February 22, 2023
Sublime is the world’s first open email security platform that lets anyone write, run, and share rules in a universal domain-specific language (DSL) to block email-borne attacks, hunt for threats, and more.
There’s osquery/EDR for endpoints, YARA for binaries, Sigma/EQL for logs, Semgrep for code, Snort/Suricata for packets. Now, there’s Sublime for email.
After building and iterating behind closed doors, working hand-in-hand with many of the top security teams in the world, we’re excited to announce that Sublime Platform is now generally available and free to use by any security team, analyst, or researcher.
We’re also happy to share that we’ve raised $9.8M in funding, led by Decibel Partners and Slow Ventures with participation from other veteran security operators and founders, to continue investing in platform capabilities and our community.
OneNote attachment command execution. HTML smuggling links. Full-page captcha redirects. Display name spoofs. Callback scams.
The email threat landscape is constantly evolving. Seemingly every week, attackers find ways to evade email security controls and land in user inboxes to deliver malware, ransomware, steal credentials, or make fraudulent wire transfers. Whether nation-state or organized crime, one thing is clear: email is still one of the most effective initial access vectors.
Before Sublime, I spent years breaking into organizations via email. I re-used the same techniques month after month. In 2018, I started to leverage high-reputation mass mailers and free file hosting providers to deliver VBA macro-laced Word docs, prompting users to “enable macros to see content.” All I had to do was rotate infrastructure and adjust macro evasions from time to time, but the technique stayed the same for years. This worked. Every. Time.
And there are real world consequences, like preparing the battlefield before a ground invasion and ransomware attacks on hospitals.
Our big realization was this: security teams could do very little to prevent the same attacks from landing again and again. They had no control over their email environments, and would do what they could to close off attack surface in the ways they could: write detection and response rules in their EDR, disable macros on certain endpoints, enforce hardware MFA where possible.
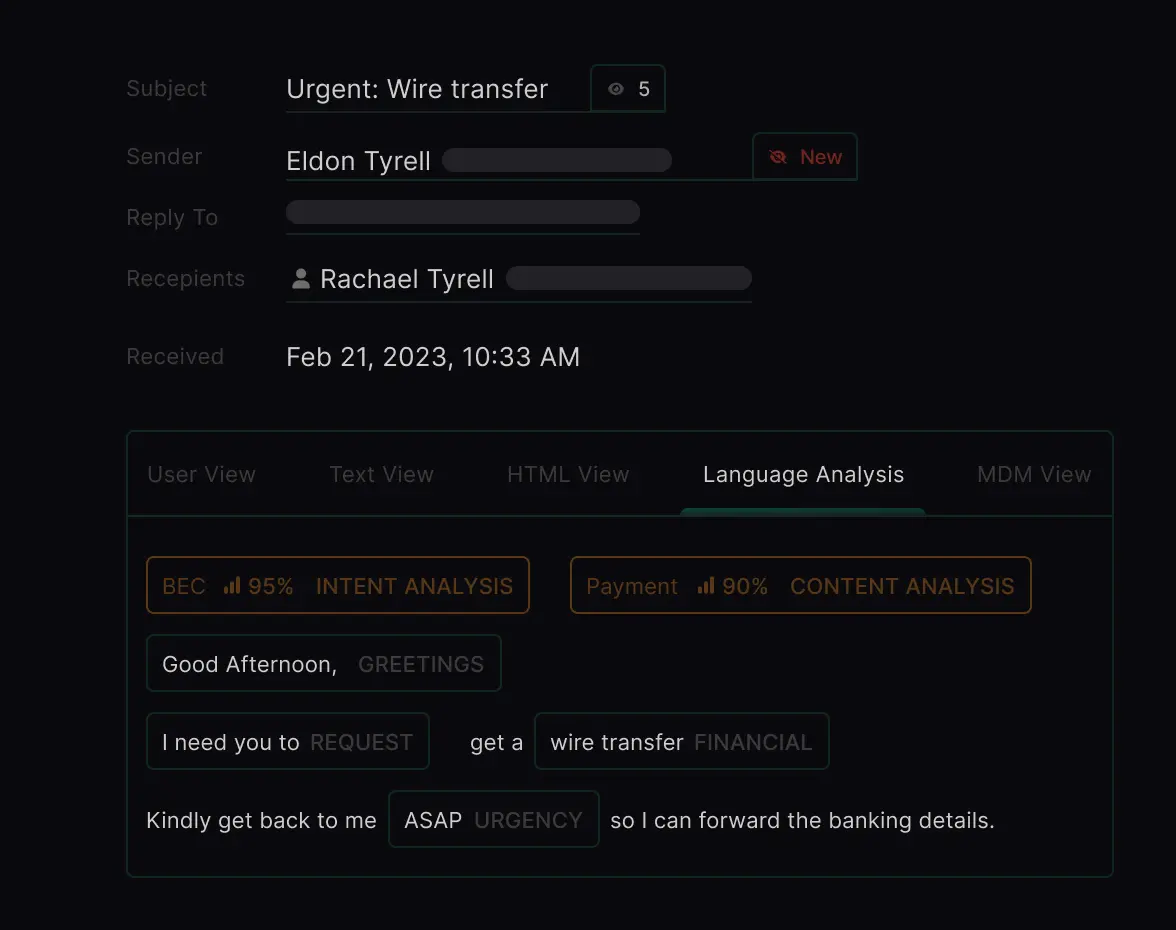
But adversaries evolve, and now there are attacks without links or attachments to siphon money and steal sensitive data (BEC), targeting of users who have macros enabled (hello Finance team 👋), callback scams that entice users to call a support line and “download and run a support administration tool.” The list goes on. And they’ll continue to evolve.
Traditional email security is a black-box walled-garden.
Security is a cat and mouse game, and until today email security vendors were the only ones playing cat.
Defenders know their environments better than anyone, they live and breathe it every working hour of every day. Yet our industry hasn’t empowered defenders to truly capitalize on that knowledge in email — until now.
