December 4, 2024

Catch malicious email messages sent from sites that have been compromised by an AnonymousFox attack.
AnonymousFox is a threat actor group that has been active since 2019, specializing in the creation of tools that exploit plugin vulnerabilities across various CMS platforms, including WordPress, Drupal, Joomla, and OpenCart. Since then, there have been a wide variety of resources available showing how the hack works, how to detect it, and how to fix it. But even with widespread prevention information, this attack hasn’t gone away.
Recently, we’ve seen an uptick of activity with our AnonymousFox indicators Detection Rule. That means sites are still being compromised and used to further distribute the attack. Sublime is able to keep malicious messages sent by compromised servers out of mailboxes. Before we look at how we do it, here’s a quick refresher on how AnonymousFox works.
Once AnonymousFox is able to exploit a plugin vulnerability, the group's suite of tools (FoxAuto, Fox Ex, Fox RSF, Fox-CGI, etc.) grants the attacker complete control over the website(s) and enables a range of malicious activities. These activities include resetting passwords, uploading scripts, installing mailers, hosting files, and more.
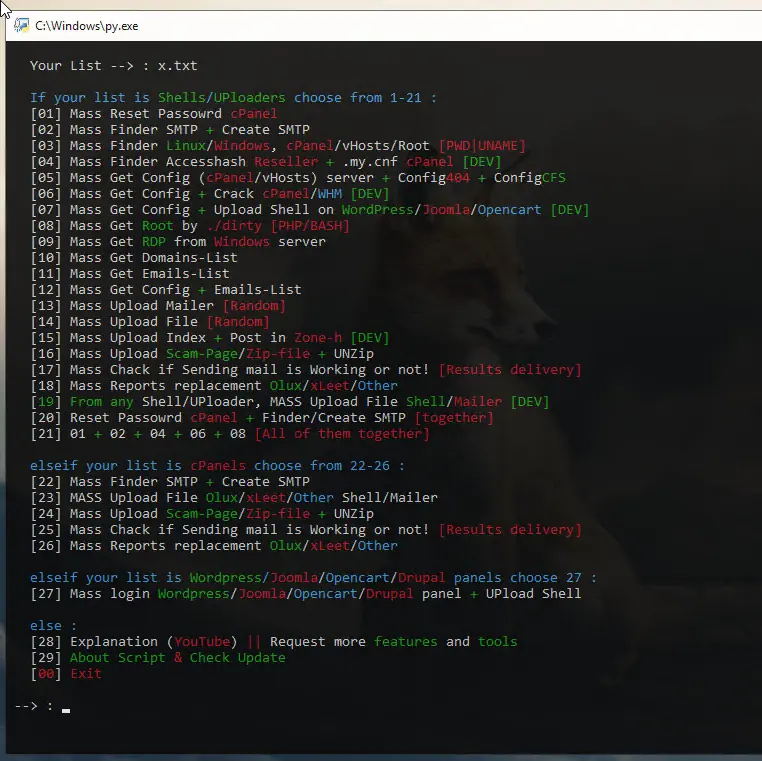
With control over the site, the attackers can easily distribute malware and phishing links using a variety of methods, including PHP mailers and hacked email accounts that use standard SMTP to send out messages. This allows them to bypass spam filters and leverage the reputation of the compromised site(s) to send out malicious email campaigns.
We've seen a wide range of variants, but generally, the email messages sent from compromised servers are straightforward, plaintext fraud attempts. Here's an example of one of these attempts:
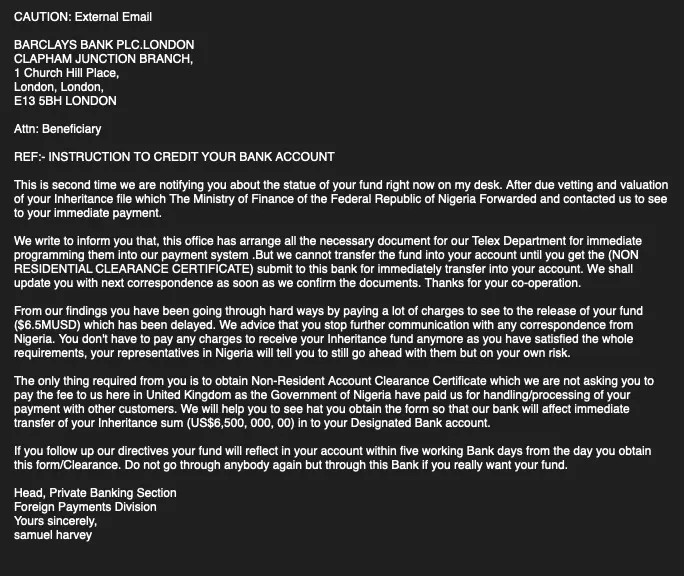
These methods listed above tend to leave behind artifacts or anomalies in the message headers, such as the presence of "anonymousfox" or "smtpfox" in the local component of various authentication email headers. Depending on the configuration, one of those artifacts may even appear as the sender email address. For example: X-Authenticated-Sender: smtpfox-1aevb@example.com
Sublime’s AI-powered detection engine is able detect these malicious messages and thereby reduce the attack’s spread. This prevention is enabled right out of the box, but in this post we’ll take a deeper dive into the Message Query Language (MQL) and signals used to detect these malicious emails:
This AnonymousFox rule uses the following logic:
type.inbound to filter down to inbound emails.any function to iterate over the hops and fields of the email headers.X-Authenticated-Sender or X-Sender that contain "(anonymous|smtp)fox-" in their values.or operator is used to also search for the sender email address containing “(anonymous|smtp)fox-".AnonymousFox is still a threat, and as it evolves, so will we. Sublime uses a combination of open-source detection rules and AI-powered techniques to detect and prevent threats like this one.
Start your free Sublime account today (managed or self-managed) to keep AnonymousFox out of your inbox. Book a live demo if you have any specific questions for our team.
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)