June 25, 2025

Phishing attack leveraging the X/Twitter link shortener to hide a malicious link
Sublime’s Attack Spotlight series is designed to keep you informed of the email threat landscape by showing you real, in-the-wild attack samples, describing adversary tactics and techniques, and explaining how they’re detected. These attacks can be prevented with a free Sublime account.
EMAIL PROVIDER: Google Workspace
ATTACK TYPE: Credential Phishing
In Q1 2025, we observed X (formerly Twitter) to be the third-most abused platform for Living Off Trusted Sites (LOTS) attacks (read the full threat report). The most common way we see X abused is through the use of its t[.]co link shortener for disguising malicious links. In a recent attack, we saw a bad actor using the t[.]co shortener to deliver an AITM credential phishing payload.
The attack starts with a brief email impersonating a secure message notification. The message is from a “DocuSign-Account” display name at the edocs[.]com domain and features language lifted from a Citrix ShareFile notification. To add legitimacy, the local part of the sender email address includes the local part of the recipient email address. The message subject indicates that the target has an encrypted message about EFT/ACH (direct deposit acronyms) waiting for them.
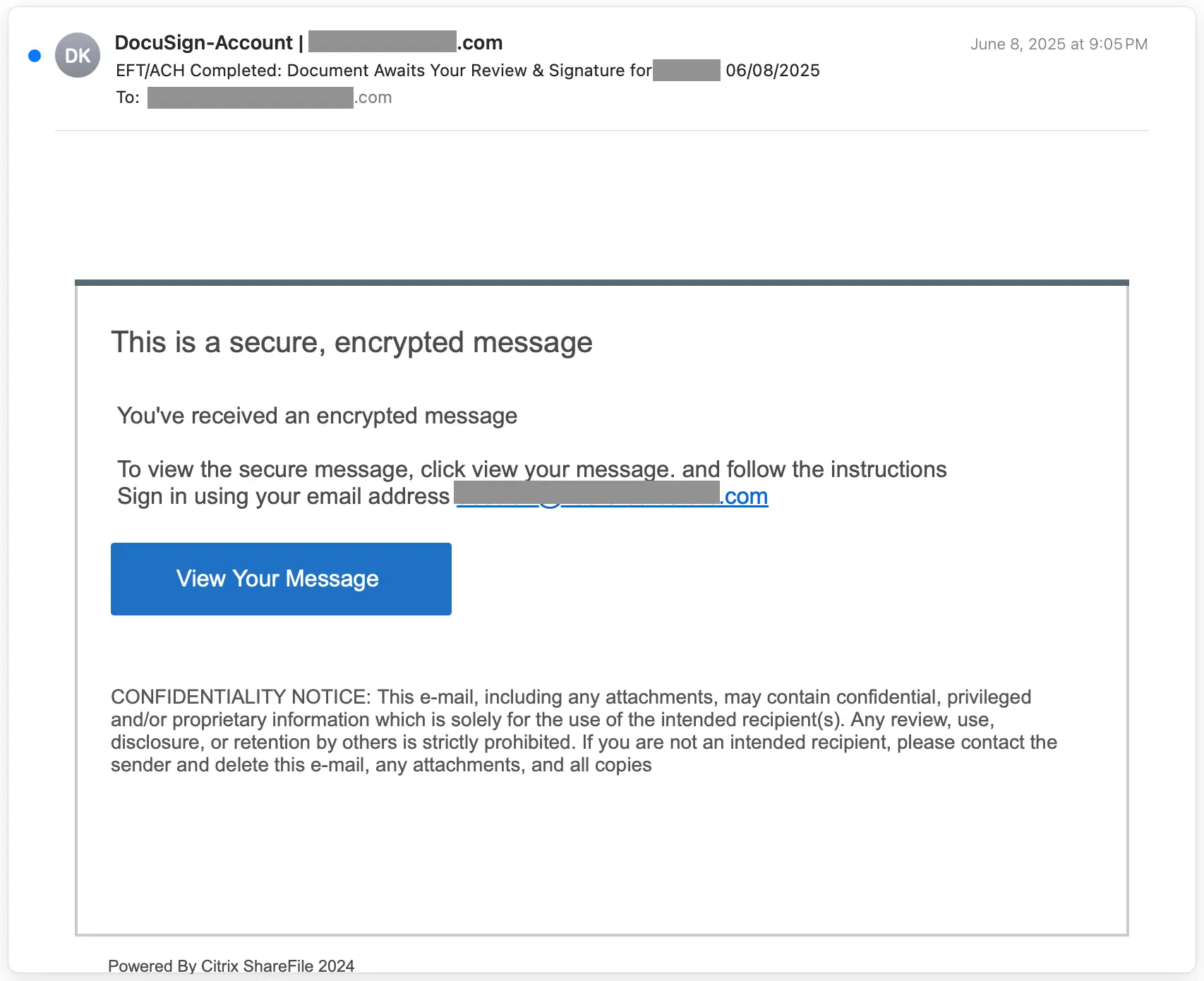
If the target clicks View Your Message, they are taken to a t[.]co-shortened URL that redirects to a firebasestorage.googleapis[.]com site. This page is the AITM credential phishing payload. It features both Adobe and Microsoft brand impersonation.
