July 17, 2025
Credential phishing attack targeting Xfinity accounts delivered via Zoom Docs
Sublime’s Attack Spotlight series is designed to keep you informed of the email threat landscape by showing you real, in-the-wild attack samples, describing adversary tactics and techniques, and explaining how they’re detected. These attacks can be prevented with a free Sublime account.
EMAIL PROVIDER: Microsoft 365
ATTACK TYPE: Credential Phishing
A few weeks back, we’d reported that we’d seen an uptick in Zoom-based attacks. In that post, we saw a credential phishing attack targeting Microsoft users that leveraged Zoom Events and Zoom Docs. But credential phishing attacks aren’t only limited to Microsoft and Google. In a recent attack, we saw a bad actor impersonate Xfinity customer service to deliver a multipage attack that ultimately ended with a credential phishing payload.
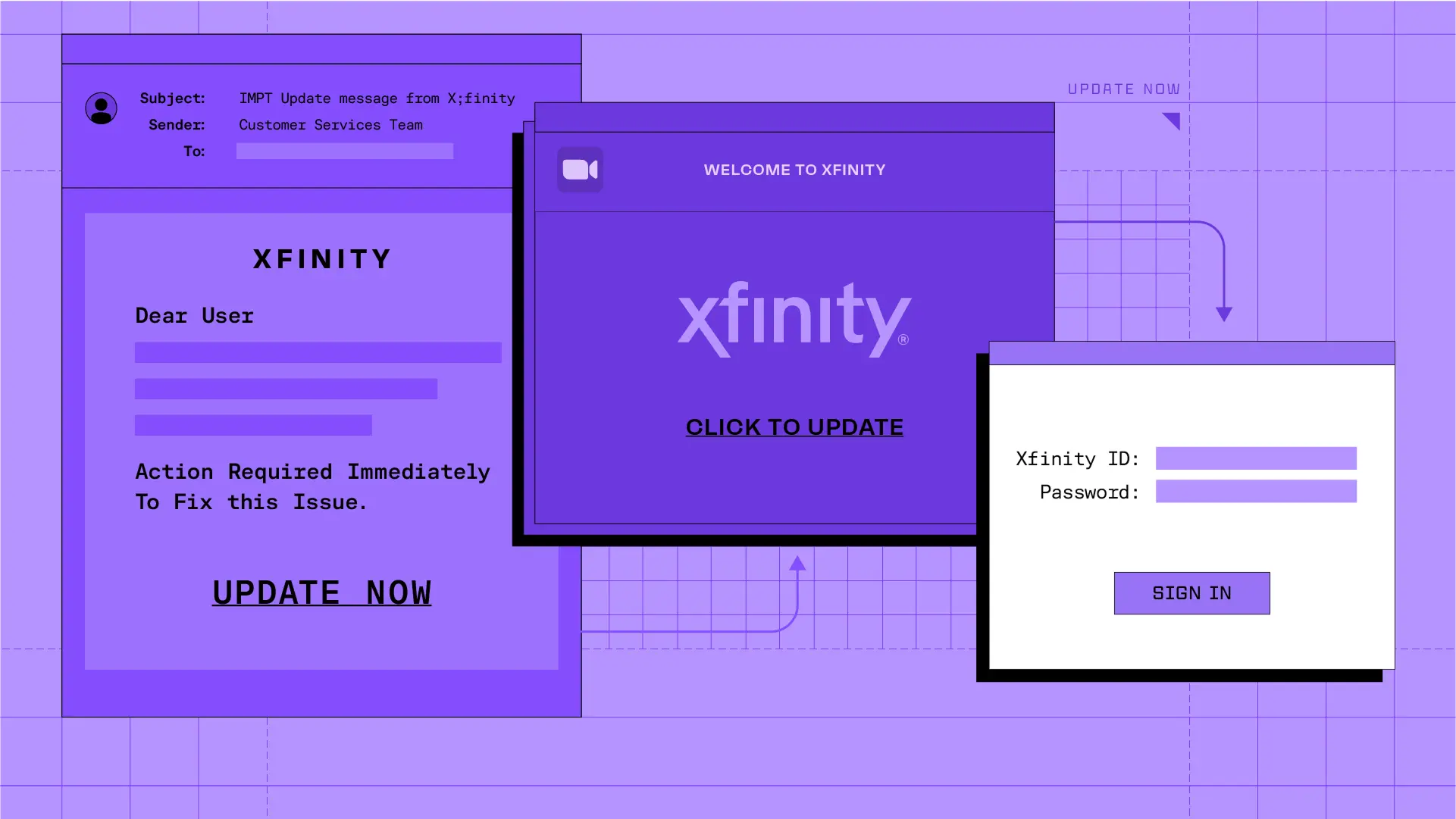
The attack started with an email sent from “Customer Services Team” and a body impersonating an Xfinity account notification. The subject and body contain character changes and typos to avoid detection. For example, a rule looking specifically for variants of “important” (denoting urgency) may miss “IMPT”, even though the recipient would likely understand the abbreviation.
