April 28, 2025

Increased threat uniqueness, emerging attack vectors, evasion techniques by attack type, and more
In our first Sublime Email Threat Research Report, our Machine Learning and Detection teams analyzed anonymized customer telemetry under strict adherence to our internal Data Privacy Framework. The findings highlight significant growth in QR code phishing, OAuth phishing, and the need for a layered, adaptive detection strategy.
Email threats continue to evolve rapidly, with threat actors demonstrating increased sophistication in both novel attack vectors and evasion techniques. What we found:
Emerging trends make it clear organizations need a layered, adaptive detection strategy that blends AI, machine learning, behavioral analysis, and threat intelligence complemented with other defense-in-depth controls to effectively counter the full spectrum of email threats.
On average, 90% of malicious emails detected were customized (as defined in the report) to their target in some way, representing a 12% increase from our observations in Q1 2024. This is the clearest signal yet that mass, template-driven phishing is dying. Attackers are leveraging automation, AI, and reconnaissance to craft bespoke attacks that bypass static defenses. The old “block once, protect forever” model is collapsing.
Breakthrough threats like QR codes, SVGs, and LOTS attacks represent a significant evolution from traditional single-vector attacks, requiring security teams to implement strategies that can detect and respond to complex attack chains.
BEC and related social engineering attacks continue to represent the highest financial cybercrime risk to most organizations, with clear industry-specific targeting and patterns emerging.
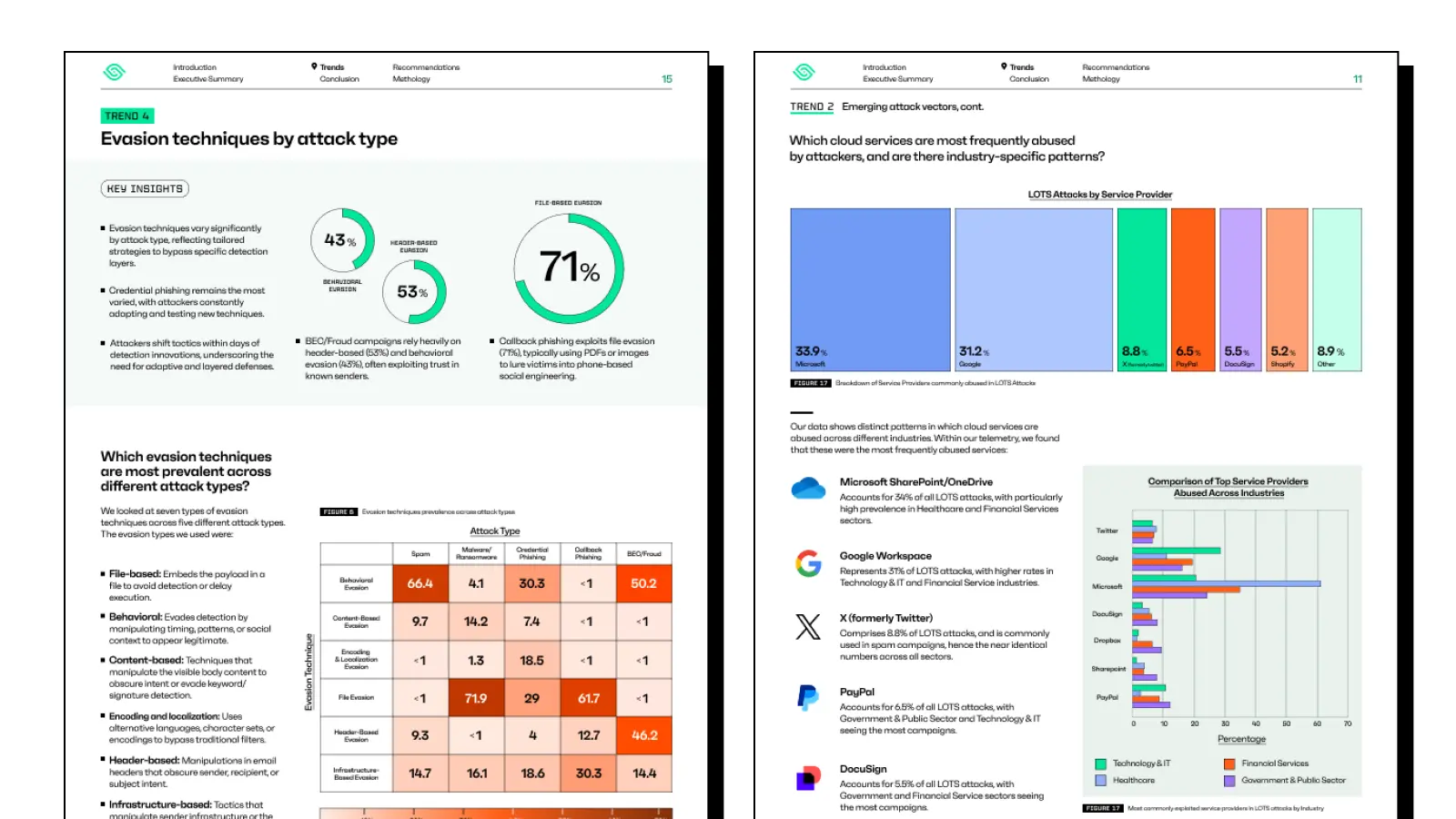
Evasion techniques vary significantly by attack type, reflecting tailored strategies to bypass specific detection layers. Attackers are not just changing payloads, they’re changing how they hide their delivery. For example, 71% of callback phishing exploits attachment-based evasion, typically using PDFs or images to lure victims into phone-based social engineering.
The complexity of email-based attacks continues to increase as threat actors combine multiple evasion techniques in a single campaign. This "evasion stacking" significantly reduces traditional detection rates and it has been observed across all major attack types.
As attackers continue to evolve their techniques at an accelerating pace, security practitioners must embrace adaptive, intelligence-driven approaches that can respond quickly to emerging threats and anticipate future developments.
Sublime is an adaptive email security platform built for the way attackers operate today. Rather than waiting on signature updates or model refreshes, Sublime continuously analyzes detection signals from your environment, generates new coverage in near real time, and automatically validates it against historical data – without waiting on manual retraining.
Want to dive deeper? Read the full Sublime Email Threat Research Report (Q1 2025) to explore the data and insights shaping the future of email security.
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)