July 31, 2025
Attack payload featuring two RMMs, one installed interactively and the other silently
Sublime’s Attack Spotlight series is designed to keep you informed of the email threat landscape by showing you real, in-the-wild attack samples, describing adversary tactics and techniques, and explaining how they’re detected. These attacks can be prevented with a free Sublime account.
EMAIL PROVIDER: Microsoft 365
ATTACK TYPE: Malware/Ransomware
Remote Monitoring and Management (RMM) software is in every IT toolbox, and with increasing frequency, many bad actors’ too. Once an RMM has been installed maliciously, an attacker can take control of the machine to exfiltrate data, lock it down for ransom, use it as a proxy to deliver other attacks, and more, making RMMs a great way to attack or cover tracks.
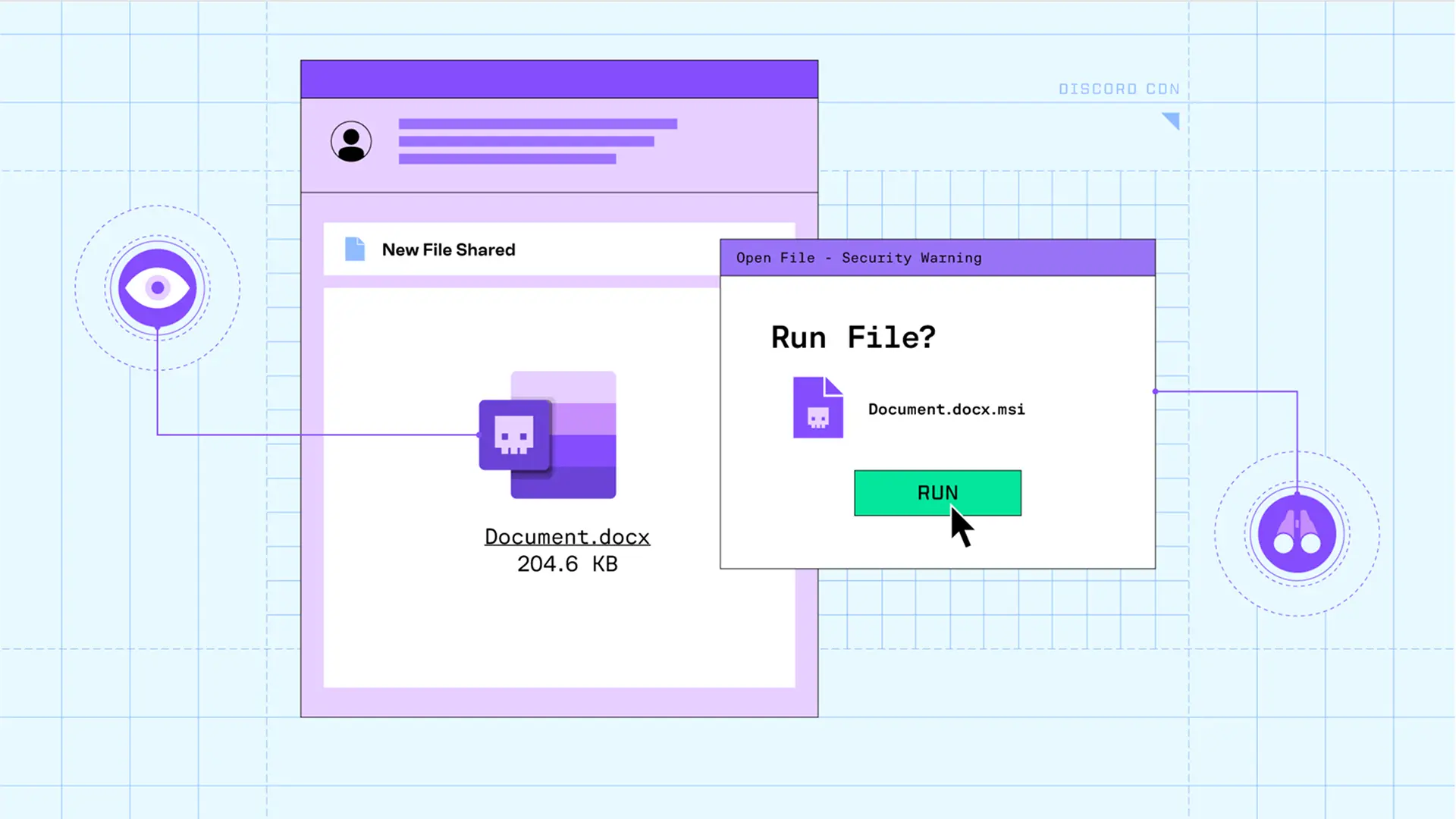
In a recent attack, we saw two RMMs delivered in a single malicious payload. With two RMMs running, an attacker maintains remote control even if one RMM is discovered. This attack involved a compromised email account, OneDrive impersonation, and file extension manipulation in order to deliver the payload. Let’s take a look.
