Solutions
Platform
Community
Sublime includes default protection for common attack types, with building blocks to create your own advanced detections.
Binary explosion recursively scans files delivered via attachments or auto-downloaded via links to detect HTML smuggling, suspicious macros, and other types of malicious payloads.
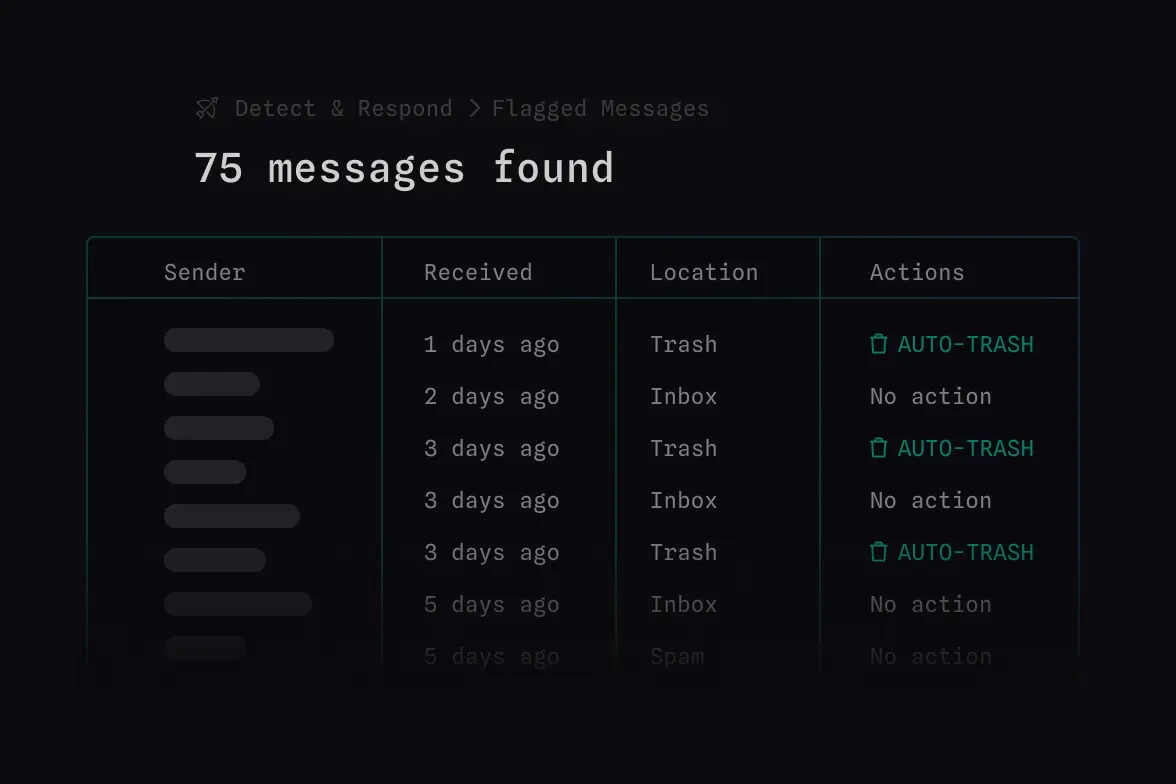





