September 4, 2025
Using a meeting request confirmation email to callback phish targets on a distribution list
Adversaries use legitimate automatically generated messages to evade security. To boost blast radius, they’ll have notification and confirmation emails sent to a distribution list, hitting hundreds or thousands of targets at once. We explored this a while back in our post on callback phishing via invoice abuse and distribution list relays.
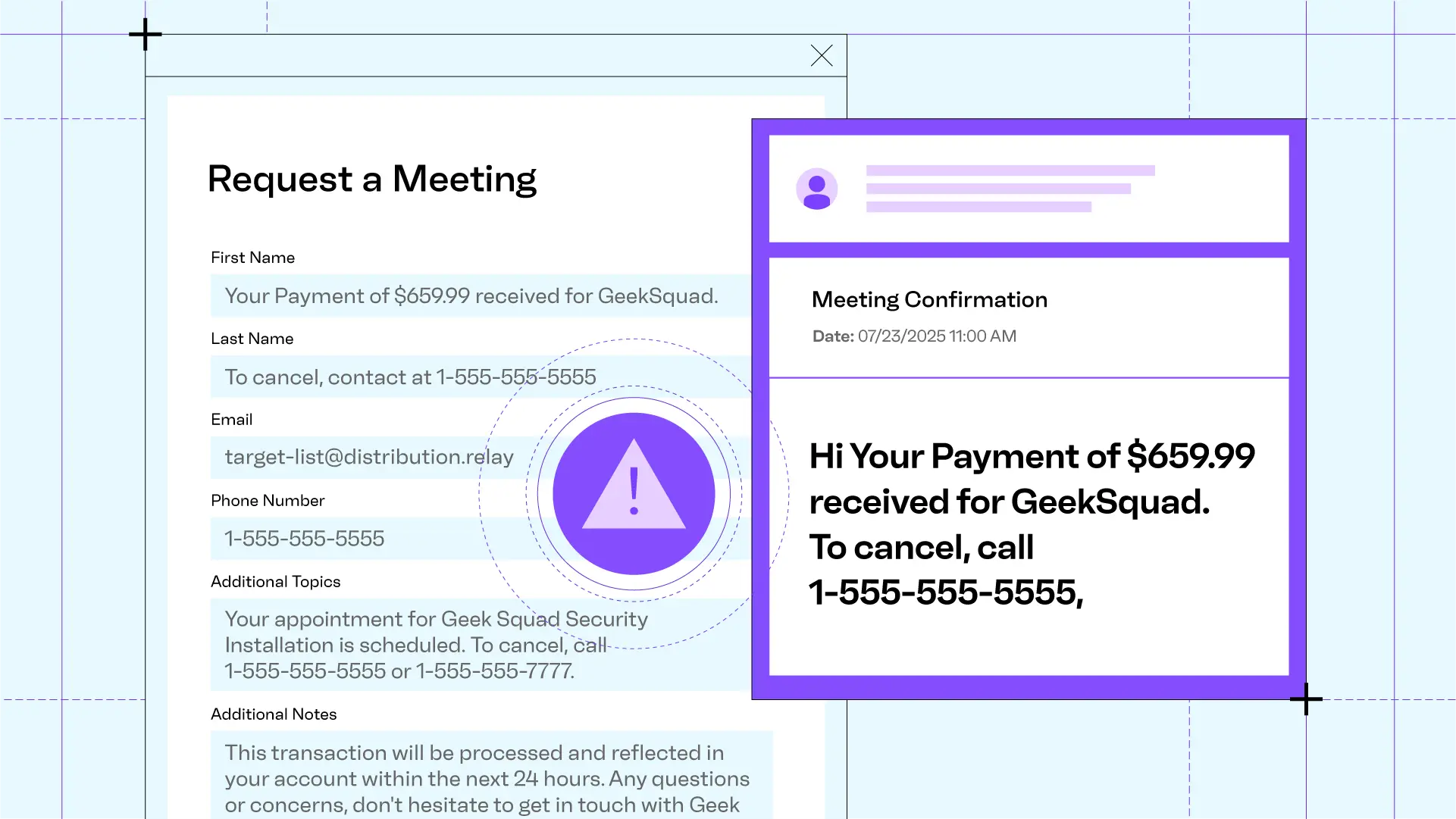
We’ve recently seen an uptick in attacks where online appointment forms are used as the mechanism for launching the attack. In a specific attack, we saw an adversary use a bank’s “Request a Meeting” form to spread a financial-related callback phishing attack. We’re going to look at how this attack worked piece by piece, but let’s start with the whole email (the bank has been redacted from the message):

This is a legitimate, autogenerated meeting confirmation message and it contains a mix of templated fields and user responses. The goal of the attack is to get the recipient to call on of two phone numbers. Combined, the numbers appear six different times in this message, along with urgent financial language.
Let’s look at what the attacker filled in or selected for each to make this email
The first name and additional topics fields set up the financial scam. The additional notes field sets a ticking clock to create urgency. The last name, telephone number, additional topics, and additional notes fields provide the callback scam phone number to reach out to to close this urgent financial issue. Finally, the attacker provided a distribution list email as their personal email address, so the notification is sent to every target on the list. And because the notification email is routed through a distribution list relay, the sender email address remains original bank email address, so it arrives without any DMARC, DKIM, or SPF authentication failures.
