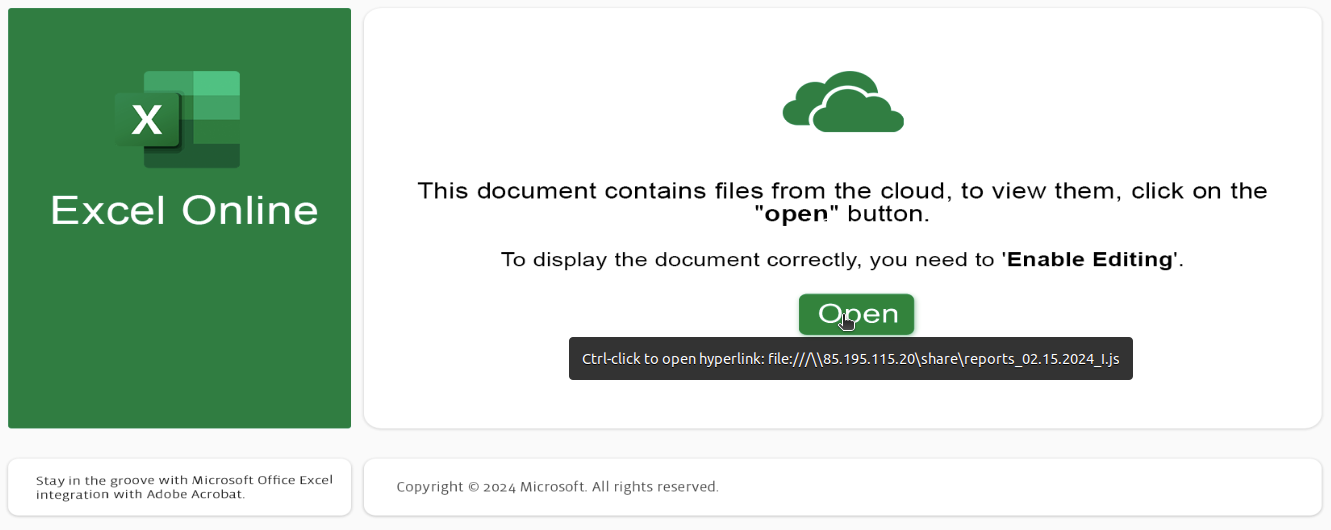
As originally posted by @DTCERT, this attack also leverages a common vector used in phishing attacks, an Excel attachment. The embedded link is cleverly crafted using an SMB structure. Upon interaction, it invokes Windows Script Host ‘wscript.exe’ to fetch a javascript file. This file downloads and executes a PikaBot DLL.
This can be detected in a variety of ways, from Excel brand impersonation to extracting the OLE relationships inside Word documents and analyzing the linked URLs for suspicious indicators. Source code for our latter detection can be found here.
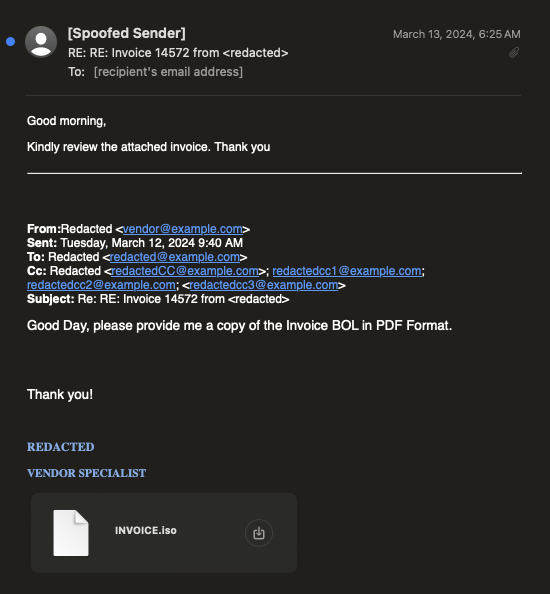
The attack chain begins with a common phishing technique known as "thread hijacking" or "thread reuse" where the attacker spoofs an email from a legitimate vendor. This message is carefully crafted to look like a continuation of previous communications between the vendor and the recipient, enhancing its legitimacy. The message prompts the recipient to review an attached invoice, which is actually an ISO image file containing the malicious payload.
Upon interacting with the ISO, the recipient invokes a modified version of the Windows Write application (’write.exe’). This side-loads a malicious DLL (’edputil.dll’) to specifically bypass security controls or alerts, and execute the malicious code undetected.
At this stage, PikaBot is installed and will attempt to communicate with its Command and Control server (C2). The C2 could send back a variety of options, and in our case an Infostealer was deployed, but this could easily be replaced with Ransomware, or other malicious payloads.
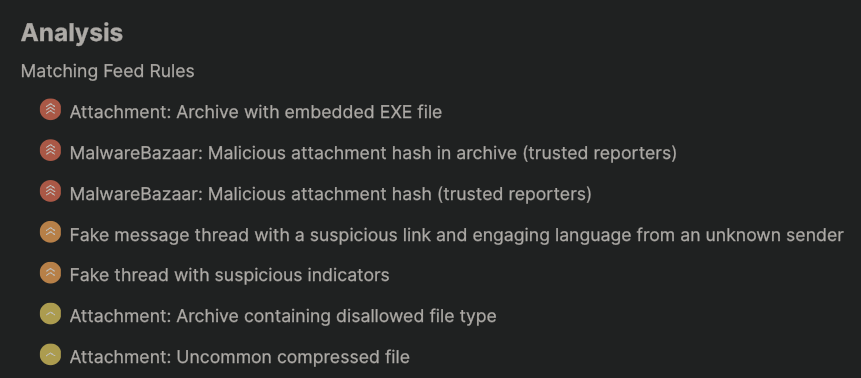
Detection at the email delivery layer is fairly straightforward, so we can use any number of the following methods to flag this message. For more information on how each of these work, as well as the source code, see our open source Feed or view it on GitHub.
The majority of techniques observed delivering PikaBot are not particularly novel—we've seen them used to deliver QakBot and other prominent malware families. It's important to focus on detecting attacker behavior to be resilient to the next evolution.
Sublime's Core Platform is free for the community with the ability to self-host, which means you can deploy protections for these techniques with a few clicks. You can also use our Managed Cloud Platform, which is free for up to 100 mailboxes.
Special shout outs to @malware_traffic, @Cryptolaemus1, and @pr0xylife, whose public research helped inspire this post, and to @affje0x65 for also sharing their research and Sublime Emerging Threats and Detection Rule Feeds.
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)