Sublime’s Message Query Language (MQL) is the first universal domain-specific language (DSL) that works across email providers, and was purpose-built for describing attacker behavior in email.
Giving defenders a common language for control and collaboration isn’t a new concept: there’s osquery/EDR for endpoints, YARA for binaries, Sigma/EQL for logs, Semgrep for code, Snort/Suricata for packets.
"I’ve been waiting for years for someone to bring detection engineering to email. I haven’t been this excited since EDR/Crowdstrike." - Bob W., Detection & Response Manager at G2000
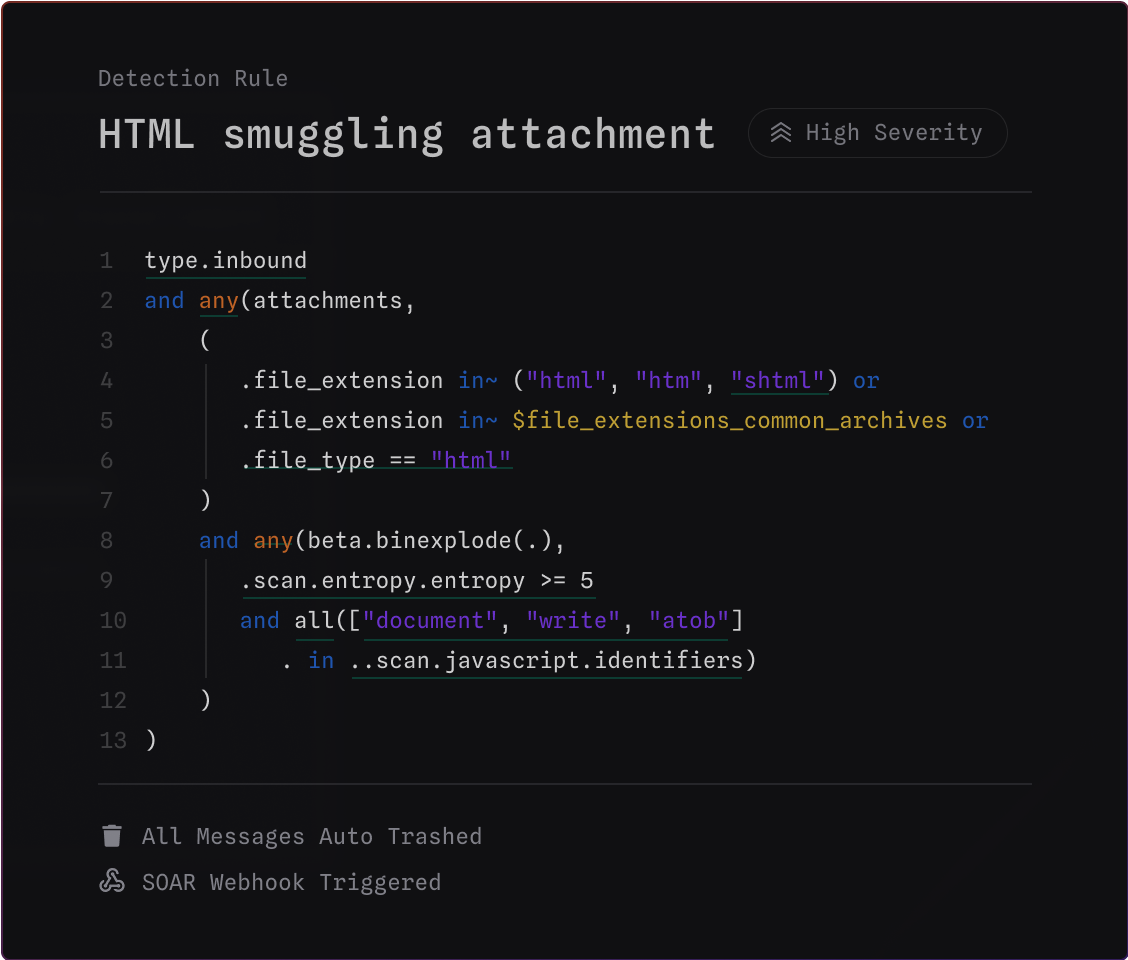
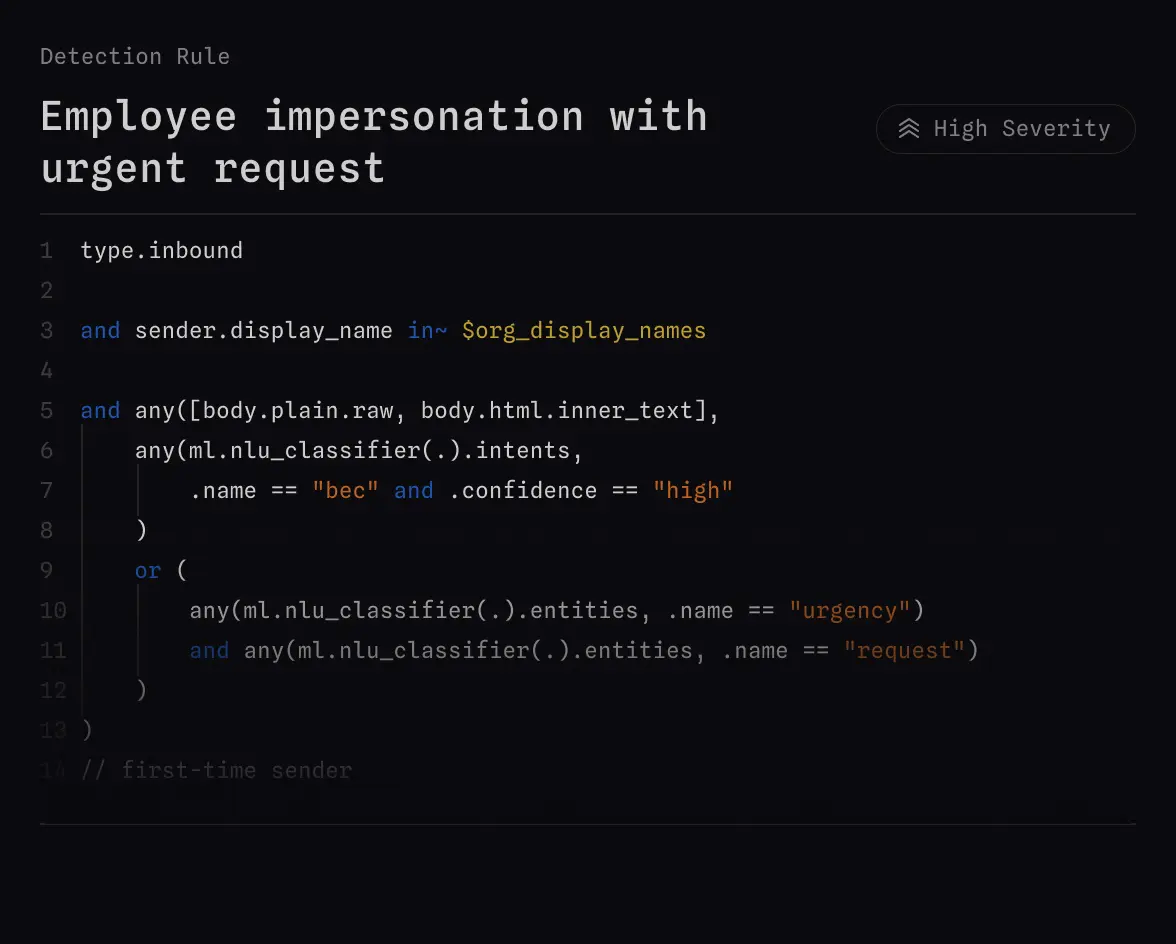
You can use MQL to block everything from HTML smuggling attacks to low-volume, high sophistication BEC attacks.
MQL uses a structured representation of an email message and can leverage any number of signals and functions like recursive file explosion, Natural Language Understanding (NLU), YARA signatures, organizational context, sender history, Link Analysis and Computer Vision (CV), VBA macro classification, Levenshtein distance, and more.
Check out the sublime-rules GitHub repo for more default protections. Fun fact: one third of these detection rules were contributed by the community. Special thanks to @ajpc500, @vector_sec, @Kyle_Parrish_, @amitchell516, @jkcoote, and others for their detection contributions that have blocked attacks that targeted organizations ranging from Fortune 500 companies to local family businesses.

