April 12, 2023

This post will cover a brief timeline of QakBot’s evolution, and focus primarily on recently observed attack techniques. We’ll discuss detection methodologies and share MQL rules that anyone can use to detect, prevent, and hunt for these threats in email environments today. If you're already running Sublime, you received these new protections automatically.
QakBot, also known as QBot and Pinkslipbot, has been active since 2007 and has been consistently and constantly evolving. Initially, QakBot started as a banking Trojan that utilized command and control (C2) servers for payload delivery. With modularity being a crucial component, QakBot’s primary objective was to steal financial data and login credentials from victims. It was also capable of spying on financial operations and redirecting users to fake banking sites.
Over the years, QakBot has used many different techniques to infect users, including malspam campaigns with malicious attachments, hyperlinks, or embedded images to drop a second-stage payload. The malware itself has evolved to include a variety of functions and new obfuscation methods to avoid detection.
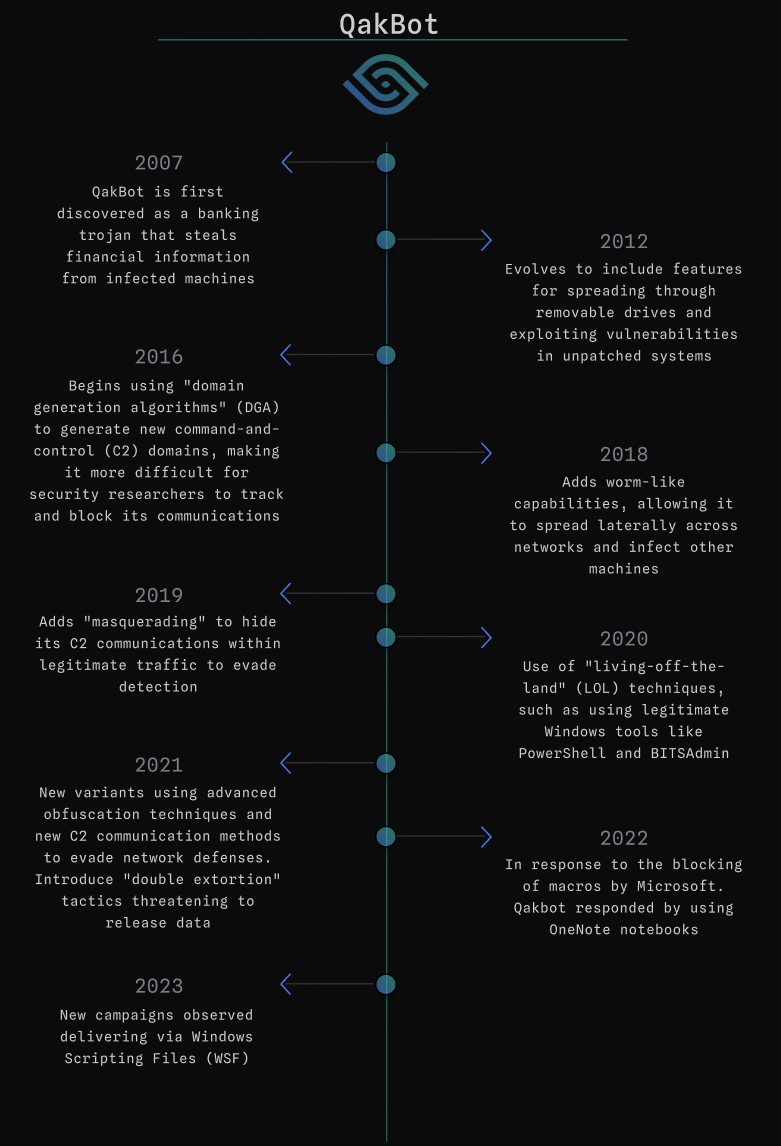
In early 2023, QakBot was observed using a new method of distribution through Windows Script Files (.wsf). In this scenario, the phishing email contains a zip file with a random name, which includes a wsf file and txt file, and a decoy pdf file.
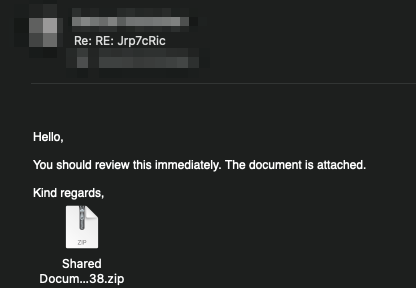
The malicious attachment is delivered in the following sequence:
This delivery method is unique in that it uses a .wsf file to execute the malicious code, rather than relying on macros or other scripting languages.
When the victim tries to open the .wsf file, javscript is executed to download the QakBot DLL file. The file is usually loaded into the C:\ProgramData directory and executed using “Rundll32.exe” with “Wind” as a parameter. For example:
Let’s create an MQL rule that can detect this specific delivery method by looking for the following characteristics:
Attachment: Archive with pdf, txt and wsf files