This is a fast, repeatable attack that only requires a distribution list, callback numbers, and a few lines of text. Additionally, as it is being delivered from a legitimate domain that the target may have previously corresponded with, the attack is less likely to be flagged as suspicious or malicious.
Sublime's AI-powered detection engine prevented both of these attacks. The top signals for these attacks were:
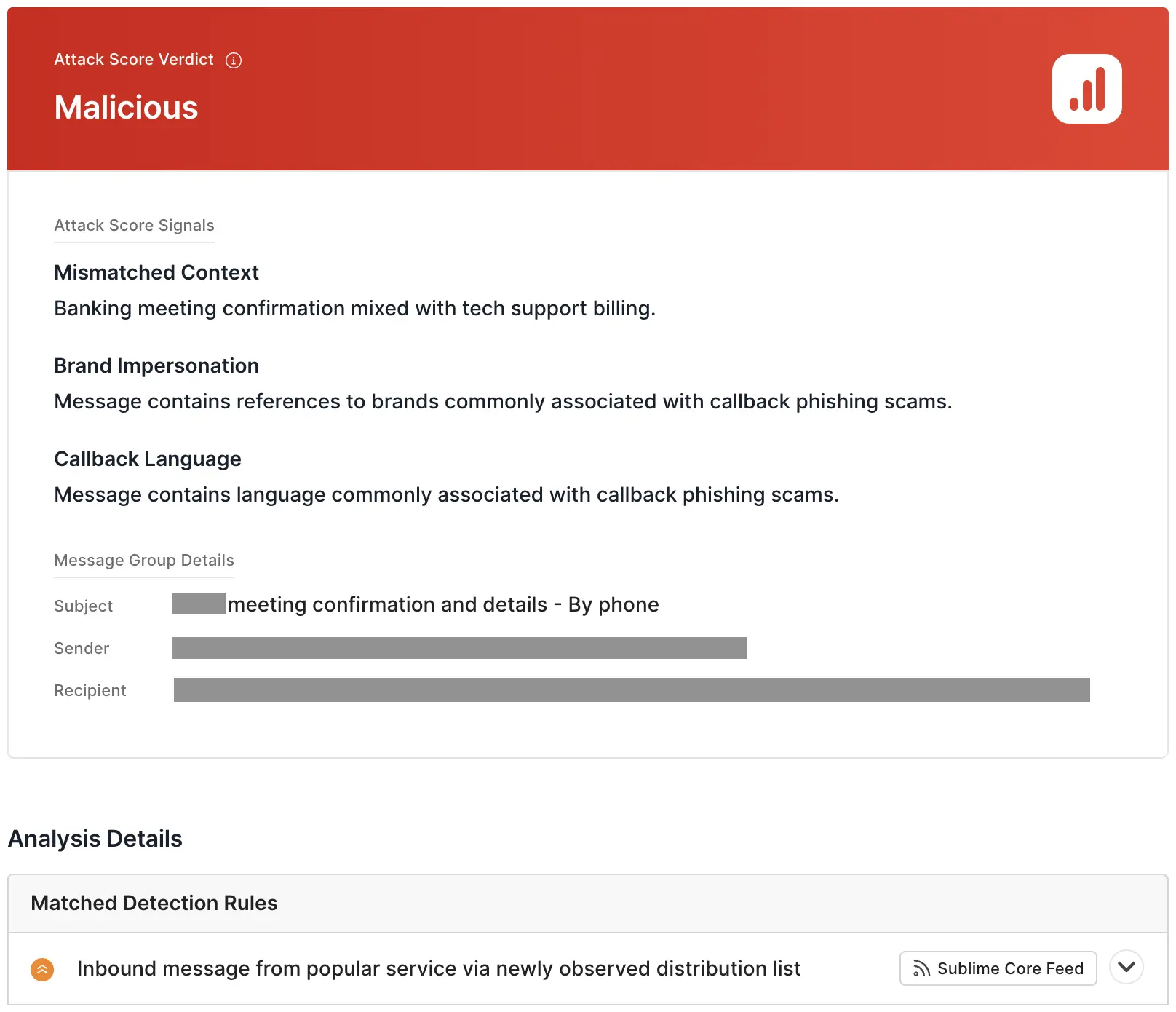
See the full Message Query Language (MQL) that detected this attacks in the publicly available Rule in the Core Feed: Inbound message from popular service via newly observed distribution list.
Bad actors will abuse legitimate resources in order to hide behind friendly domains. That’s why the most effective email security platforms are adaptive, using AI and machine learning to shine a spotlight on seemingly minor discrepancies.
If you enjoyed this Attack Spotlight, be sure to check our blog every week for new blogs, subscribe to our RSS feed, or sign up for our monthly newsletter. Our newsletter covers the latest blogs, detections, product updates, and more.
Read more Attack Spotlights:
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)