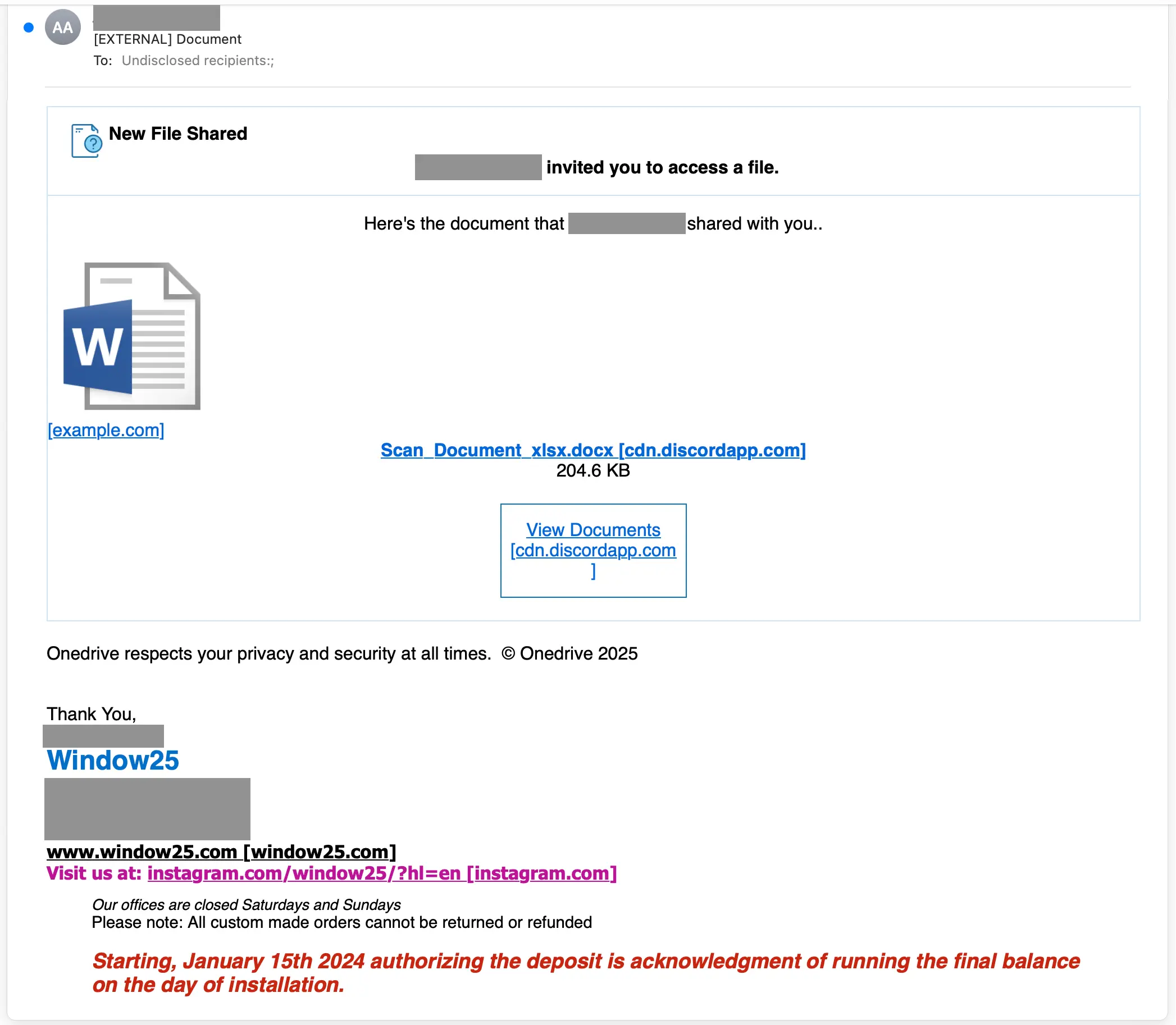
First, the malicious email is sent from a compromised account to an undisclosed recipient list. The message contains a link that appears to be a .docx hosted on cdn.discordapp[.]com. This message is designed to look like it’s from OneDrive, including a Word icon and a OneDrive privacy footer.
