December 29, 2025
Looking at some interesting threat trends ahead of our 2026 email security report
We’re in that week between the Christmas and New Year’s holidays when brains and bodies are recharging after 51 weeks of chaos. If you’re less “recharging” and more “working” this week, though, we wanted to share a lighter piece to think about as we head into 2026.
To give some context, we’re currently working on our 2026 email security report (here’s our report from earlier this year) that looks back at some of the big stories being told by our platform data. It’ll be shipping on January 21st, but while we’re still in the middle of slicing, dicing, analyzing, and writing, a few cool trends popped out that we wanted to share now. So without further ado…
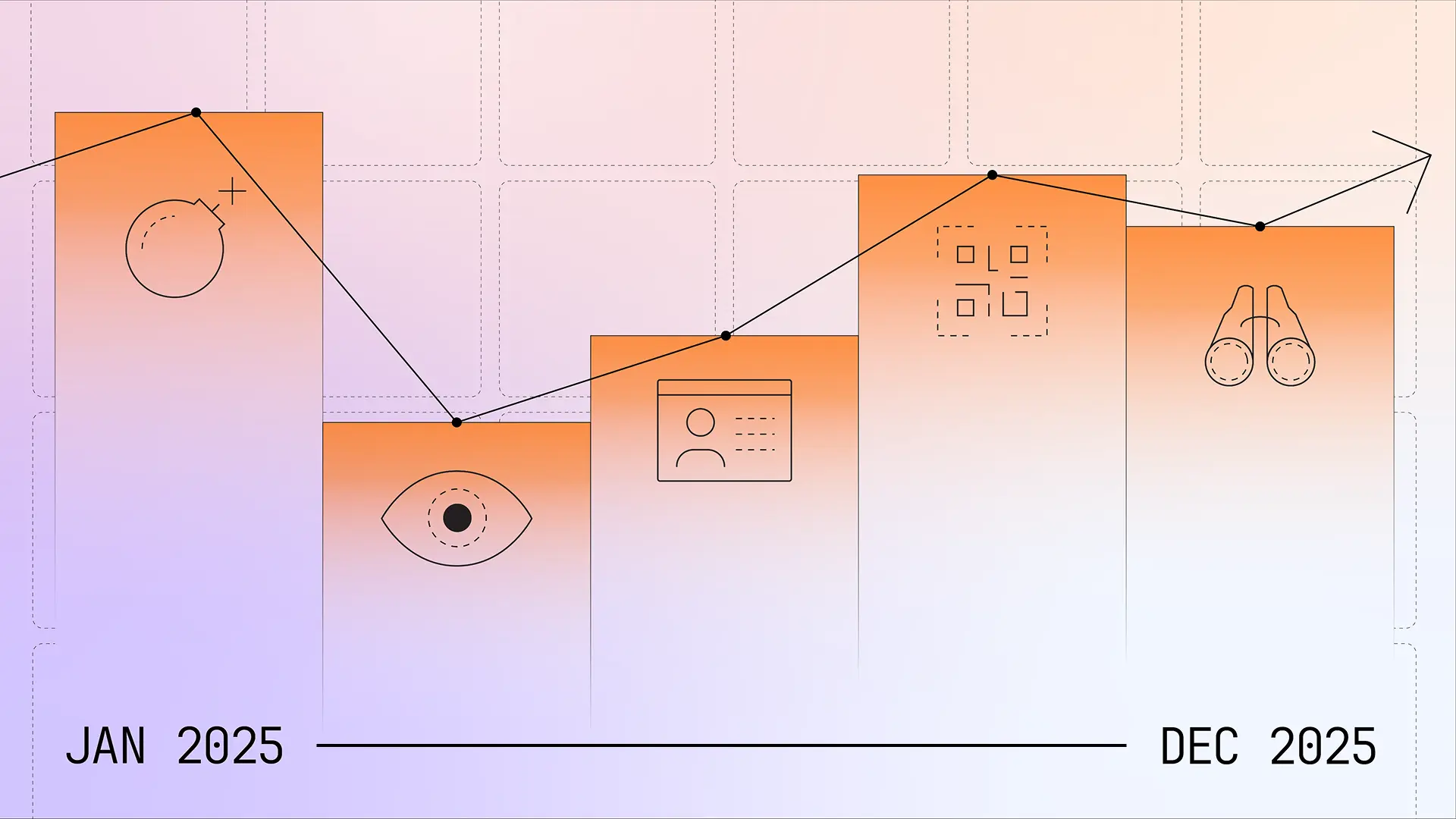
We’re still analyzing the numbers for this attack, but preliminary findings are showing a nearly 22x increase in malicious calendar-based attacks (ICS phishing) from the first to second half of 2025 for Sublime customers.
In these two-vector attacks, adversaries will put phishing information or other malicious payloads within a calendar invite that is sent to both the target’s inbox and calendar. The math gets fuzzy here, but this approach more than doubles the chance of success for an attack, because even if the email gets caught by an email security solution, the event is still automatically added to the target’s calendar thanks to default automations offered by the major cloud email providers.
Sublime stops these attacks for customers. And if you aren’t a Sublime customer, check out our open source solution that will work in your environment (no account necessary).
While malware and ransomware attacks will result in a file-based payload, their evasion tactics appear to be shifting towards behavioral evasions like social engineering and time-based delivery (ex: tax-themed attacks in April). This could be due to the generally increased complexity of attacks, the increased use of GenAI to craft attack messages, or a matter of learning from the successes of other attack types.
In our Q1 report, we highlighted QR phishing as a hot trend. Well, it didn’t get less hot. From the first to second half of 2025, we saw a nearly 300% increase in QR code-based attacks. This is unsurprising as these attacks:
The most commonly abused service providers are Microsoft, Google, and X, but we’ve seen steady growth in the use of lesser known services to deliver attacks from legitimate infrastructure (or at least infrastructure not deemed “illegitimate”).
In fact, it’s looking like nearly 25% of LOTS attacks originate from newer, smaller, or more obscure hosting sites. The bulk of these attacks appear to be coming from the abuse of page and form building platforms, support portals, collaboration services, file sharing systems, and design tools.
We started offering email bomb protection back in August, and wow, some of them are big. If you aren’t familiar with email bombs, we’ve been frequently calling them the DDoS of the inbox. In these attacks, adversaries send a lot of email to an inbox (or inboxes) to shut them down, obscure an attack, and more.
For example, an attacker could spam a mailbox with hundreds of messages (typically graymail, like newsletters) and then send a message impersonating IT to help the target get their mailbox back under control. If the target calls “IT” they’ll only be a few clicks away from a machine takeover.
We are seeing some very interesting numbers on email bombs (which we’ll put in the full report), but we’re going to share the biggest one here. The largest email bomb we detected was made up of over 10,000 messages. That’s big.
Those are just a few preliminary findings from our ongoing analysis. It’s always interesting to see what insights are hiding in attack data, so if you want to see the full report, download it from our Resource Center on Jan. 21 and attend our webinar that same day to watch me and our head of Product Marketing break down the numbers.
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)