Additionally, while the screenshot below only shows the sender’s display name (the default view for some email applications), the sender’s address is Gmail, not Xfinity or Comcast.

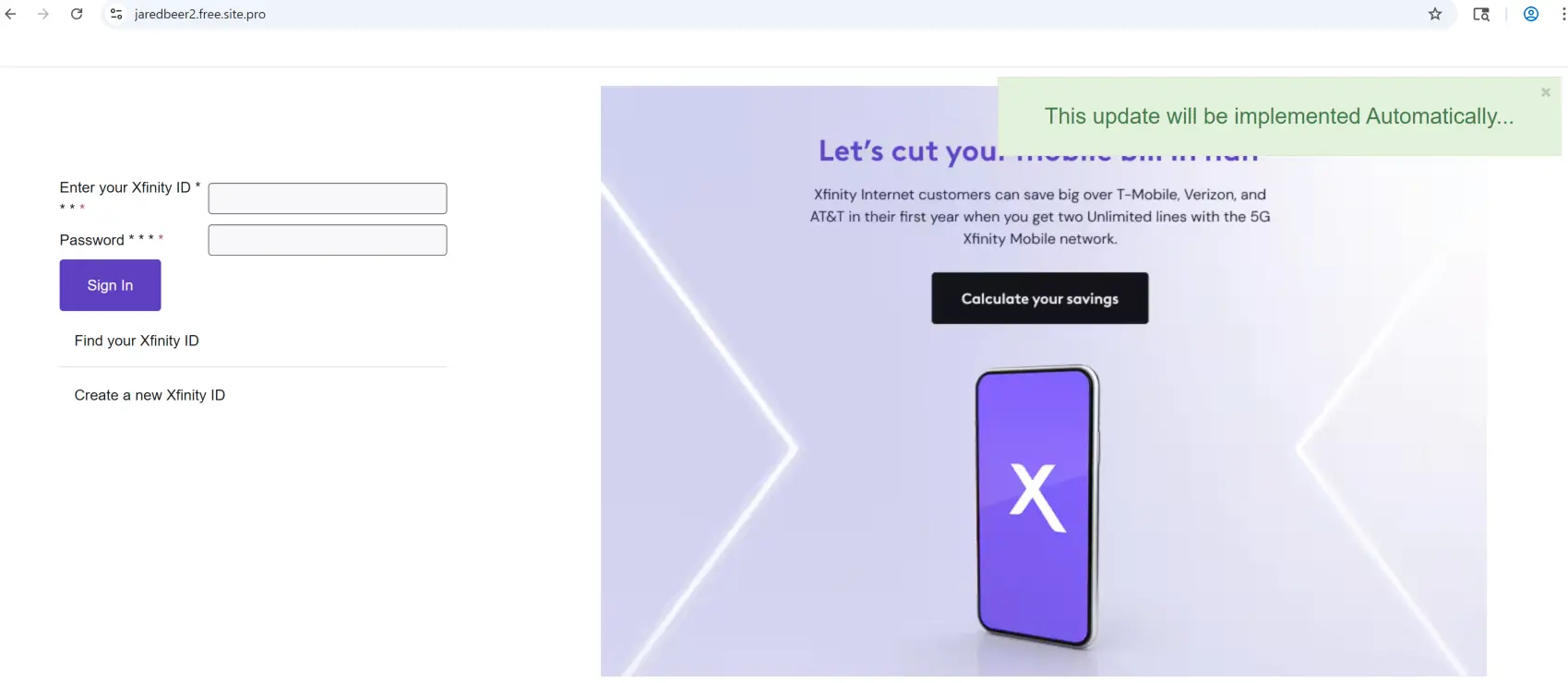
If the target clicks UPDATE N0W, they are taken to a Zoom Doc made to look like an Xfinity landing page. From here, they are presented with a CLICK TO UPDATE link. Note that there are no typos on this page, as the typos in the email body are intended for detection evasion. Because email attacks don’t end at the email, Sublime uses machine learning-powered Link Analysis to recursively analyze links in an email, which in this case showed a page with Xfinity branding and a docs.zoom[.]us URL.

If the target clicks on CLICK TO UPDATE, they are taken to a credential phishing page on an entirely new domain.