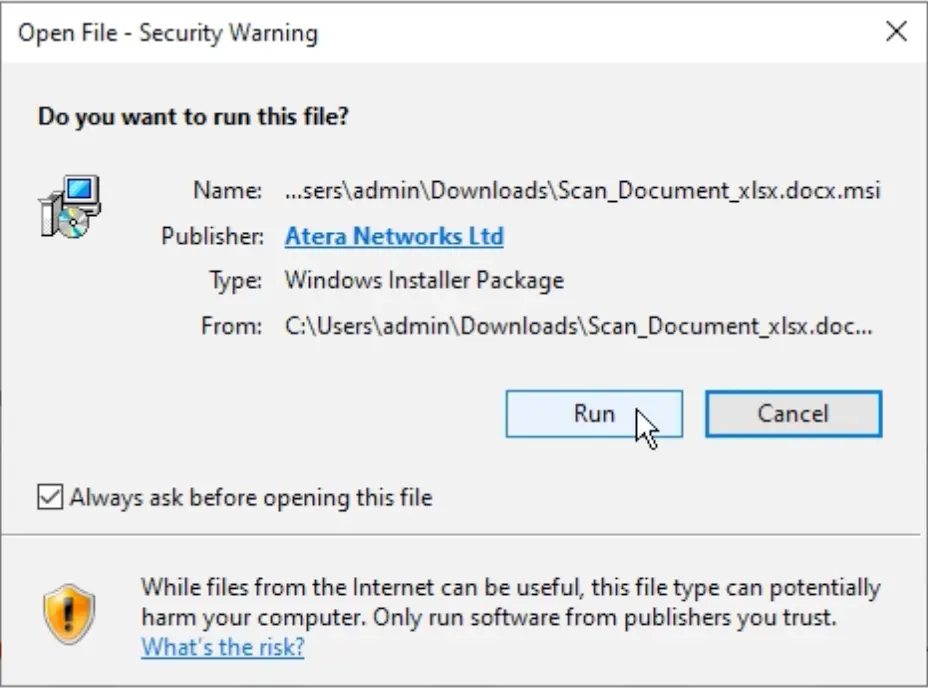
If the target clicks the link, they download a file with the same filename listed in the email, except that it ends in .msi after the .docx. If launched, the first RMM is installed and configured: Atera.
This attended install of the Atera Agent is followed by auto-configuration.
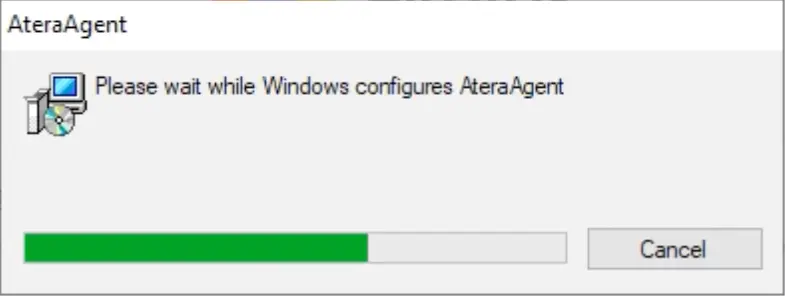
While this attended installation is going on, two silent installations are running in the background: Splashtop Streamer and .Net Runtime 8. Both of these files are downloaded directly from legitimate sources, appearing as innocuous web traffic.
Upon completion of the visible, attended installation, the attacker can now access the target machine via either Atera or Splashtop. As this attack was caught before the payload could be delivered, it’s unclear if this was going to be used for ransomware, exfiltration, or more.