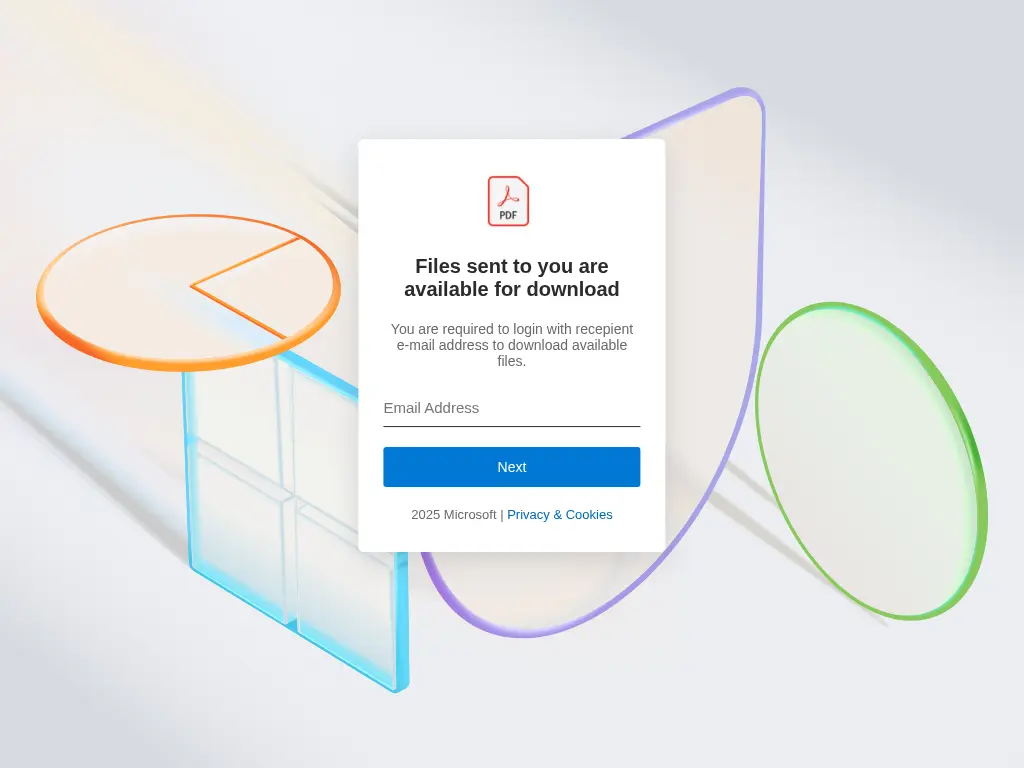
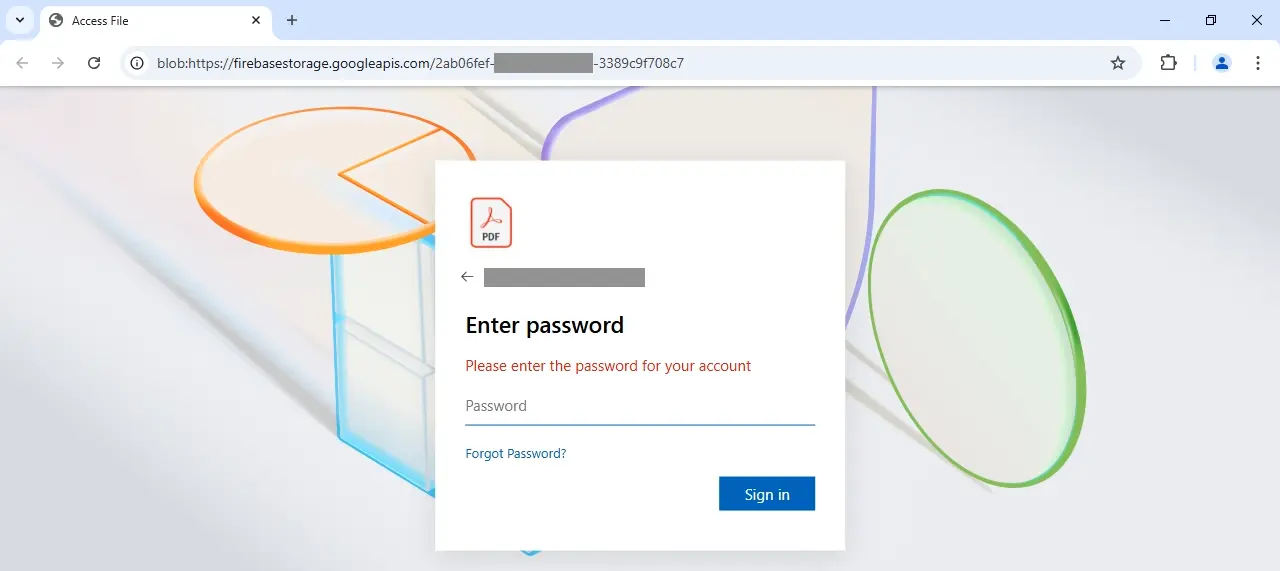
If the target enters their email address in an attempt to download the financial PDF, the AITM attack begins. All credentials are passed from this login page to an actual Microsoft OAuth server, but are harvested by the attacker as well.
