November 13, 2025
Malicious messages sent from compromised or fraudulent Salesforce accounts
Over the past few months, we’ve seen a steady stream of email attacks and spam sent over legitimate Salesforce infrastructure. It is unclear exactly how adversaries are gaining access to Salesforce infrastructure, but it’s speculated that they could be compromising existing Salesforce accounts or spinning up fraudulent accounts on stolen payment information.
Like other Living Off Trusted Sites (LOTS) attacks we’ve written about, adversaries are leveraging Salesforce infrastructure to boost legitimacy and aid in evasion. Salesforce is a trusted company (legitimacy) and blocking messages from their infrastructure en masse would result in a high percentage of false positives (evasion). Let’s take a look at a few different types of messages we’ve seen and the signals Sublime uses to stop them.
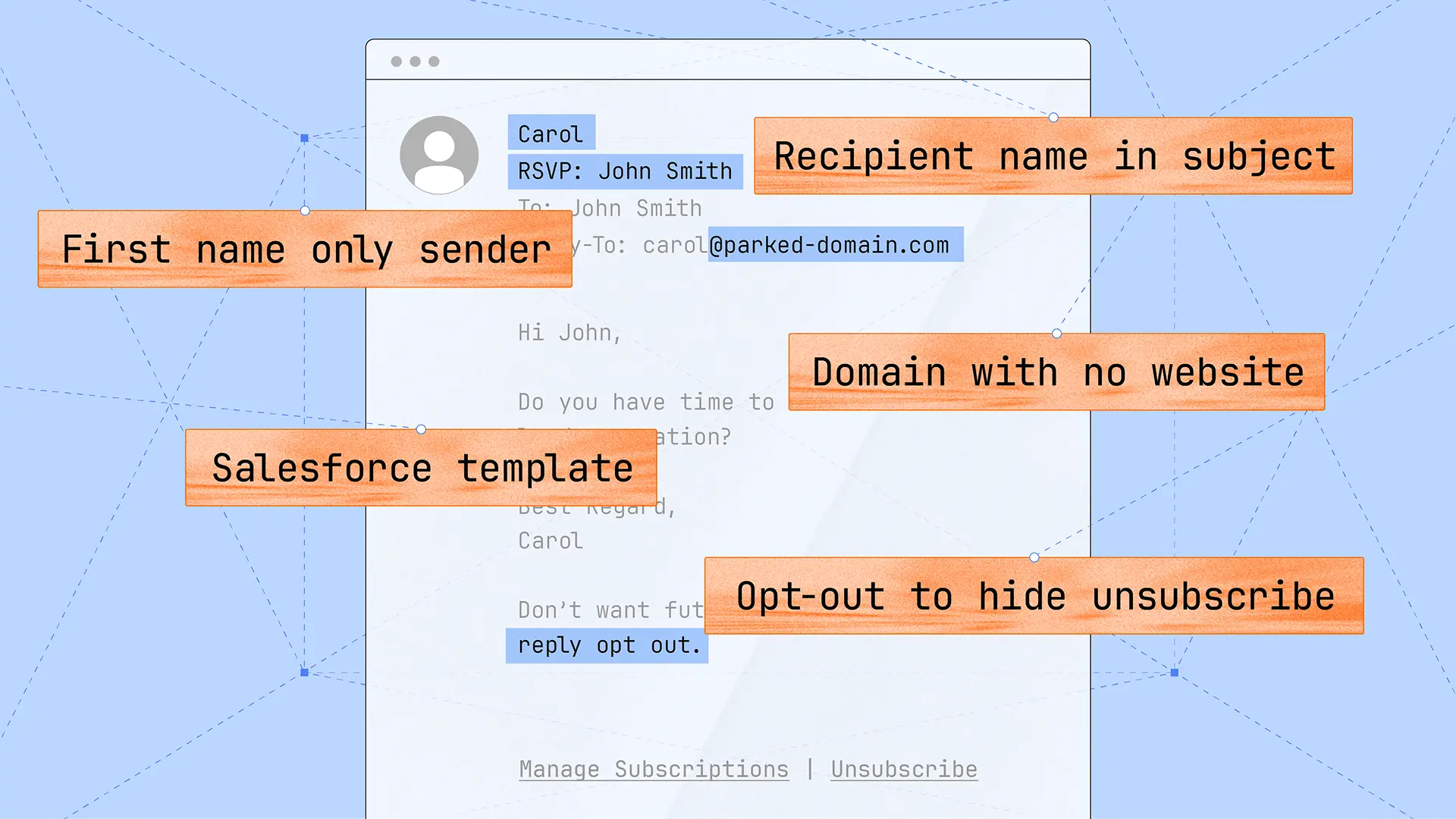
The first type of message we’ll look at is also the highest volume type of message, with thousands being sent in bulk. The intent of these messages is to get the target to respond with an “opt out” message to unsubscribe. Responding confirms both target receipt and engagement. This small interaction could result in the target being added to a high intent spam list, the initiation of a BEC attack, and more. Here’s an example email:
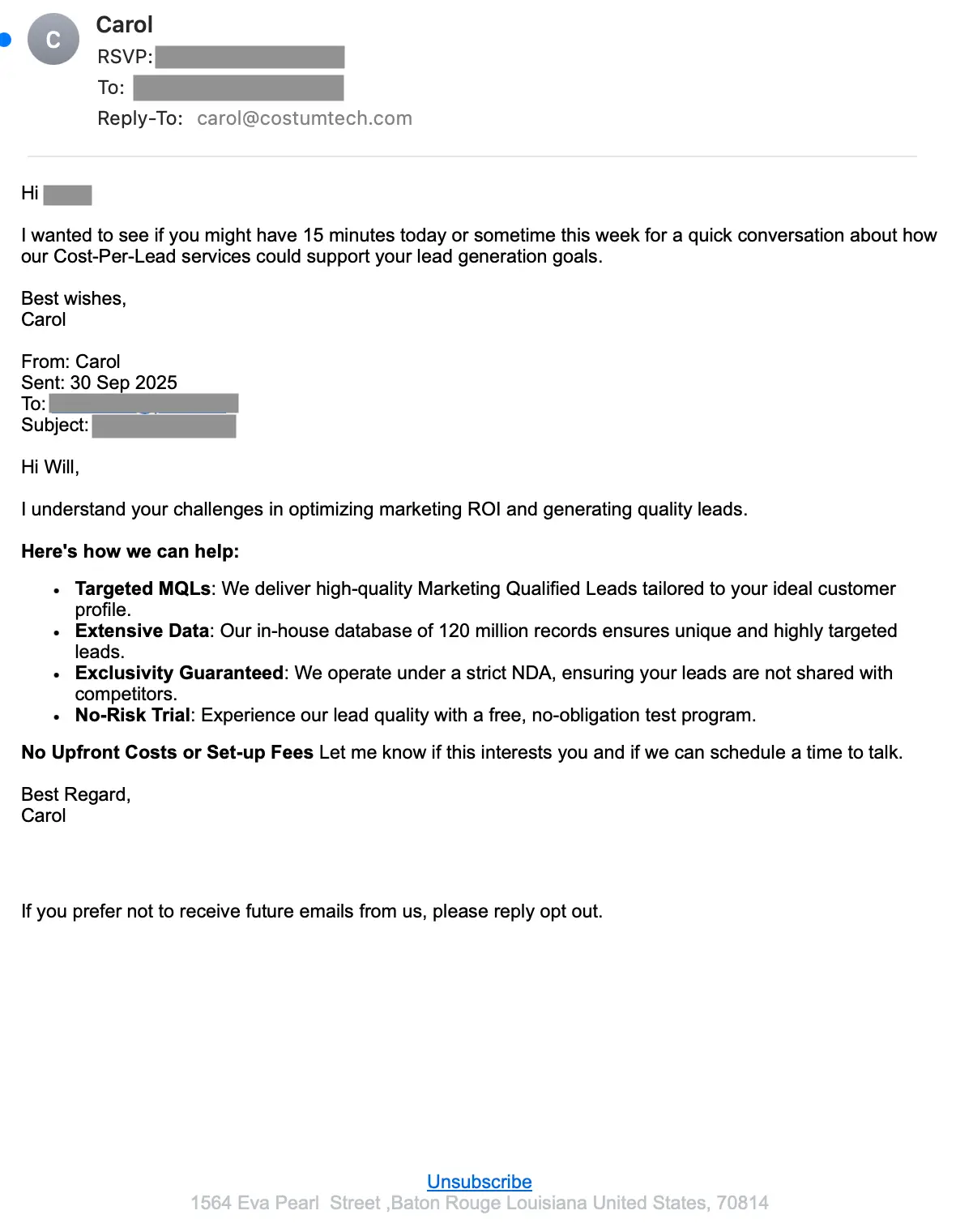
These messages contain a few recurring themes:
While many of these signals appear in malicious messages, they could also be adopted by marketing teams that intend to leverage the same proven tactics for driving non-malicious engagement.
