October 8, 2025

Credential phishing scam targeting UK Visas and Immigration sponsors
Sublime’s Attack Spotlight series is designed to keep you informed of the email threat landscape by showing you real, in-the-wild attack samples, describing adversary tactics and techniques, and explaining how they’re detected. These attacks can be prevented with a free Sublime account.
EMAIL PROVIDER: Google Workspace
ATTACK TYPE: Credential Phishing
We have recently detected a large influx of credential phishing attacks targeting visa sponsors in the UK. These attacks start with emails that impersonate the UK Visas and Immigration (UKVI) department of the UK Home Office. The messages direct the target to fake Sponsor Management System (SMS) login pages that are used for credential phishing.
It is unclear who the attackers are or what their specific goal is, but based on the amount of messages detected by Sublime, it can be safe to assume that this is an organized effort. In this post, we’ll look at the attack, how it works, and possible goals of the attackers.
While the attack email has many variants, they all share the goal of getting the target to log in to their SMS account. Each message conveys a sense of urgency, often asking the target to review a notification, an approaching expiration, or an upcoming security review.
Within the messages, there are typically references to needing either Level 1 or Level 2 SMS accounts. In some cases, the message directs the recipients to forward the message to a Level 1 or Level 2 SMS account holder if the message reached them incorrectly. Incidentally, many of these messages were sent to targets without those accounts.
Additionally, the payload URL is obfuscated behind a button or an official-looking link. These evasions can be seen in the below examples, including the hover text to the payload URL:
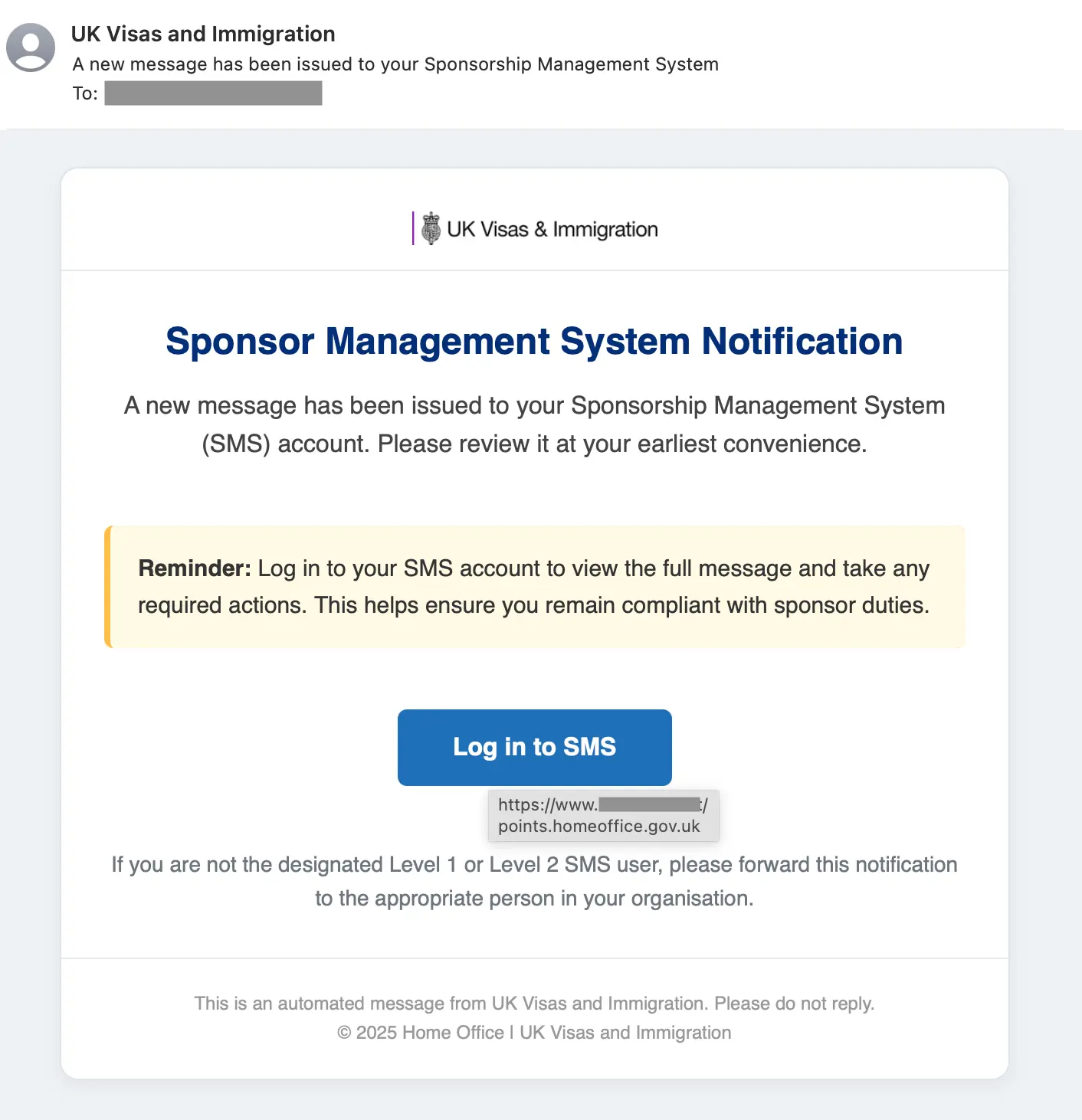
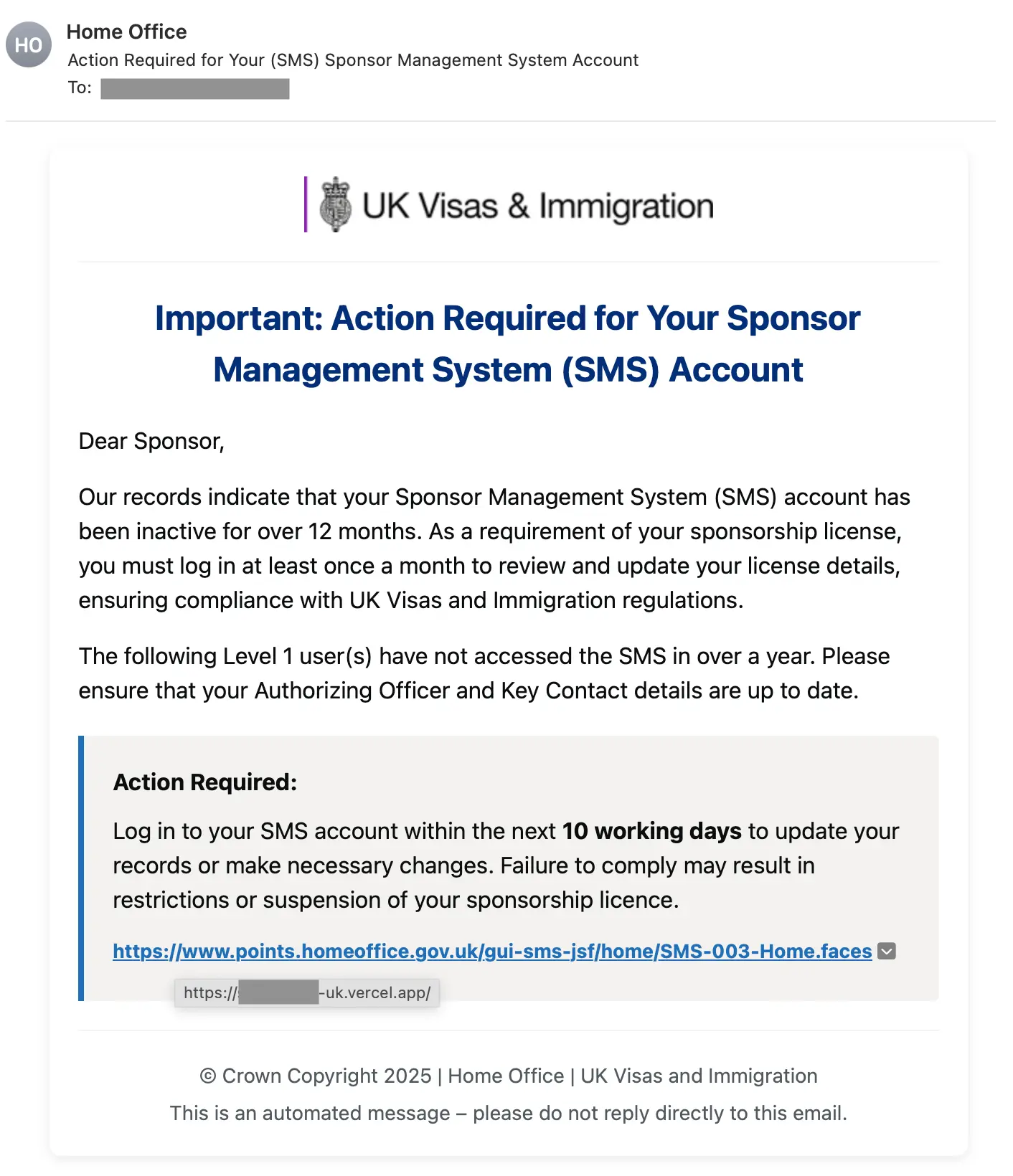
After clicking on the link, the target is taken to a credential phishing page that is an imitation of the UK Home Office SMS login page. The official page is hosted on points.homeoffice.gov[.]uk, and many of the attack pages reference that address within their page URL or path.