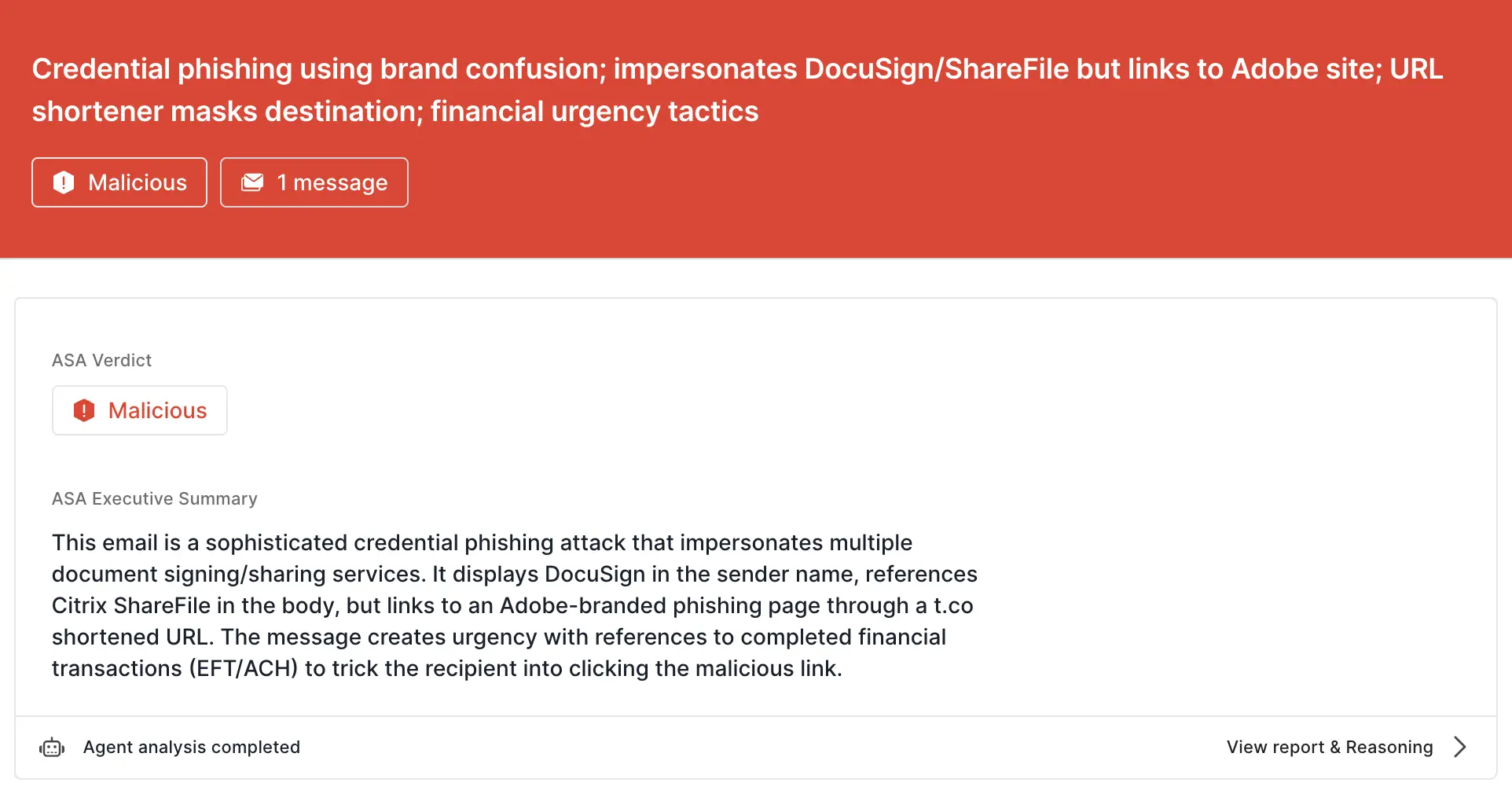
Sublime's AI-powered detection engine prevented this attack. Some of the top signals for this attack were:
ASA, Sublime’s Autonomous Security Analyst, flagged this email as malicious. Here is ASA’s analysis summary:
LOTS attacks are popular because they let bad actors hide behind friendly domains. That’s why the most effective email security platforms are adaptive, using AI and machine learning to shine a spotlight on seemingly minor discrepancies.
If you enjoyed this Attack Spotlight, be sure to check our blog every week for new blogs, subscribe to our RSS feed, or sign up for our monthly newsletter. Our newsletter covers the latest blogs, detections, product updates, and more.
Read more Attack Spotlights:
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)