June 26, 2024
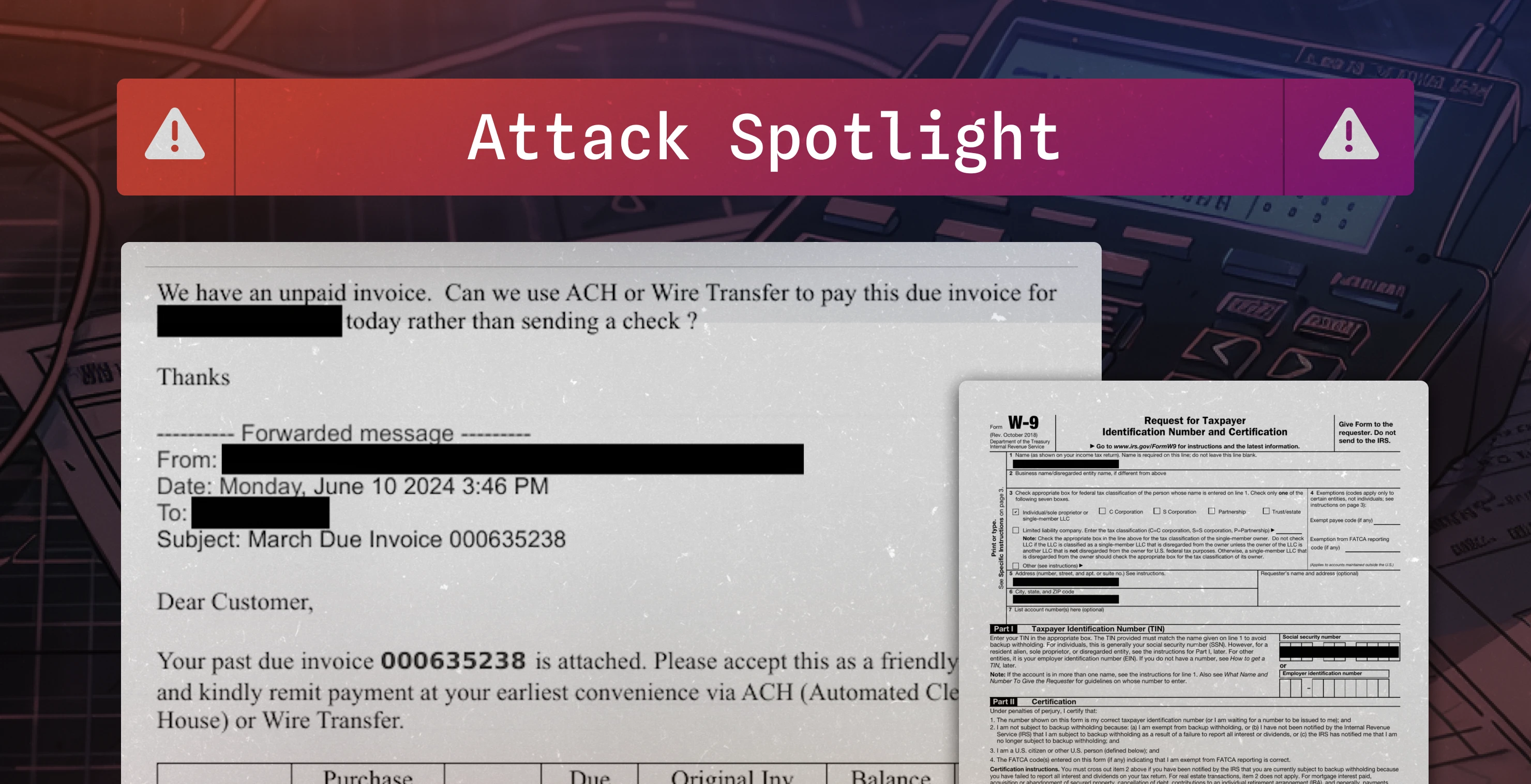
Sublime Security Attack Spotlight: Attempts to conduct fraud by soliciting a payment for a seemingly legitimate overdue invoice.
Sublime’s Attack Spotlight series is designed to keep you informed of the email threat landscape by showing you real, in-the-wild attack samples, describing adversary tactics and techniques, and explaining how they’re detected.
EMAIL PROVIDER: Microsoft 365, Google Workspace
ATTACK TYPE: BEC (Business Email Compromise)
Attempts to conduct fraud by soliciting a payment for a seemingly legitimate overdue invoice. Messages are highly personalized and targeted:
The attached PDF also contains a fabricated W-9 form with a fake SSN, signed by a fictitious persona. Attachment: Inv no# 000635238.pdf.

Sublime detected and prevented this attack using the following top signals:
Sublime detects and prevents BEC and other email based threats. Deploy an instance in alert-only mode.
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)