October 16, 2025
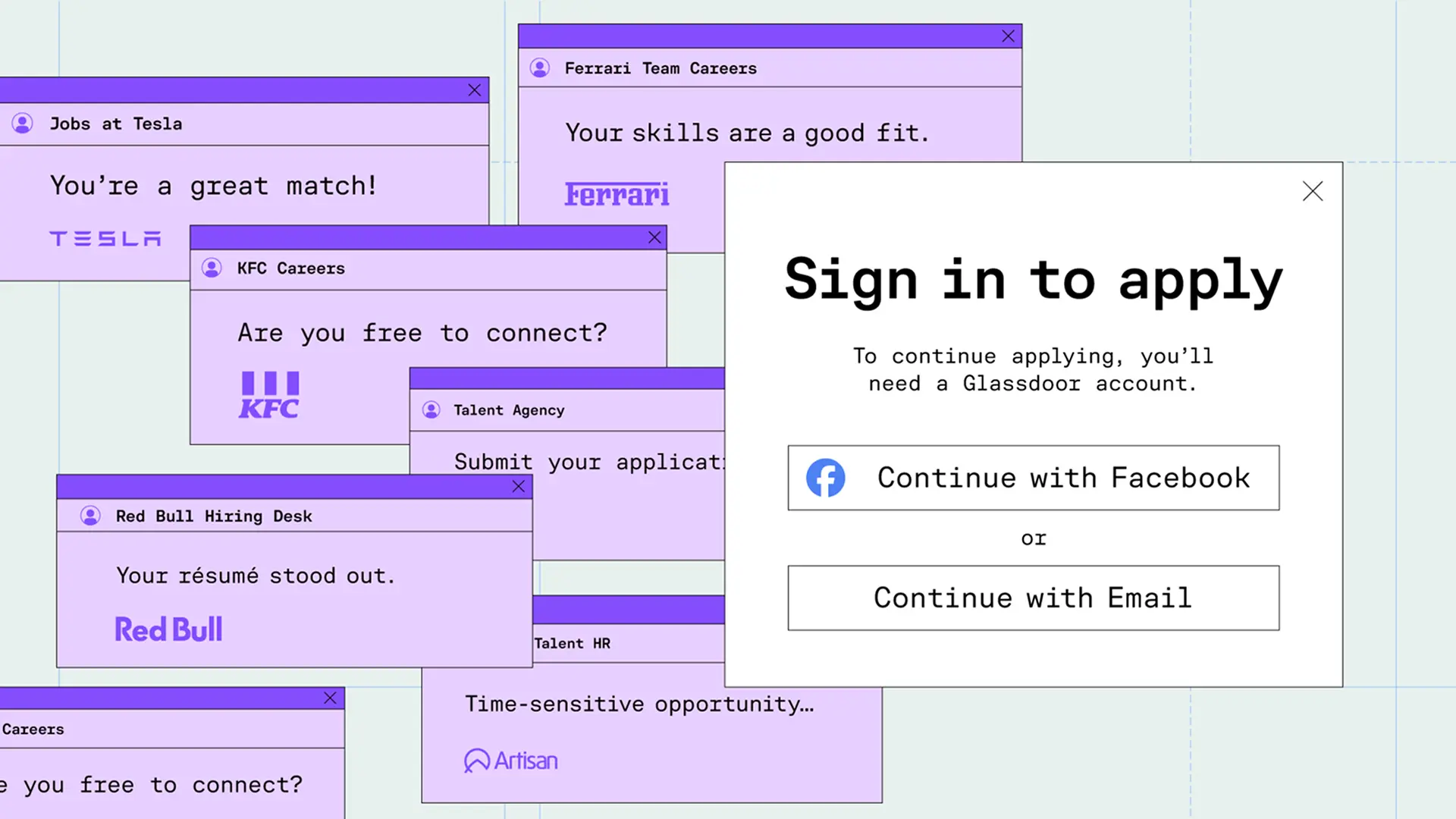
Fake hiring messages impersonating brands like Tesla, KFC, Red Bull, and more
Sublime’s Attack Spotlight series is designed to keep you informed of the email threat landscape by showing you real, in-the-wild attack samples, describing adversary tactics and techniques, and explaining how they’re detected. These attacks can be prevented with a free Sublime account.