We recently covered the ongoing barrage of credential phishing job scams sent through a variety of methods. A significant amount of those attacks were sent using Salesforce infrastructure. Here’s an example impersonating a Nike recruiter:
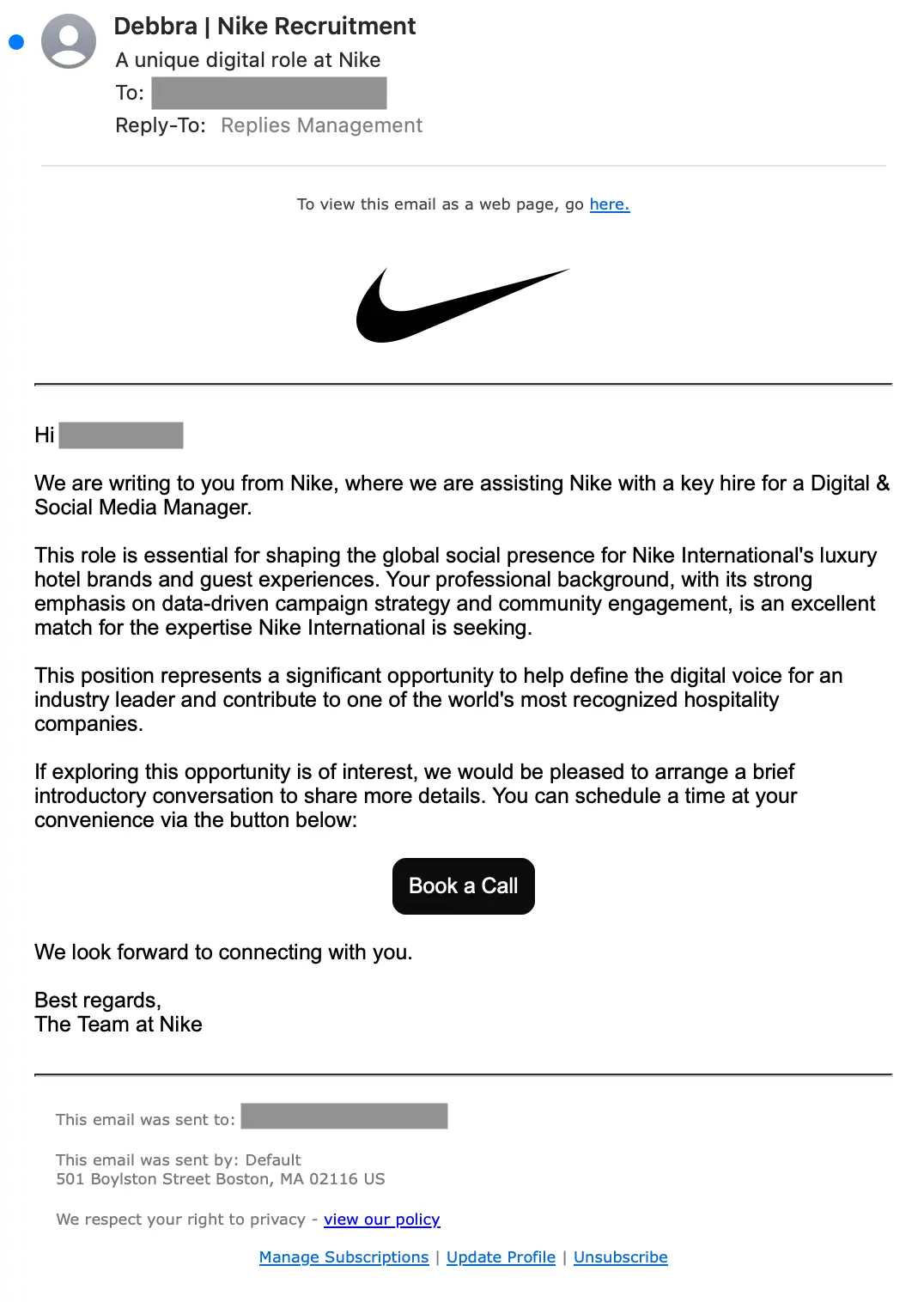
The Book a Call button leads directly to a credential phishing page hosted on Vercel (nikewaycareers.vercel[.]app). But since this message was sent via Salesforce, it contains many more legitimate links than suspicious:
view.s12.exacttarget[.]com which redirects to to s12.view.sfmc-marketing[.]com.cl.s12.exct[.]net URLs.We’ve observed variants of this attack imitating many different companies and used for both credential and callback phishing.