In some cases, the target is first taken through a challenge page before reaching the phishing page:
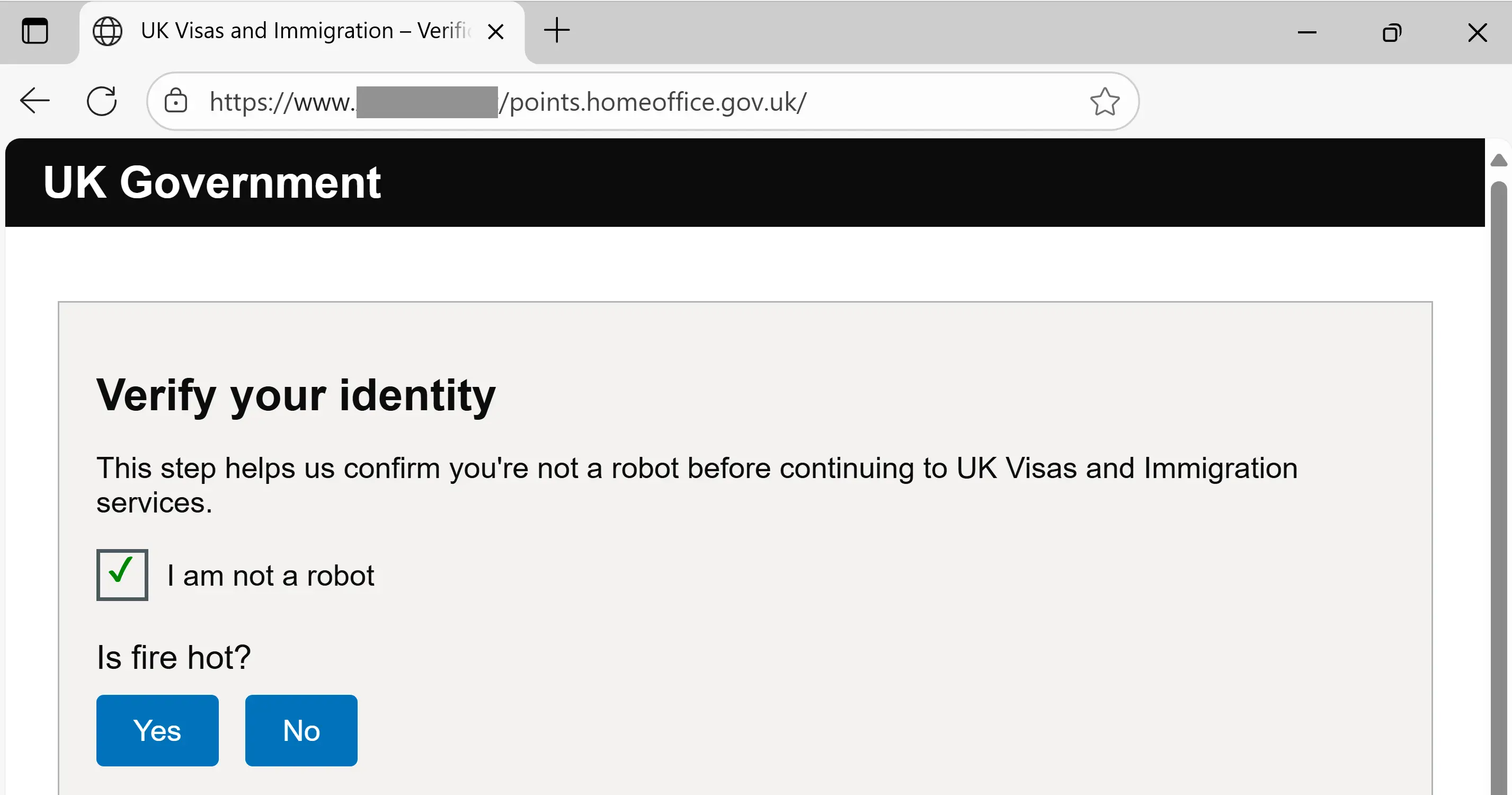
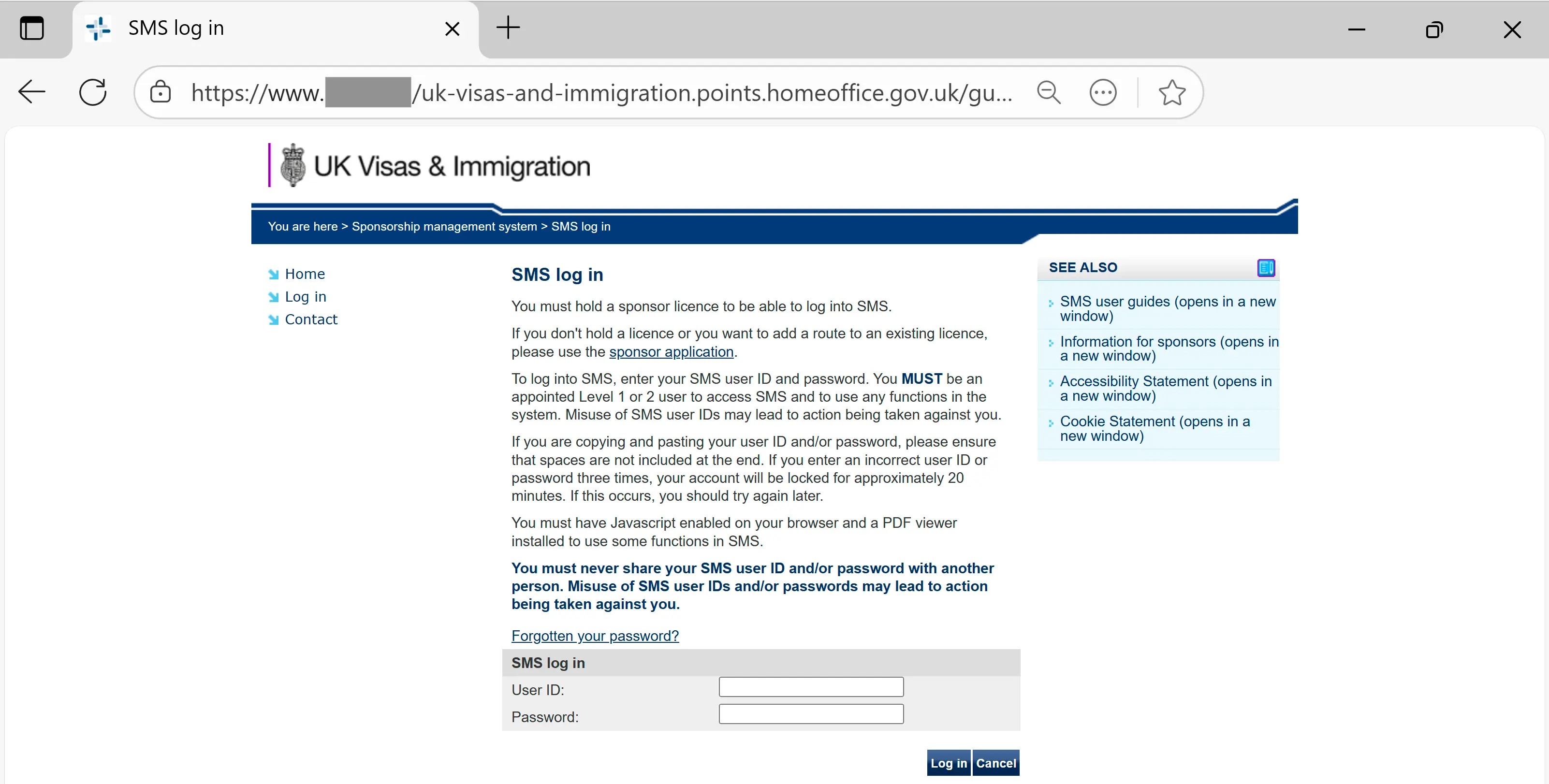
Looking at the source code of this page, we can see that the login portion is actually a form that submits the credentials to a sms.php processing script.
The phishing page has been observed across a wide variety of domains. Some of these attacks are hosted on compromised domains (instead of attacker-owned or free). This tactic is used to evade security scanning that looks at domain trustworthiness (in some cases, compromised .org domains). By only adding one page to the compromised site and then not returning, an attacker could considerably decrease chances of detection.
This activity targets highly sensitive, identity-linked systems and poses significant risk to individuals, organizations, and possibly even national security:
At present, Sublime’s Threat Research team does not attribute this activity to a known adversary. It is difficult to determine the exact motivation of these attacks without more information about the adversaries. A possible motivation is opportunistic financial gain, in which the attacker exploits the complexity and opacity of immigration systems in order to sell stolen identities/visas or extort their victims.