EMAIL PROVIDER: Google Workspace, Microsoft 365
ATTACK TYPE: Credential phishing
Scammers increase their chances of success by keeping their scams relevant. As the U.S. faces a slowed job market, a fake job opportunity from a reputable company is very relevant bait. Earlier this week, we looked at a Google Careers phishing scam. In this post, we'll be looking at another recent attack campaign in which we saw bad actors impersonate a wide variety of well-known companies in order to credential phish targets looking for social media manager jobs. While the brands varied per message, the intent and methodology remained the same, indicating the use of a phishing kit and/or LLM to quickly create and launch a varied attack. All messages contained:
Here are just a few examples:
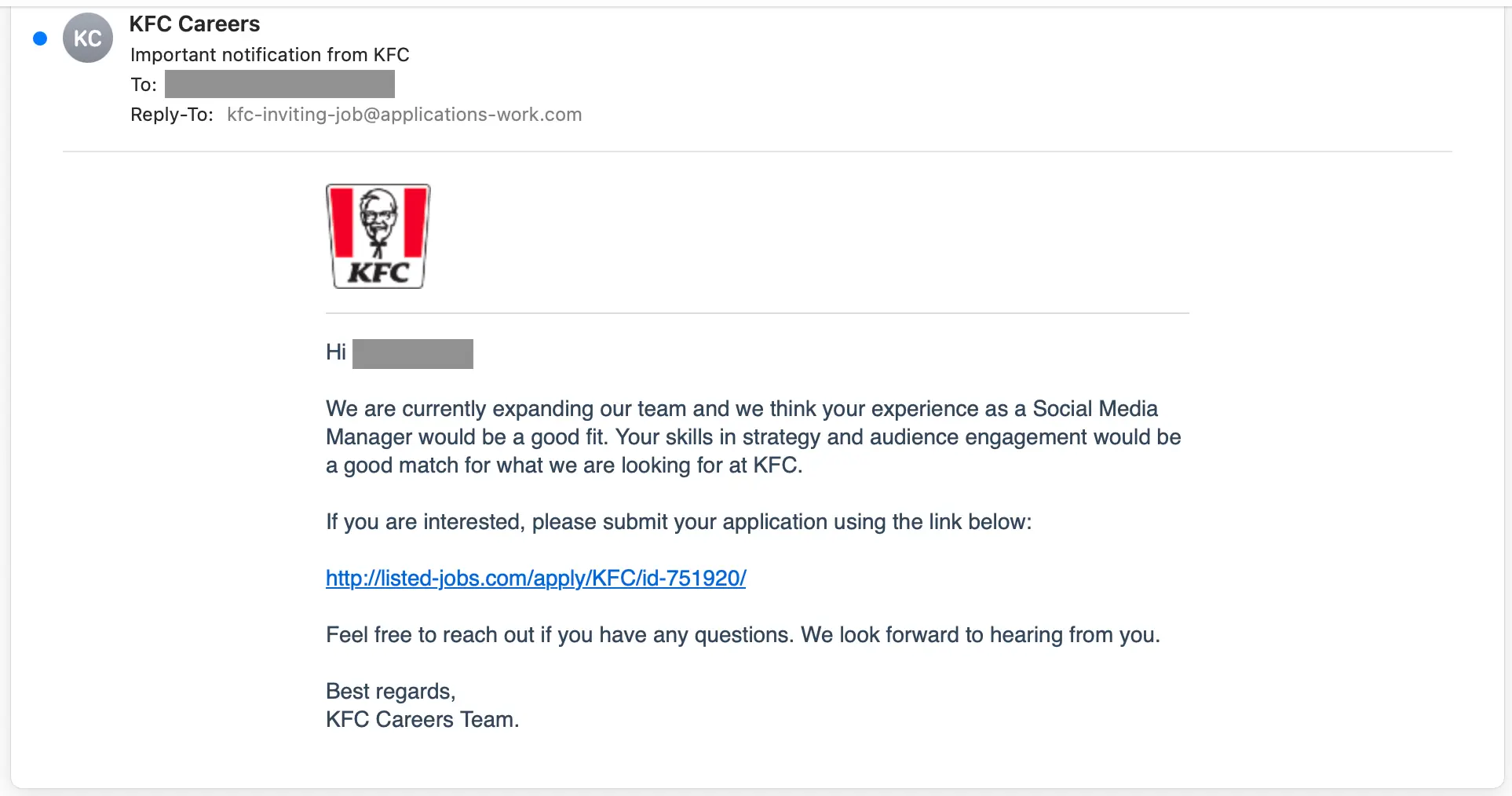
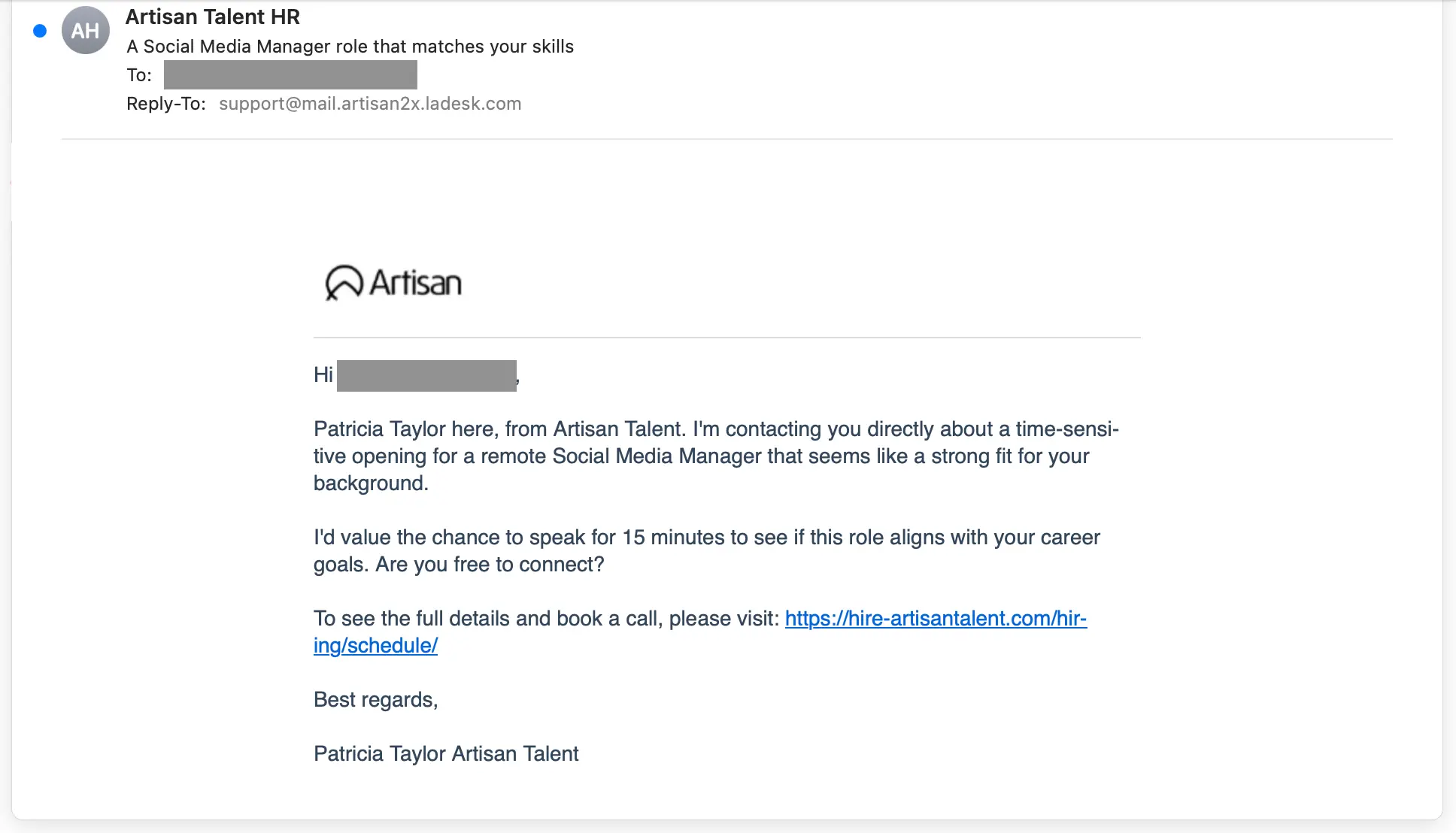