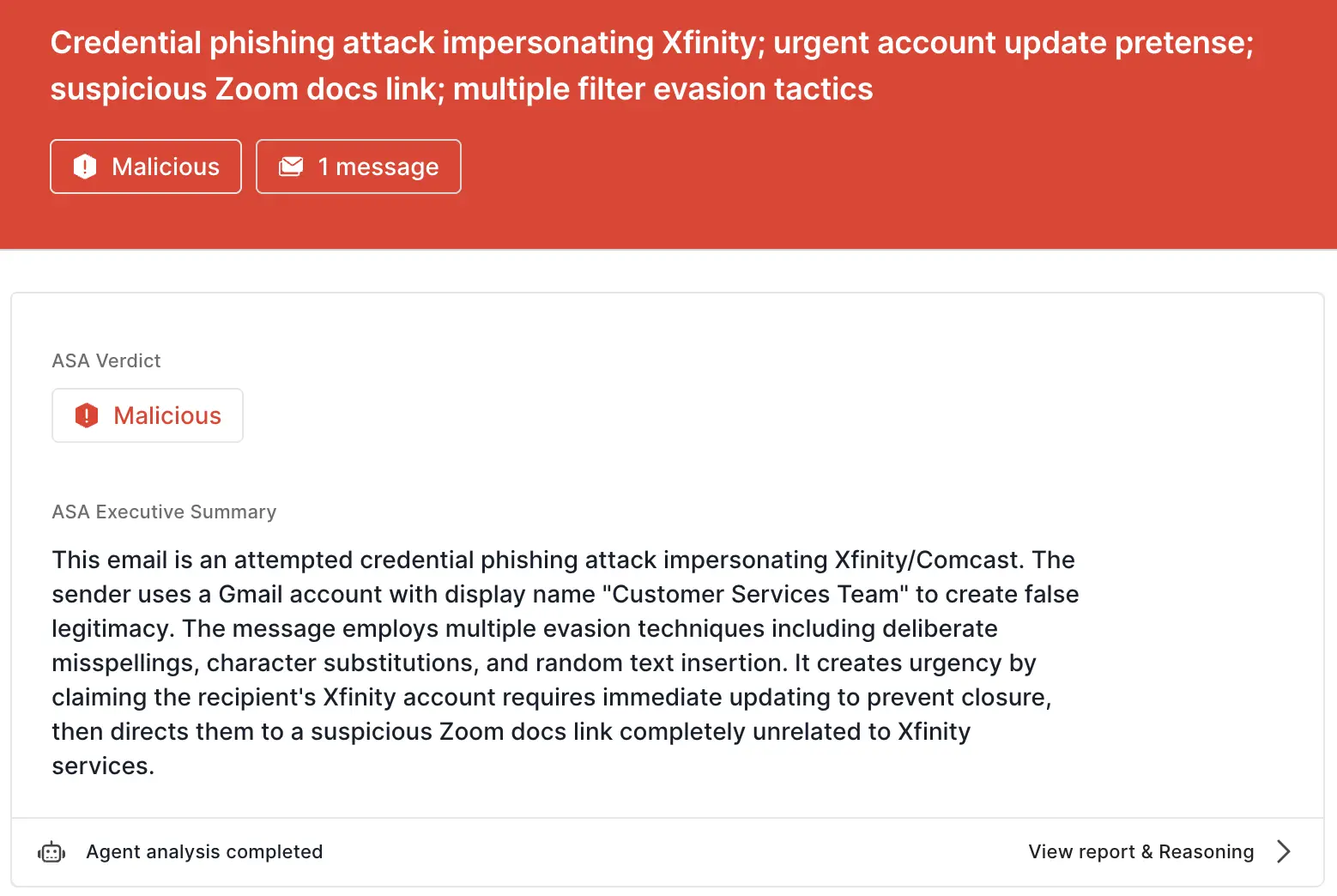
Sublime's AI-powered detection engine prevented this attack. Some of the top signals for this attack were:
docs.zoom[.]us.ASA, Sublime’s Autonomous Security Analyst, flagged this email as malicious. Here is ASA’s analysis summary:
Living off Trusted Sites (LOTS) attacks are popular because they let bad actors hide behind friendly domains. That’s why the most effective email security platforms are adaptive, using AI and machine learning to shine a spotlight on seemingly minor discrepancies.
If you enjoyed this Attack Spotlight, be sure to check our blog every week for new blogs, subscribe to our RSS feed, or sign up for our monthly newsletter. Our newsletter covers the latest blogs, detections, product updates, and more.
Read more Attack Spotlights:
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)