In this last attack, we see Salesforce being used to deliver a crypto wallet theft payload. Just like the previous attack, the bad actor uses the Salesforce email template with all of the legitimate management links. In this case, though, they impersonate Trust (a company that offers a crypto wallet) and offer a chance to participate in a Shiba Inu token airdrop.
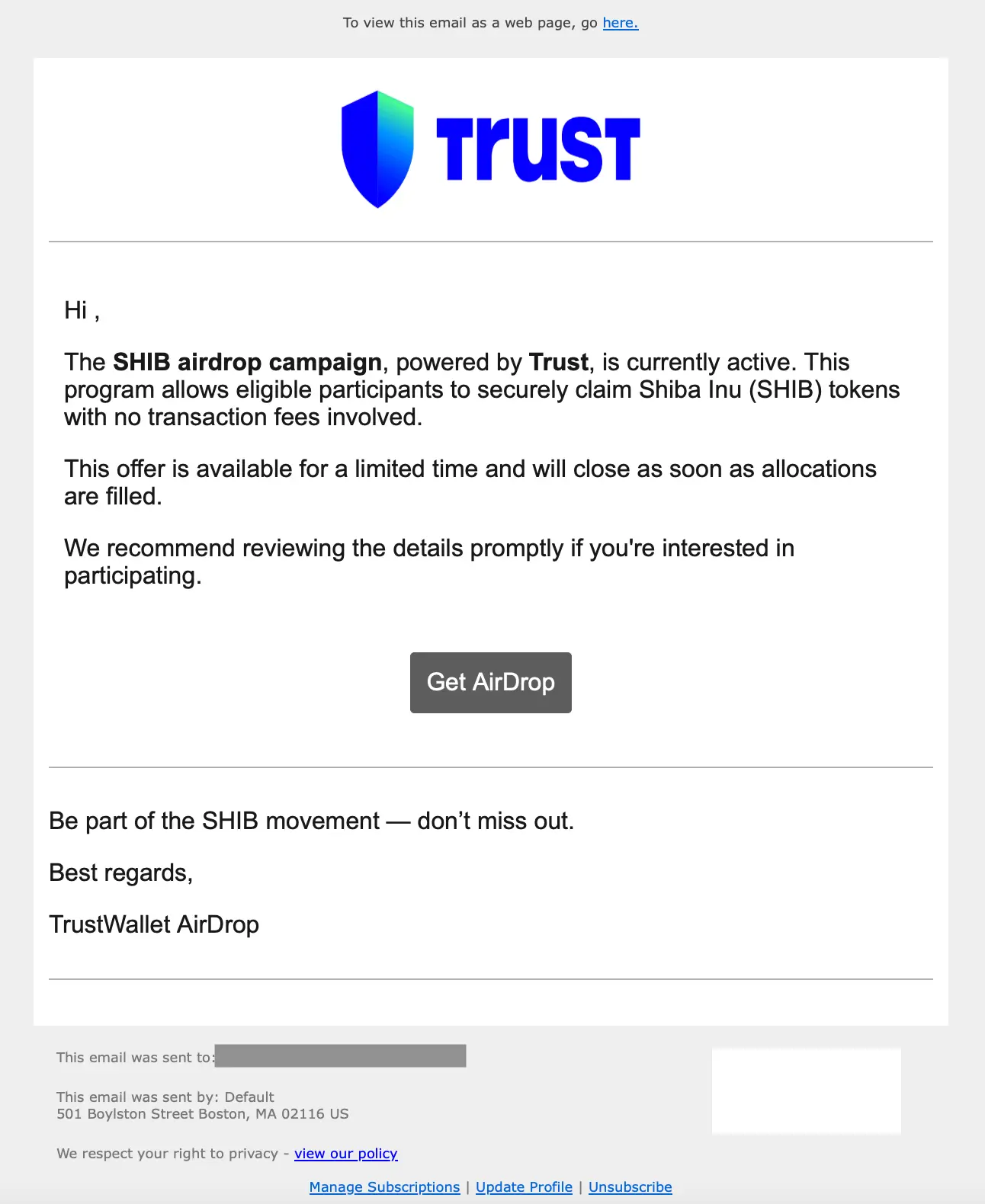
Hovering over the Get AirDrop button shows a preview link of nam12.safelinks.protection.outlook[.]com that contains a URL redirect to Salesforce infrastructure. Clicking on that button follows the URL redirect and then redirects one more time to a free pages[.]dev Cloudflare page (we previously covered this malicious use of Cloudflare pages) that harvests crypto information:
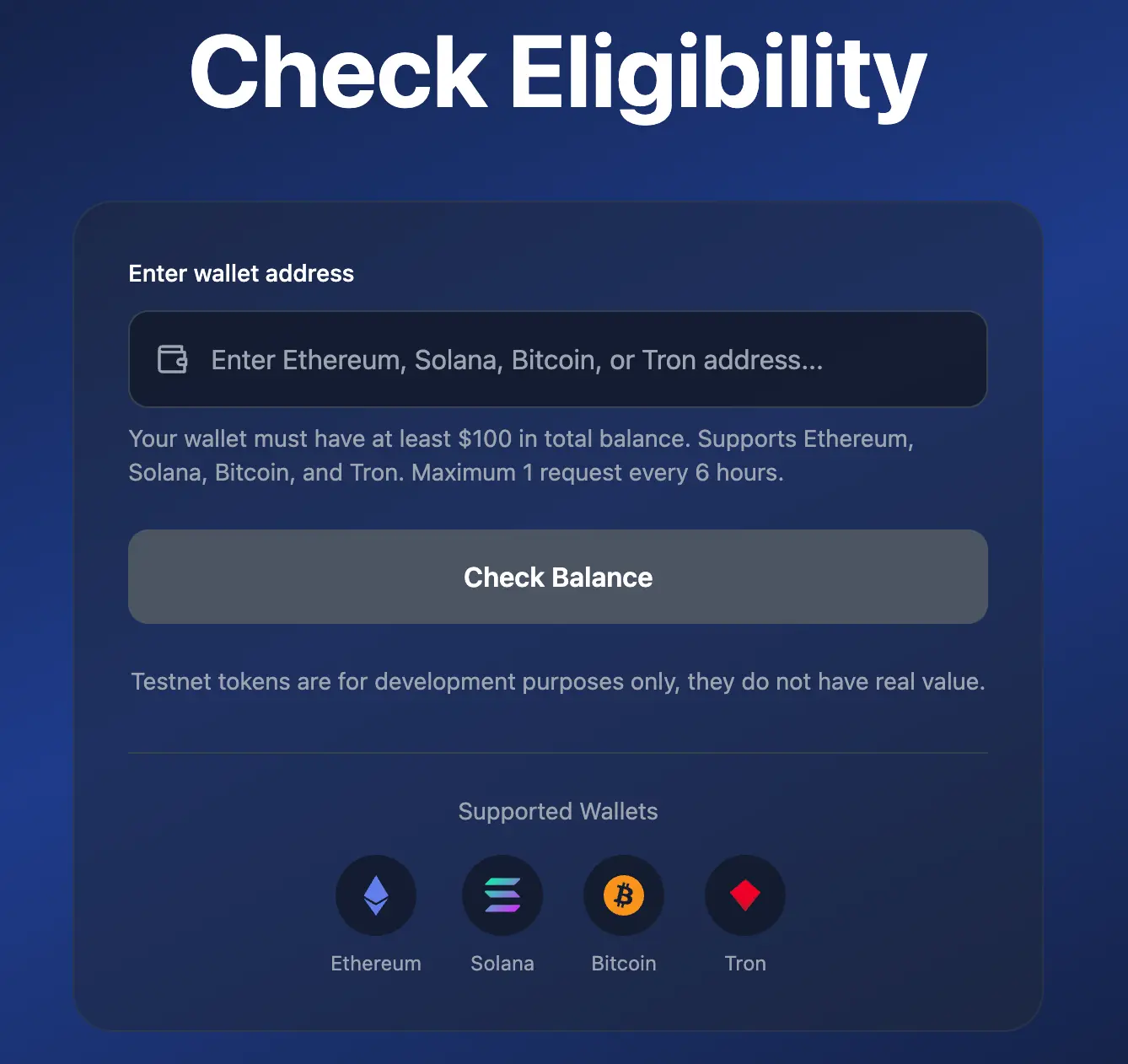
After entering a wallet address, the page confirms if the wallet is real.