In the security industry, we’re all fighting a common enemy. Sharing and collaboration are a part of our DNA. Whether publicly on Twitter, or behind closed doors on private mailing lists or in Slack groups, sharing TTPs and IOCs is the norm.
We wanted to give organizations a way to easily operationalize all this sharing, but a couple things have to be true for that to really work:
By empowering the community to work together more effectively, we can unlock the potential to innovate and adapt faster than attackers. When one person writes and shares a rule, it benefits others. There’s no bottleneck.
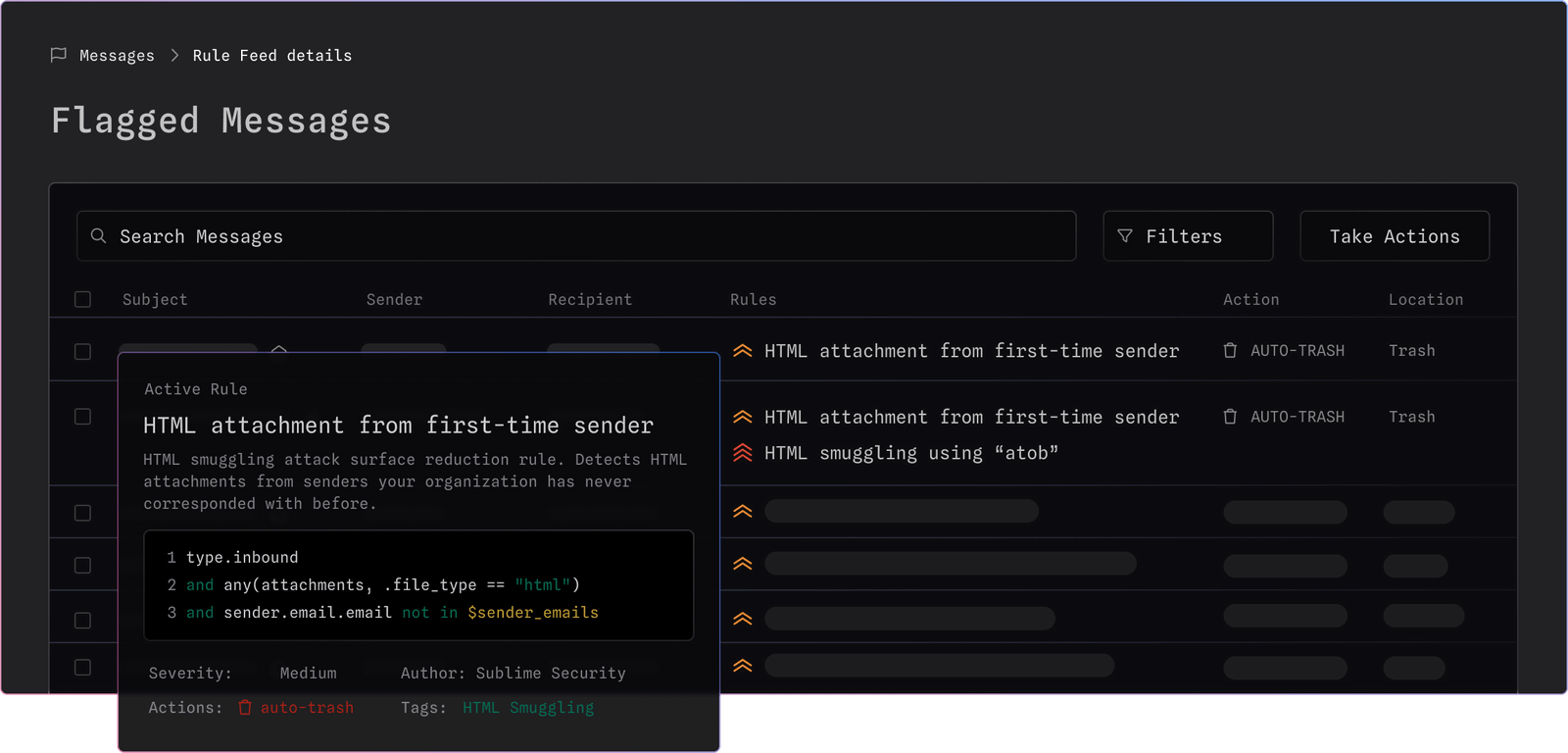
We’ve seen this play out dozens of times already: detection rules shared by Sublime users to combat new attacker techniques — like this rule made in response to the recent rise in OneNote attachment phishing — have been deployed to dozens of other organizations and helped keep them safer.
As of today, anyone can deploy their own Sublime instance using Docker or Cloud-native options in minutes — for free. For folks who want an instance managed by the Sublime team, we also offer paid SaaS and Enterprise versions.
Ultimately, end users are not at fault when they click on a phishing link or open a malicious attachment. Email attacks are sophisticated, and even technical users can be deceived.