Sublime's AI-powered detection engine prevented this attack. Some of the top signals for this attack were:
.docx file, but they are instead taken to a similarly-named .msi file.ASA, Sublime’s Autonomous Security Analyst, flagged this email as malicious. Here is ASA’s analysis summary:
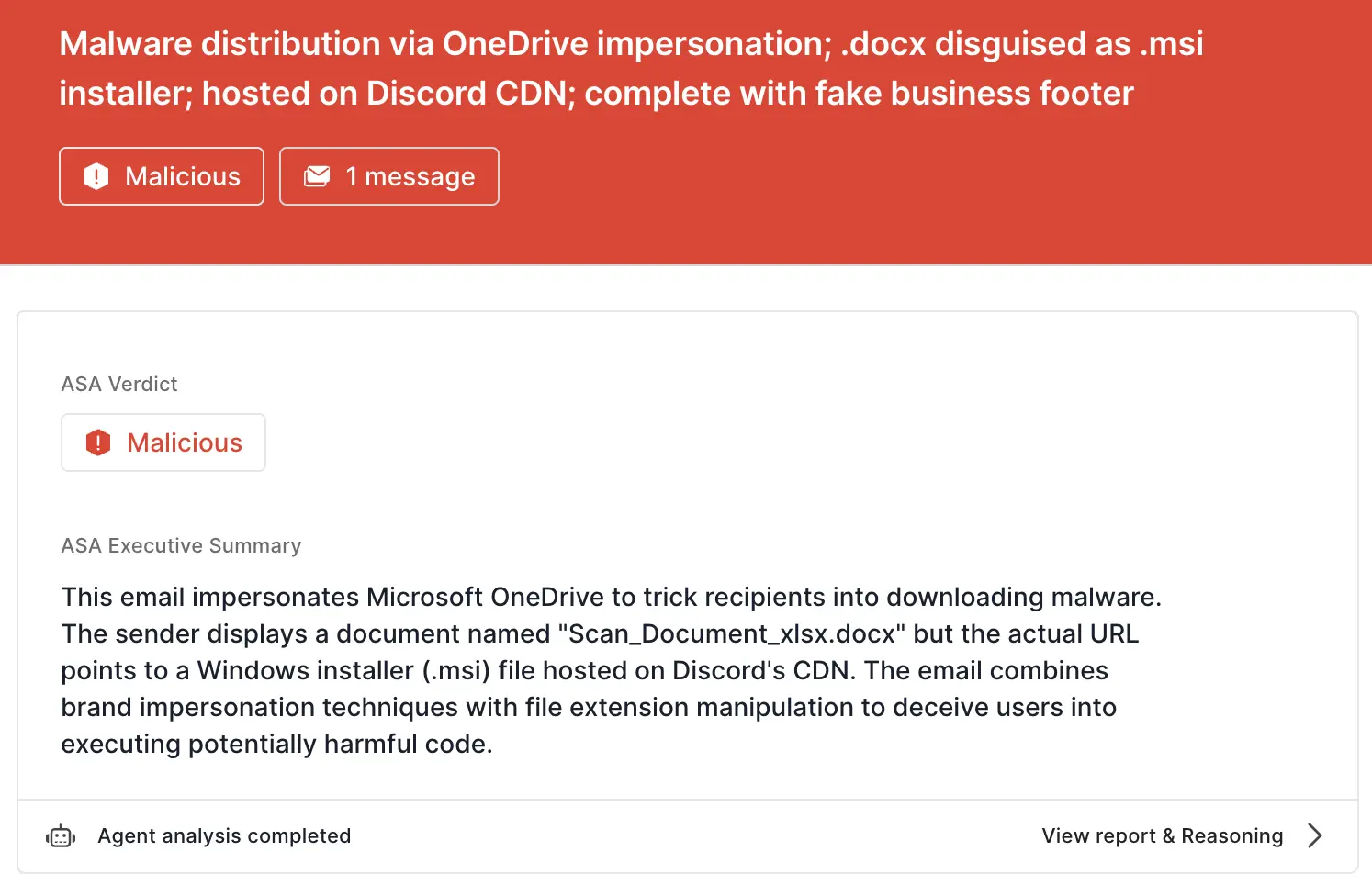
RMM attacks give bad actors a lot of ways to do bad things, so it’s important that malicious installers don’t make it into inboxes. That’s why the most effective email security platforms are adaptive, using AI and machine learning to shine a spotlight on seemingly minor discrepancies.
If you enjoyed this Attack Spotlight, be sure to check our blog every week for new blogs, subscribe to our RSS feed, or sign up for our monthly newsletter. Our newsletter covers the latest blogs, detections, product updates, and more.
Read more Attack Spotlights:
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)