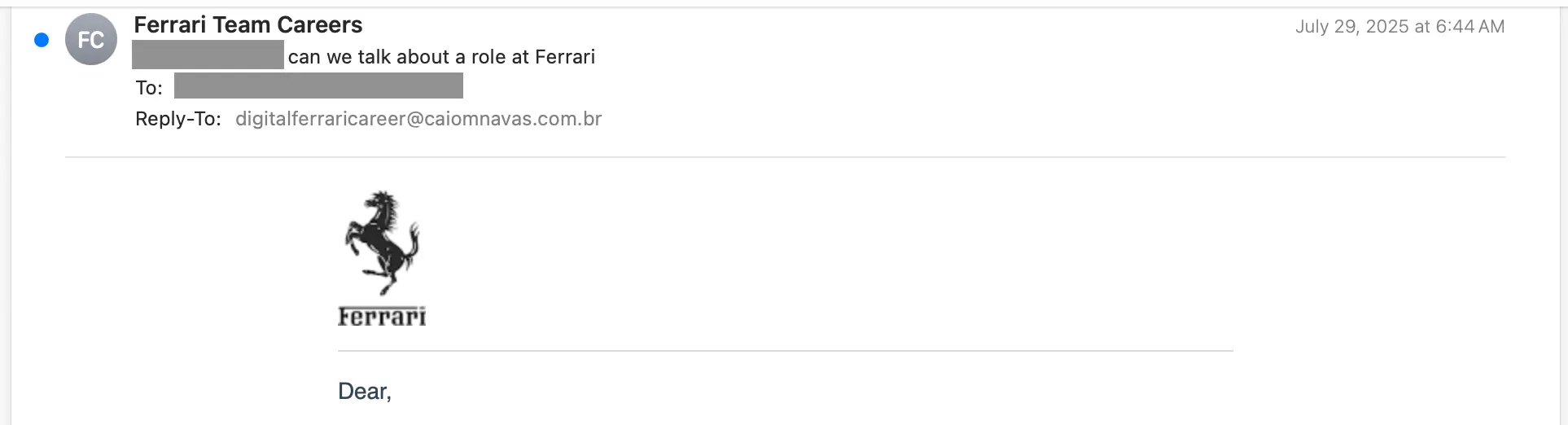

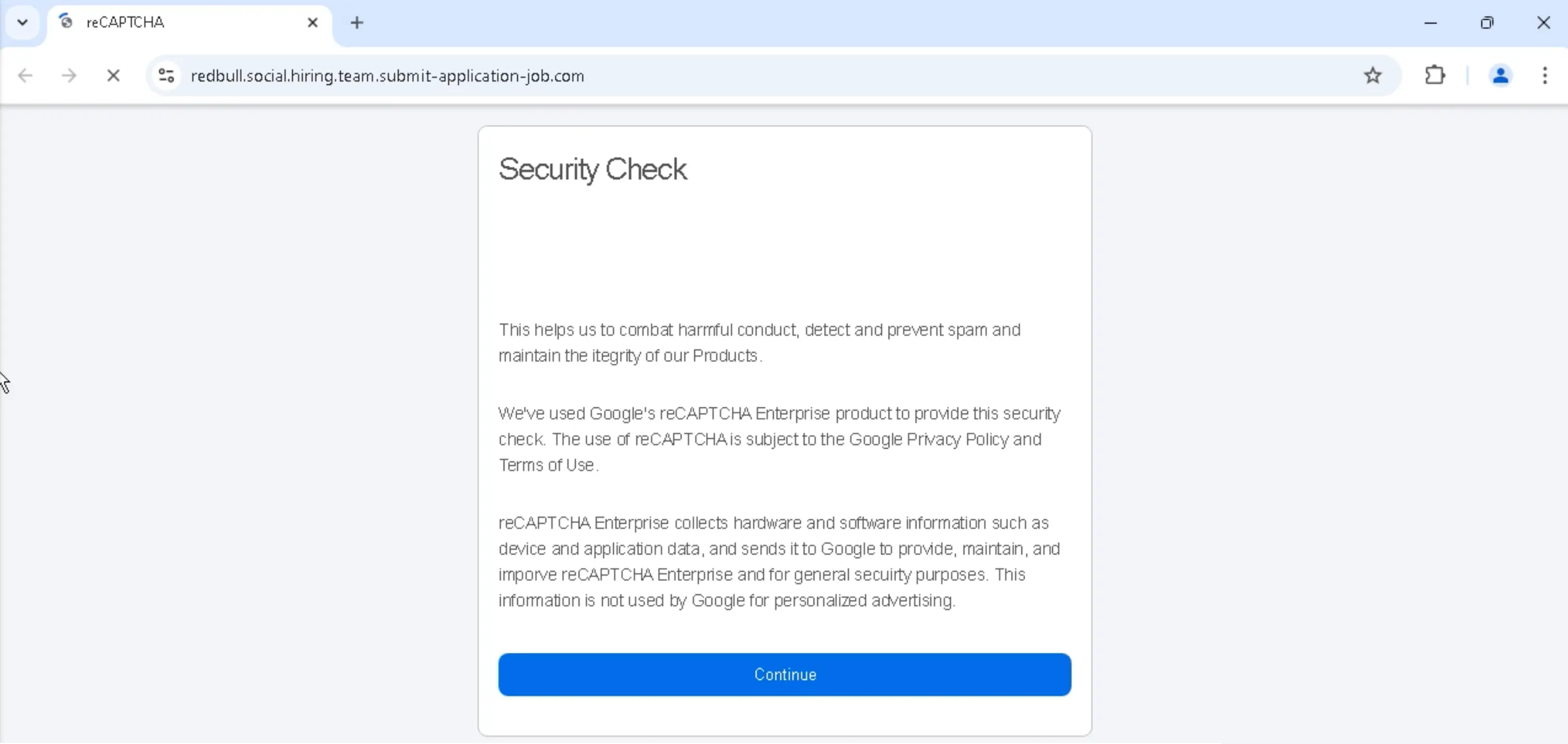
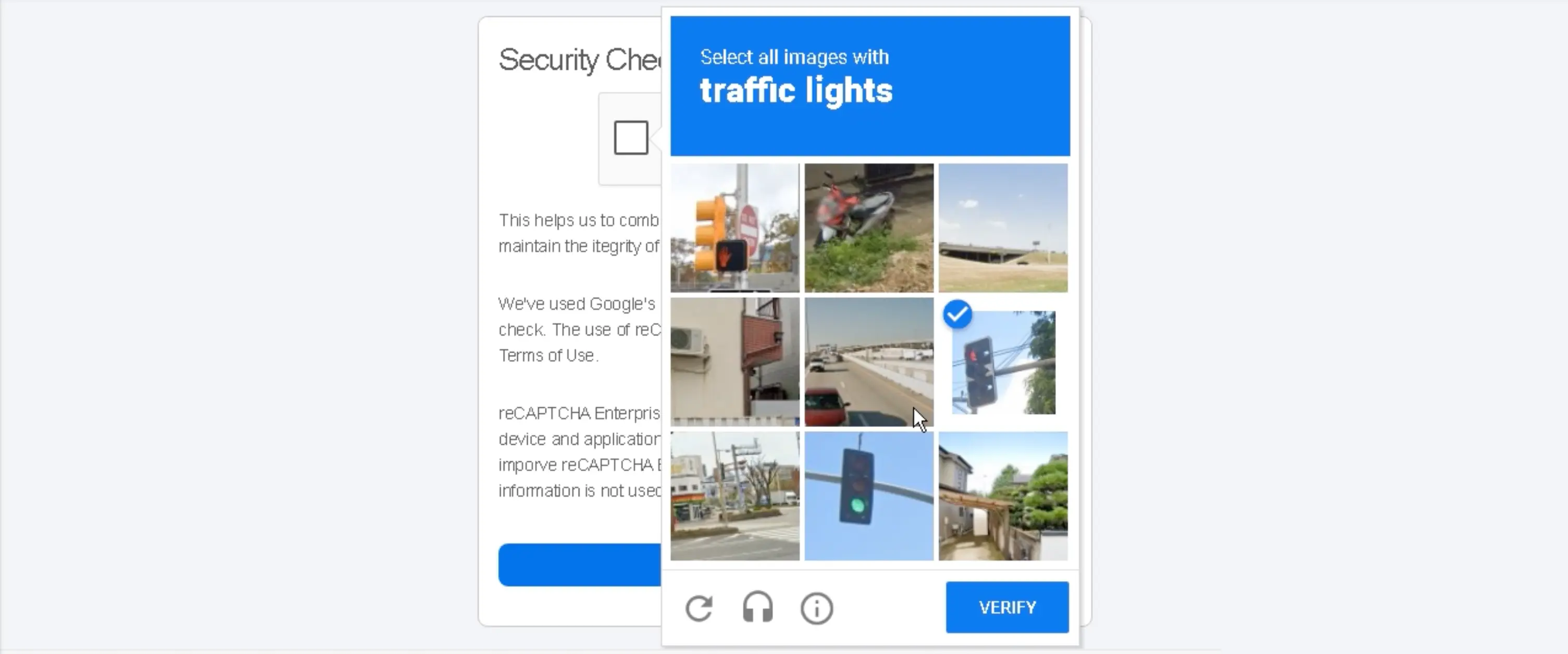
Using the Red Bull message as an example, clicking the www.redbull@rebrand[.]ly link takes the target to a fake security check. The check includes a reCAPTCHA challenge image.