The traditional black box approach to email security fails to take advantage of the expertise and context that security professionals have. Sublime lets defenders protect their organizations without one hand tied behind their backs.
That’s why our mission at Sublime is clear: to create a safer internet where defenders take back the advantage.
It’s Day 1.
We couldn’t have gotten here alone. Thank you to our amazing customers, community, advisors, and investors who believed in us early and have continued to support us.
We’re grateful to our lead investors, Decibel and Slow, as well as the experienced operators and angel investors who also contributed to our funding. In alphabetical order, they are:
Jerry Perullo (Former CISO, NYSE and former Chairman of the Board, FS-ISAC), Justin Label (Inner Loop Capital), Kevin Patrick Mahaffey (Founder, Lookout), Leo Polovets (Partner, Susa Ventures), Marty Roesch (Creator of Snort and Founder, Sourcefire), Michael Sutton (Former CISO, Zscaler), Oliver Friedrichs (Founder of Phantom Cyber and Pangea), Pete Koomen (Co-founder, Optimizely), Rama Ranganath (Director, Google), Rishi Bhargava (Co-founder, Demisto), Slavik Markovich (Co-founder, Demisto), Sounil Yu (Creator of Cyber Defense Matrix and former Chief Security Scientist, Bank of America).
And last but not least, none of this would exist without our incredible team: Jonathan, Jon, Cameron, Ross, Bobby, Alex, Madison, Hugh, AJ, Sumeet, Ben, Omar, and Sam. Thank you for believing in our vision and making it a reality.
And finally, thanks mom.
🤝
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)