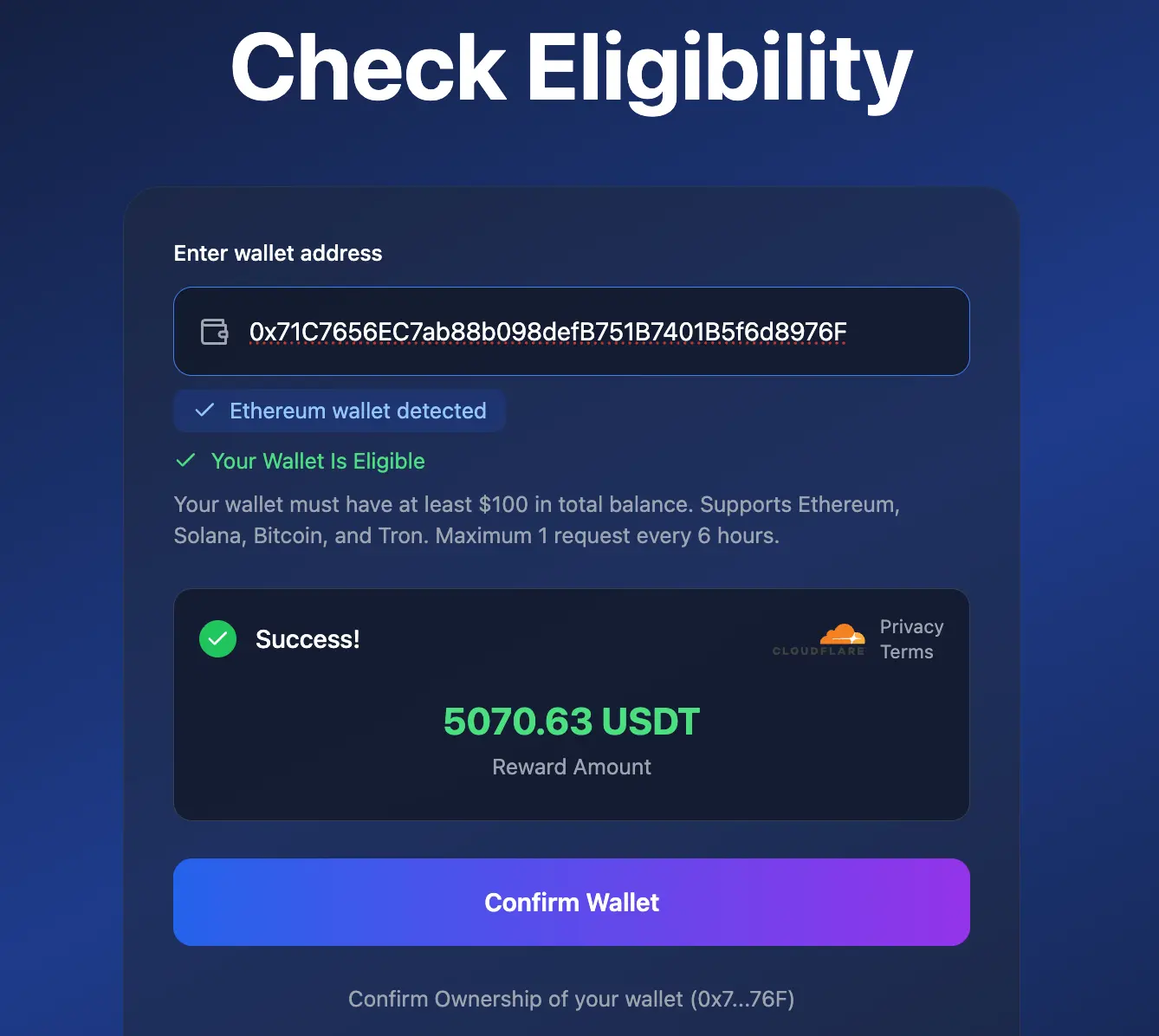
After confirmation, you’re asked to connect to a wallet… again.
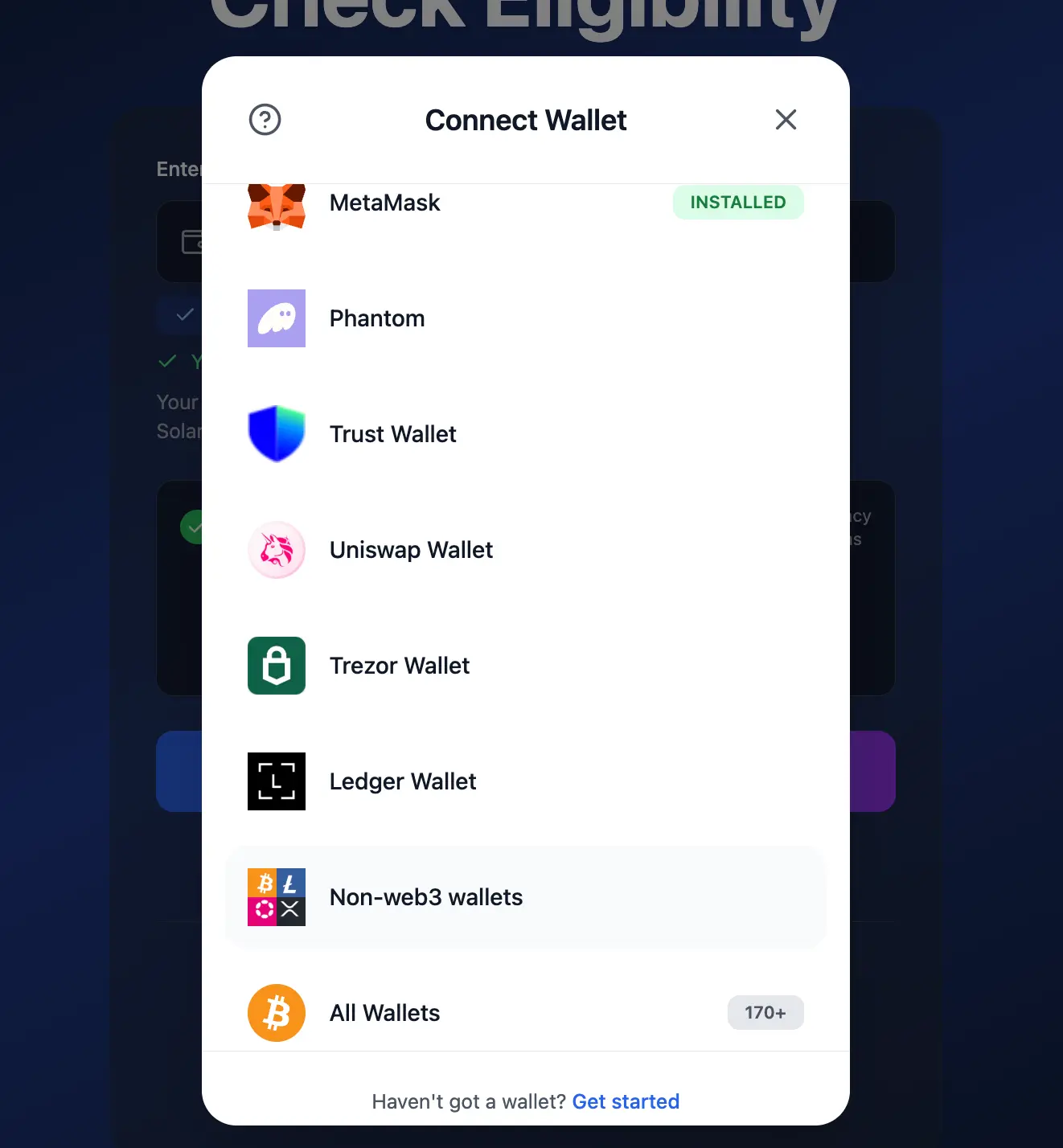
The connection attempt will fail, and the target will be forced to manually connect.