Once the challenge is completed, the target is taken to a fake Glassdoor job listing.
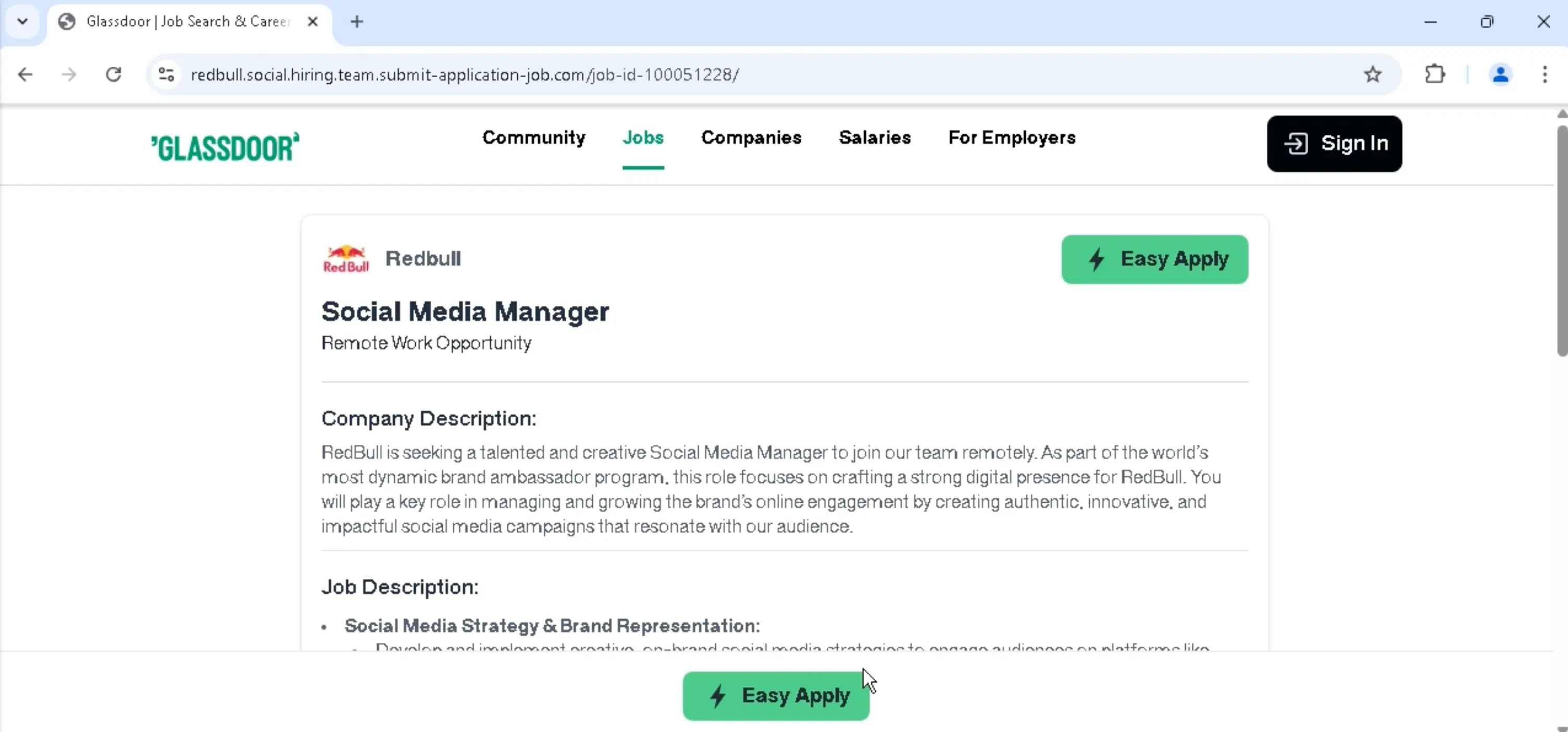
After clicking Easy Apply, the target is taken to a fake Glassdoor login where they can login with their email address or Facebook account.