Sublime's AI-powered detection engine prevents these attacks. Some top signals for these attacks are:
homeoffice.gov[.]uk within the URL to imitate legitimacy.ASA, Sublime’s Autonomous Security Analyst, flagged this attack as malicious. Here is ASA’s analysis summary for one of the messages:
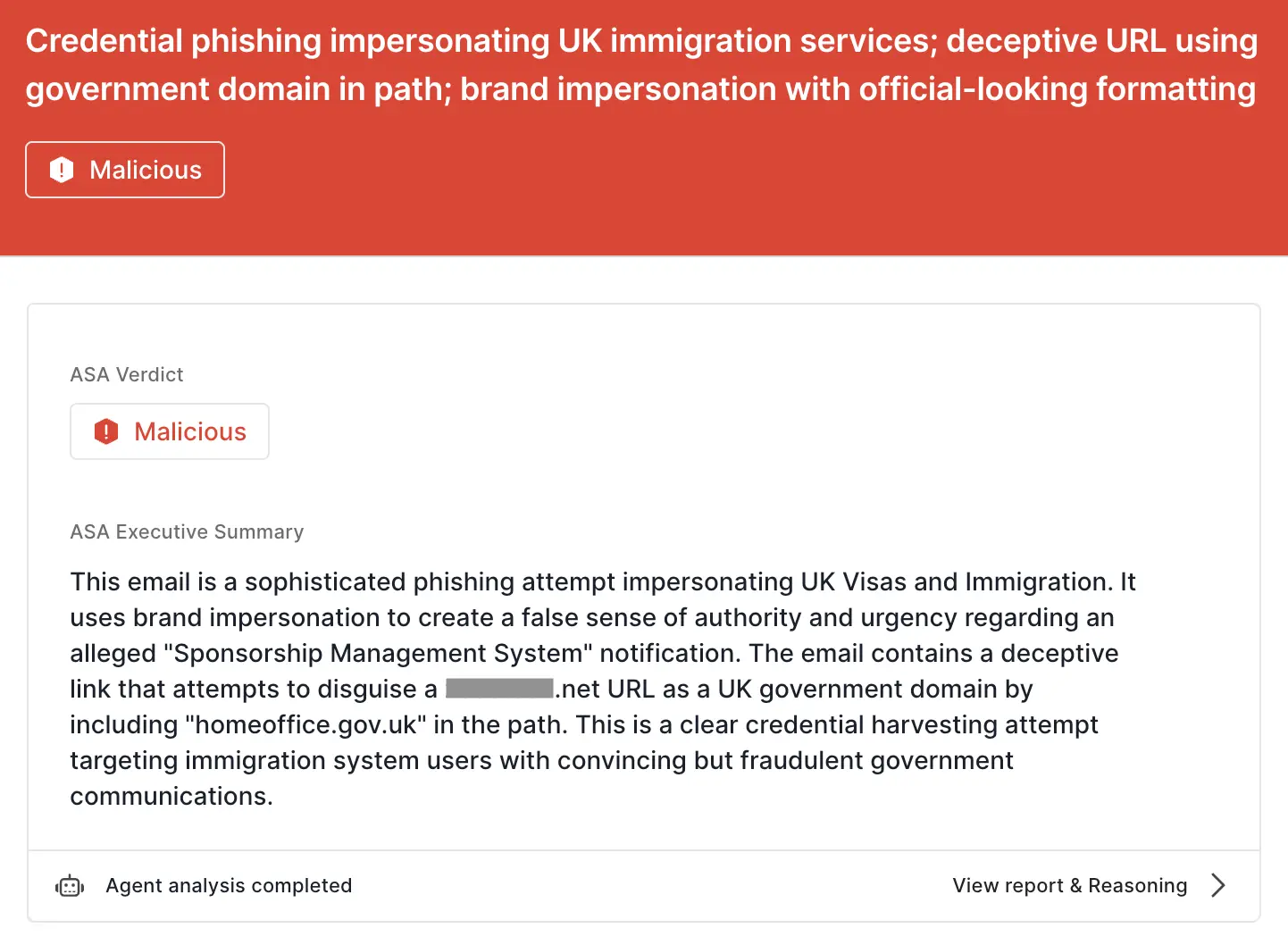
The quantity and variety of these attacks make it clear that adversaries will continue iterating on their assault. That’s why the most effective email security platforms are adaptive, using AI and machine learning to shine a spotlight on seemingly minor discrepancies.
If you enjoyed this Attack Spotlight, be sure to check our blog every week for new blogs, subscribe to our RSS feed, or sign up for our monthly newsletter. Our newsletter covers the latest blogs, detections, product updates, and more.
Read more Attack Spotlights:
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)