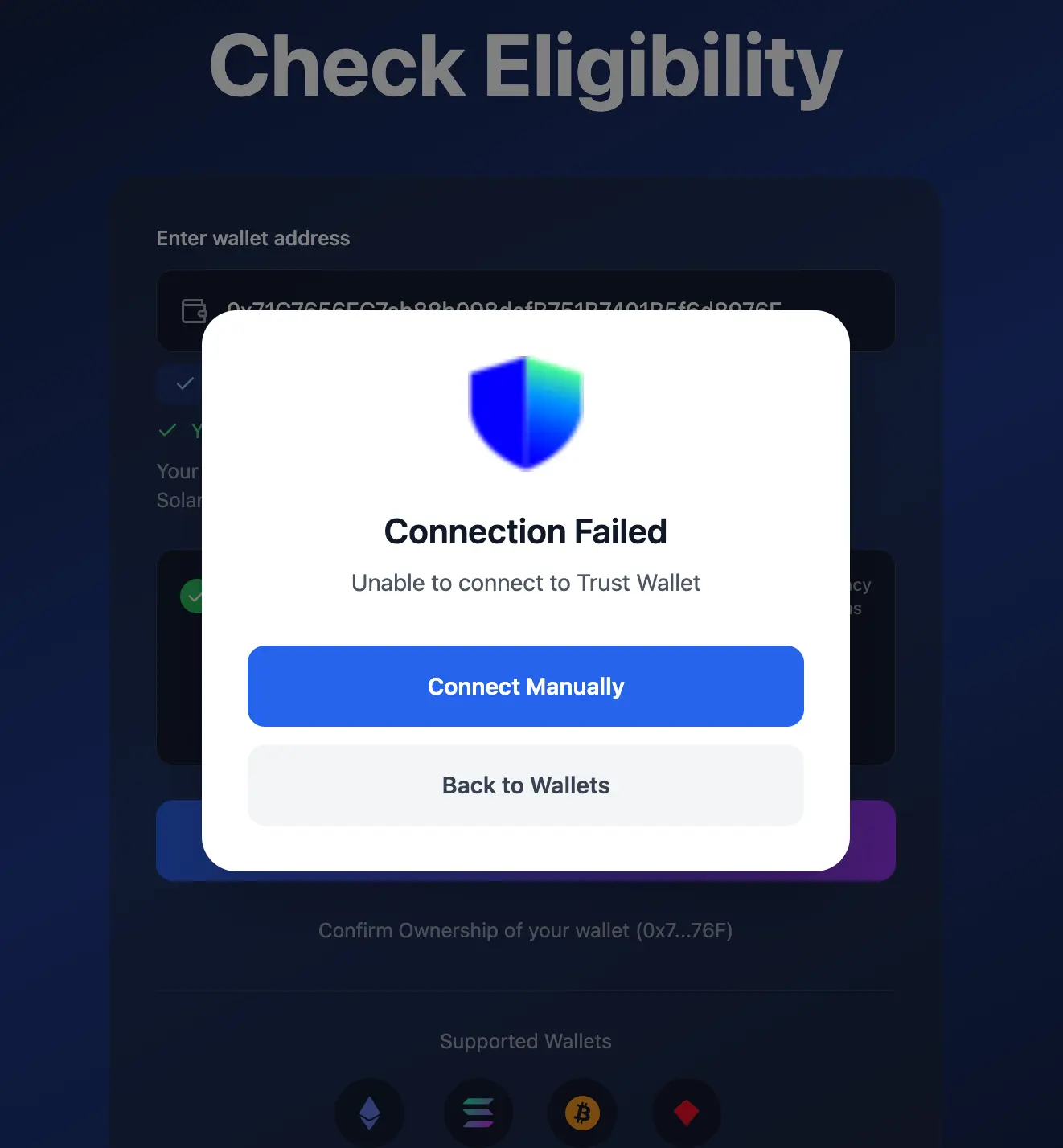
They are prompted for a recovery phrase to complete the connection. Note the mismatch before the 24-word prompt and the 12 text fields.