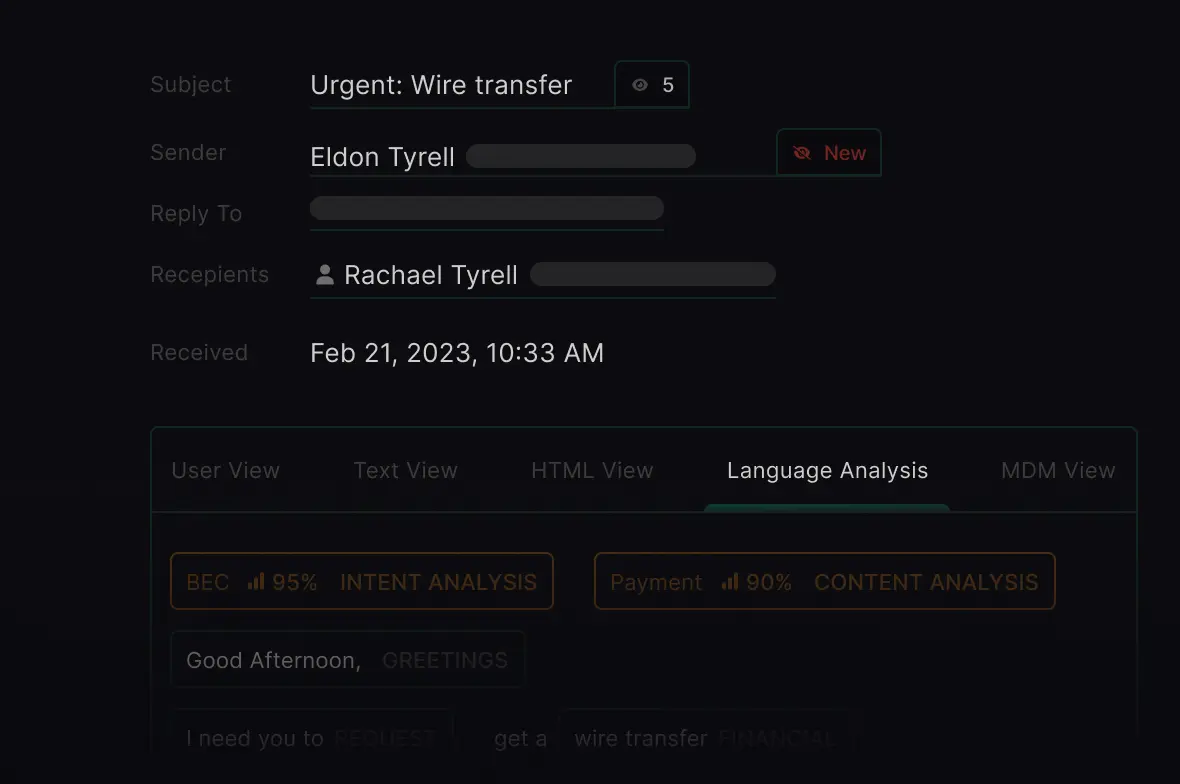
Natural Language Understanding analyzes message tone and intent and leverages sender history to detect payload-less attacks.


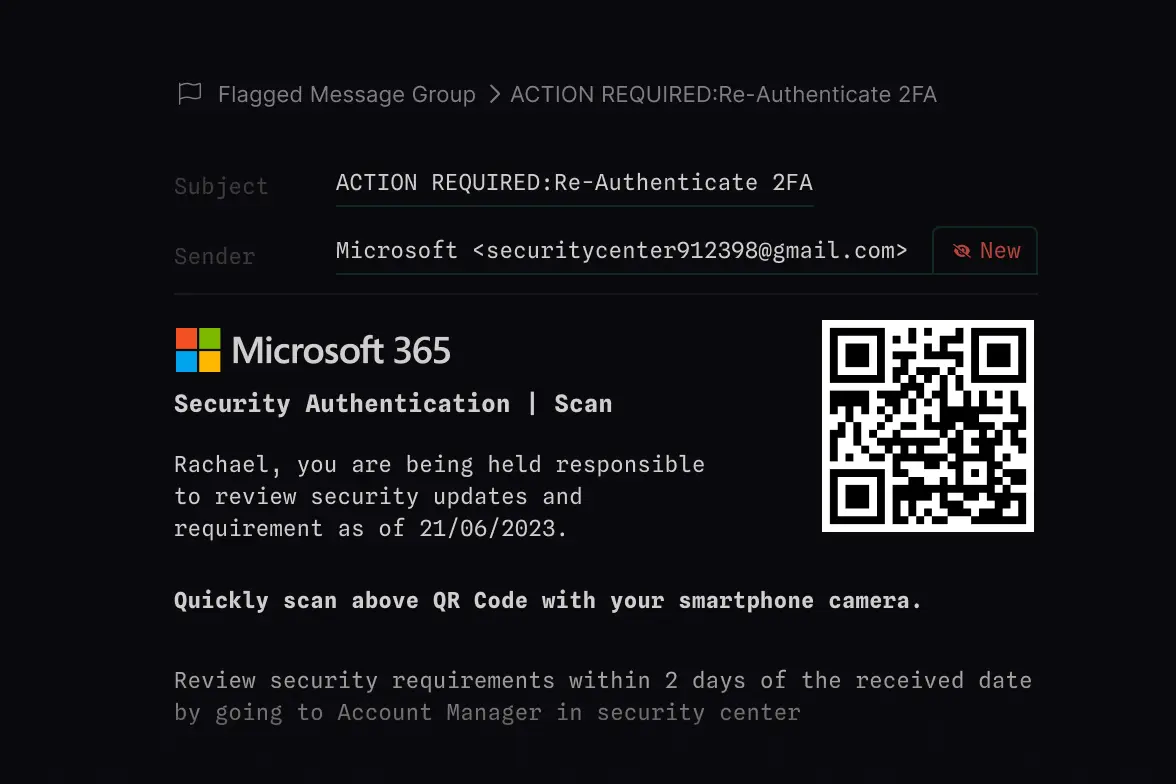
Identify QR codes in message bodies and attachments using Computer Vision and recursive binary explosion. Analyze encoded URL routing and destination for credential phishing, malware delivery, and more.