The rule is inspecting inbound mail with at least 1 attachment. It uses Sublime’s open-source static-files, specifically the $file_extensions_common_archive list, to determine if the file is an archive.
If an attachment is found with an archive , we use file_extension to check for archives and the file.explode function, which explodes the archive file. The rule then checks if the archive file contains a .pdf, .txt, and .wsf file at a depth of 1.
If all of these conditions are met, the rule tags the email as "Qakbot" and "Suspicious attachment" and assigns it a medium severity rating.
Test in the Sublime Playground
In addition to specific detections, it’s important to consider the protections gained by a more generalized approach. Attack surface reduction (ASR) is a proactive security strategy that involves minimizing potential avenues of attack for malicious actors by limiting their opportunity to do harm.
One effective way to protect against Qakbot and other similar malware threats is by implementing attack surface reduction (ASR) techniques, such as the rule below. This rule utilizes MQL to scan email content for any links that may lead to an encrypted zip file, and then checks whether the zip file contains a disk image in IMG, ISO, or VHD format.
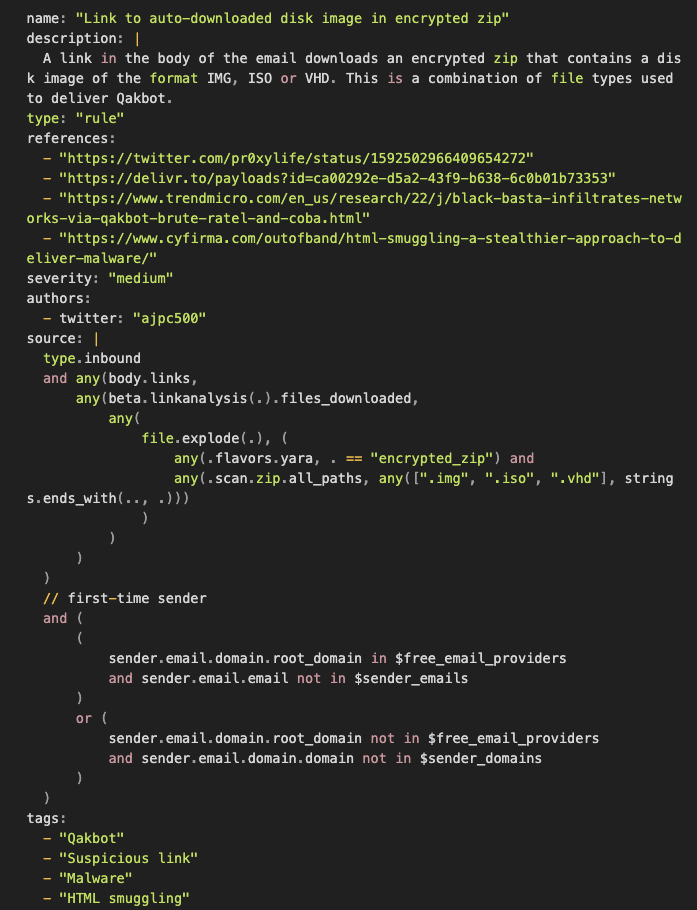
In late 2022, QakBot began using OneNote attachments as part of its campaigns, likely in response to Microsoft’s blocking of Office Macros. We can again leverage MQL to surface these attempts.
The rule below was contributed by @Kyle_Parrish_/Kyle Parrish, a Sublime Community user.

This rule aims to identify potential threats in OneNote attachments by searching for specific suspicious commands. It first checks for OneNote files, as well as OneNote files inside archives, using Sublime’s static-files list ($file_extensions_common_archives). The rule then uses MQL to scan for specific strings that may indicate malicious behavior, such as references to shell commands (e.g., Windows Script Host, scheduled tasks), PowerShell, and other malware indicators. This is another great example of reducing your attack surface, while not specifically aimed at Qakbot, but any malware looking to leverage similar delivery mechanisms.
Qakbot's unique delivery methods require a multi-layered approach for detection.
One effective technique for safeguarding against Qakbot and other similar malware threats is implementing Attack Surface Reduction (ASR) measures. By proactively reducing potential avenues of attack for malicious actors, ASR can significantly minimize the opportunity for harm.
All of the rules described above can be used as both detection rules to prevent new attacks going forward, as well as a Hunt rules to look for historical attacks. They've all been added to the core Sublime Rules Feed, which means all Sublime instances, both free and paid, receive these new protections by default.
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)