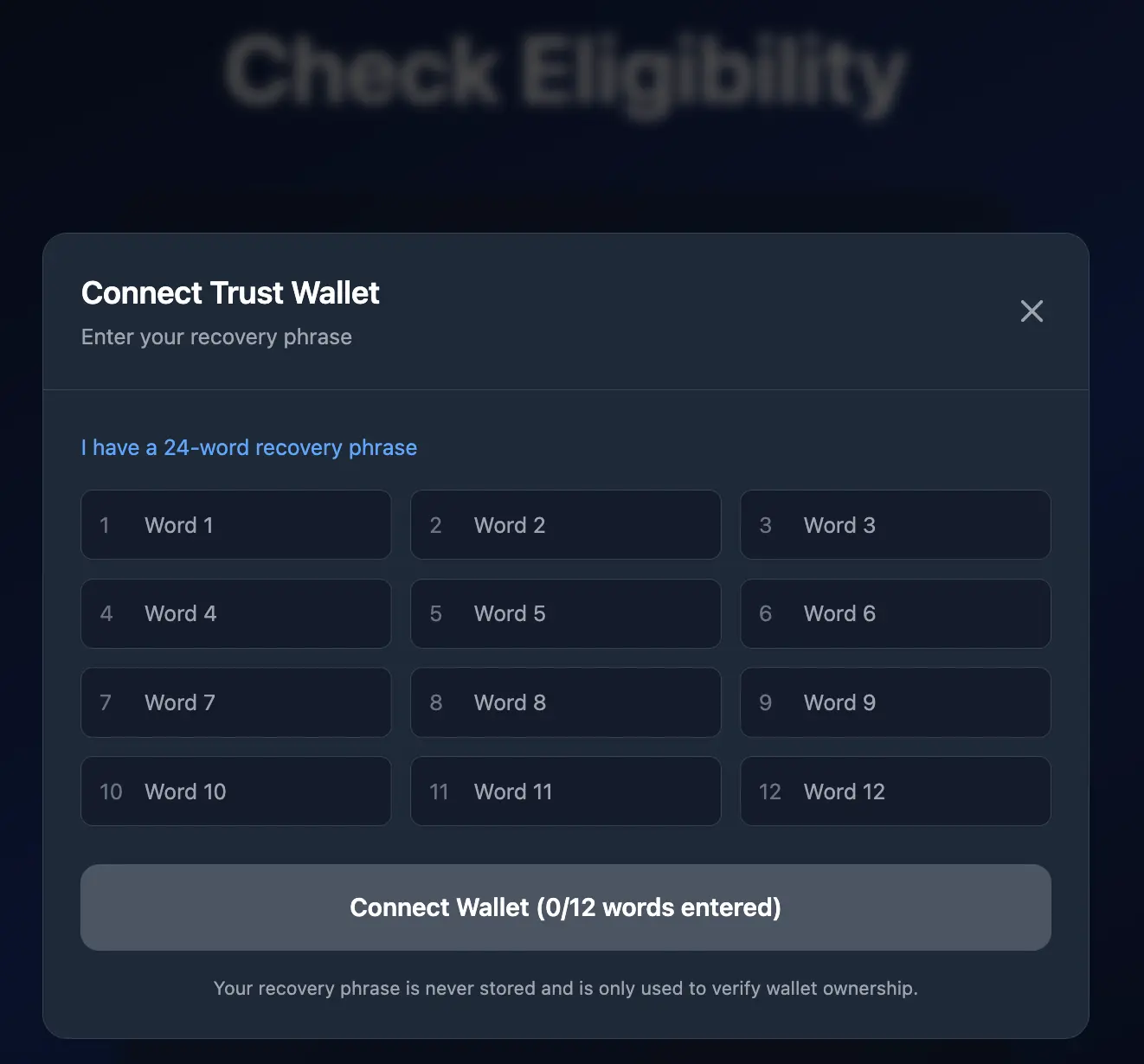
After filing out the 12 boxes and clicking connect, no validation occurs. Instead, the target is taken to a confirmation screen indicating a successful connection and the upcoming transfer of reward tokens.
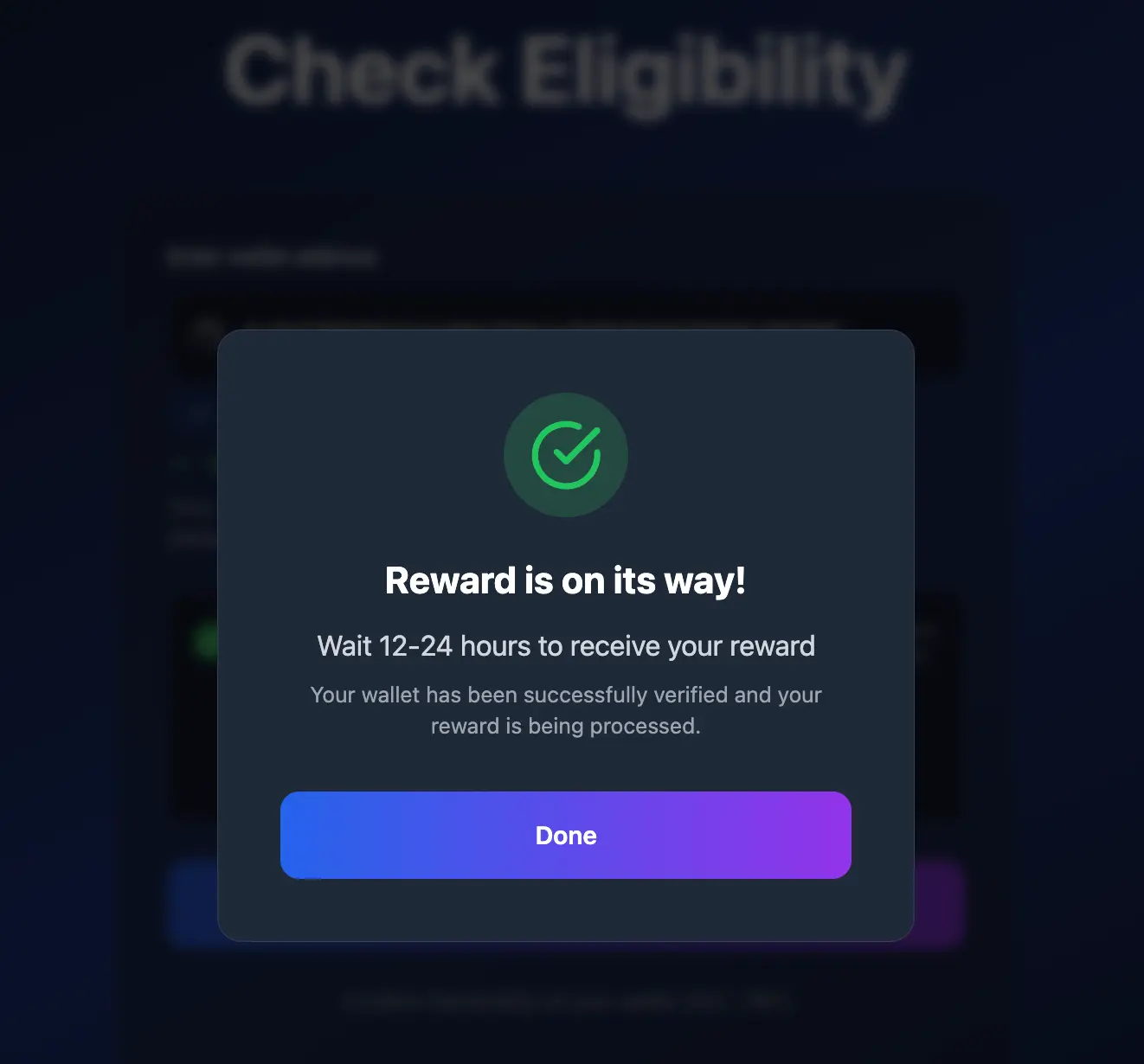
At that point, the bad actor has all the details needed to siphon fund from the crypto wallet.