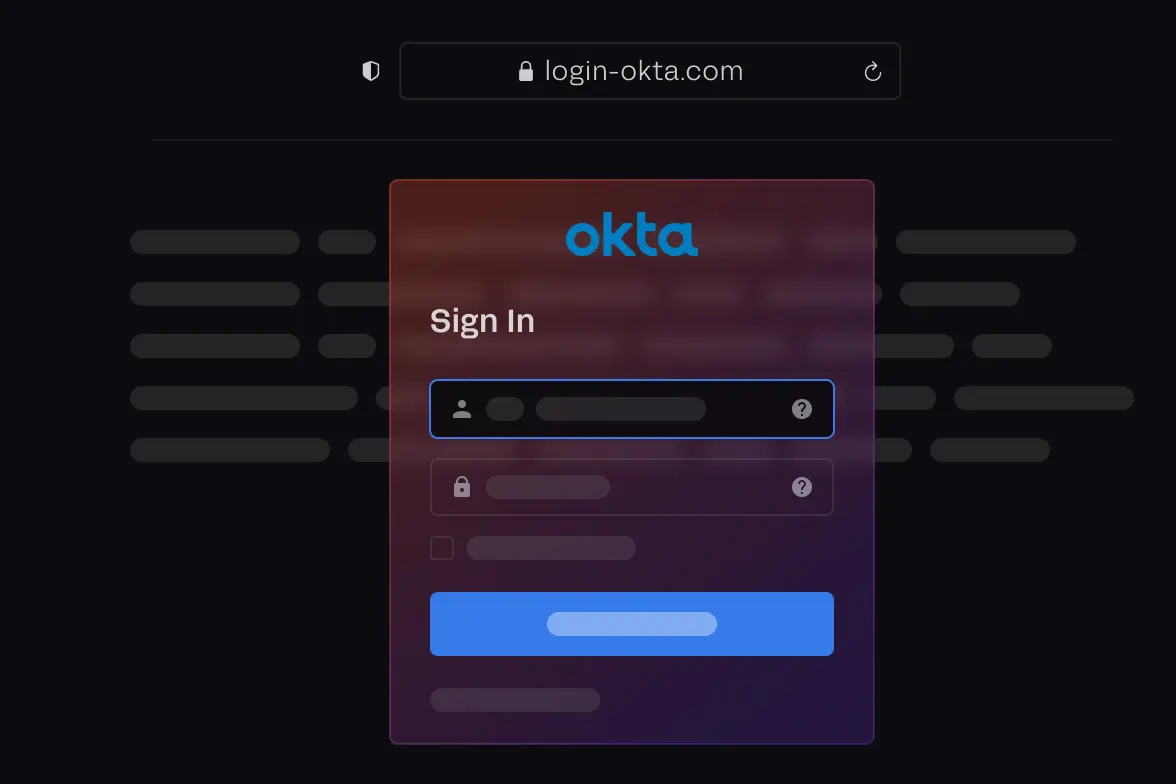
Link Analysis renders web pages using a headless browser and analyzes content using Computer Vision for impersonated brand logos, login pages, captchas, and other suspicious content.





Sender analysis leverages organizational context to detect impersonation of high-value users.





Optical-Character-Recognition (OCR) extracts key entities from attachments such as callback phone numbers.






Detection rules have been contributed both publicly and privately by Global 2000 security teams and independent researchers.

























Deploy and integrate a free Sublime instance in minutes.
For organizations of any size. First 100 mailboxes free.
Limited to 600 active mailboxes. View Docker Guide.
Scales to any number of mailboxes. View AWS Quickstart
Coming Soon!

