July 2, 2024

Sublime Security Attack Spotlight: Attempts to deliver malware by sending a fake purchase order.
Sublime’s Attack Spotlight series is designed to keep you informed of the email threat landscape by showing you real, in-the-wild attack samples, describing adversary tactics and techniques, and explaining how they’re detected.
EMAIL PROVIDER: Google Workspace
ATTACK TYPE: Malware/Ransomware
Attempts to deliver malware by sending a fake purchase order message. Attack characteristics:
Agent Tesla is a .Net-based Remote Access Trojan (RAT) and data stealer for gaining initial access that is often used for Malware-as-a-Service (MaaS). In this criminal business model, threat actors known as initial access brokers (IAB) outsource their specialized skills for exploiting corporate networks to affiliate criminal groups. As first-stage malware, Agent Tesla provides remote access to a compromised system that is then used to download more sophisticated second-stage tools, including ransomware.
Source
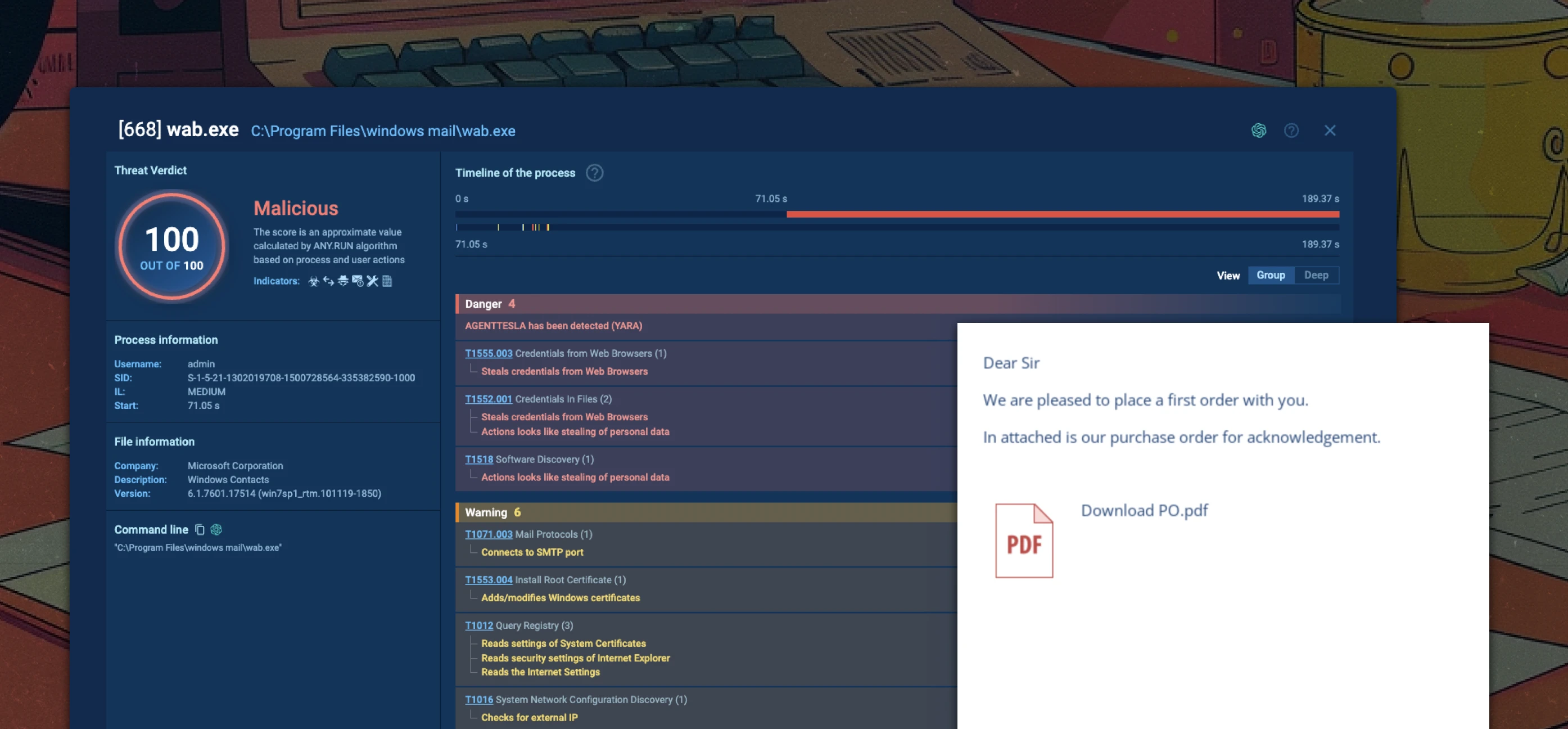
Sublime detected and prevented this attack using the following top signals:
Sublime detects and prevents malware/ransomware delivery and other email based threats. Deploy a free instance today.
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)