Sublime's AI-powered detection engine prevented the above attacks. While each attack leveraged legitimate Salesforce infrastructure, each also offered a variety of detection signals. Here are some of the top signals from the crypto phishing attack:
ASA, Sublime’s Autonomous Security Analyst, flagged these emails as malicious. Here is ASA’s analysis summary for the crypto attack:
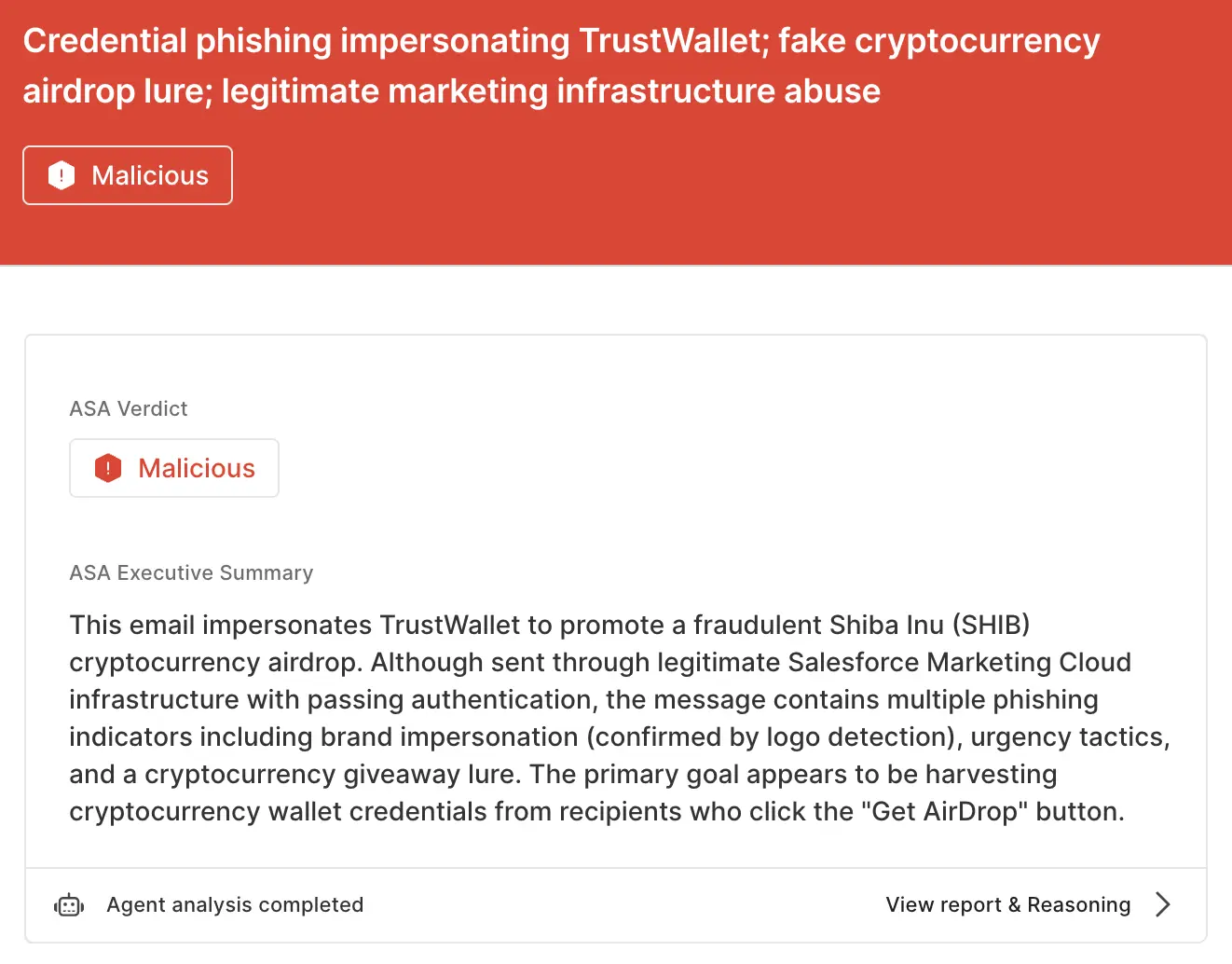
While Salesforce abuse is real and rampant, it’s not an instant indication of malicious intent. That’s why the most effective email security platforms are adaptive, using AI and machine learning to shine a spotlight on the suspicious indicators of the scam. To see how Sublime can keep these attacks out of your inboxes, get an expert demo today.
If you enjoyed this Attack Spotlight, be sure to check our blog every week for new blogs, subscribe to our RSS feed, or sign up for our monthly newsletter. Our newsletter covers the latest blogs, detections, product updates, and more.
Read more Attack Spotlights:
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)