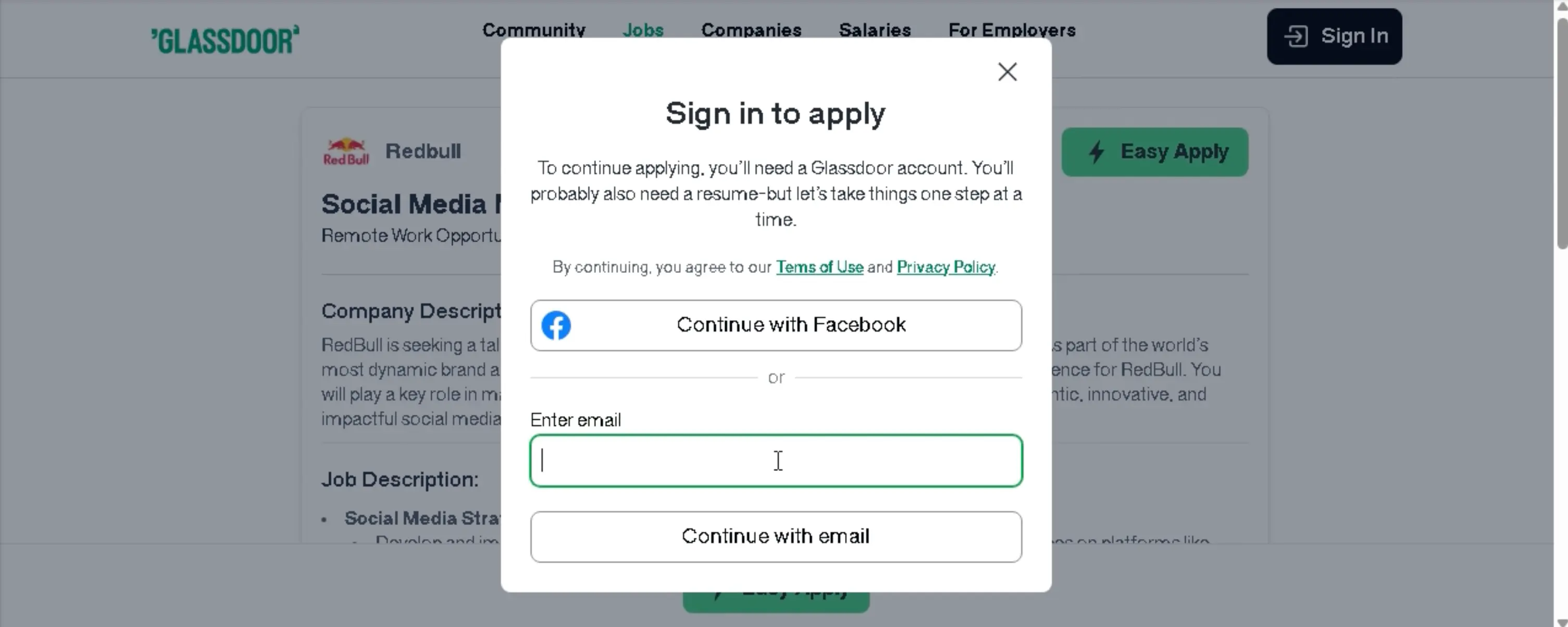
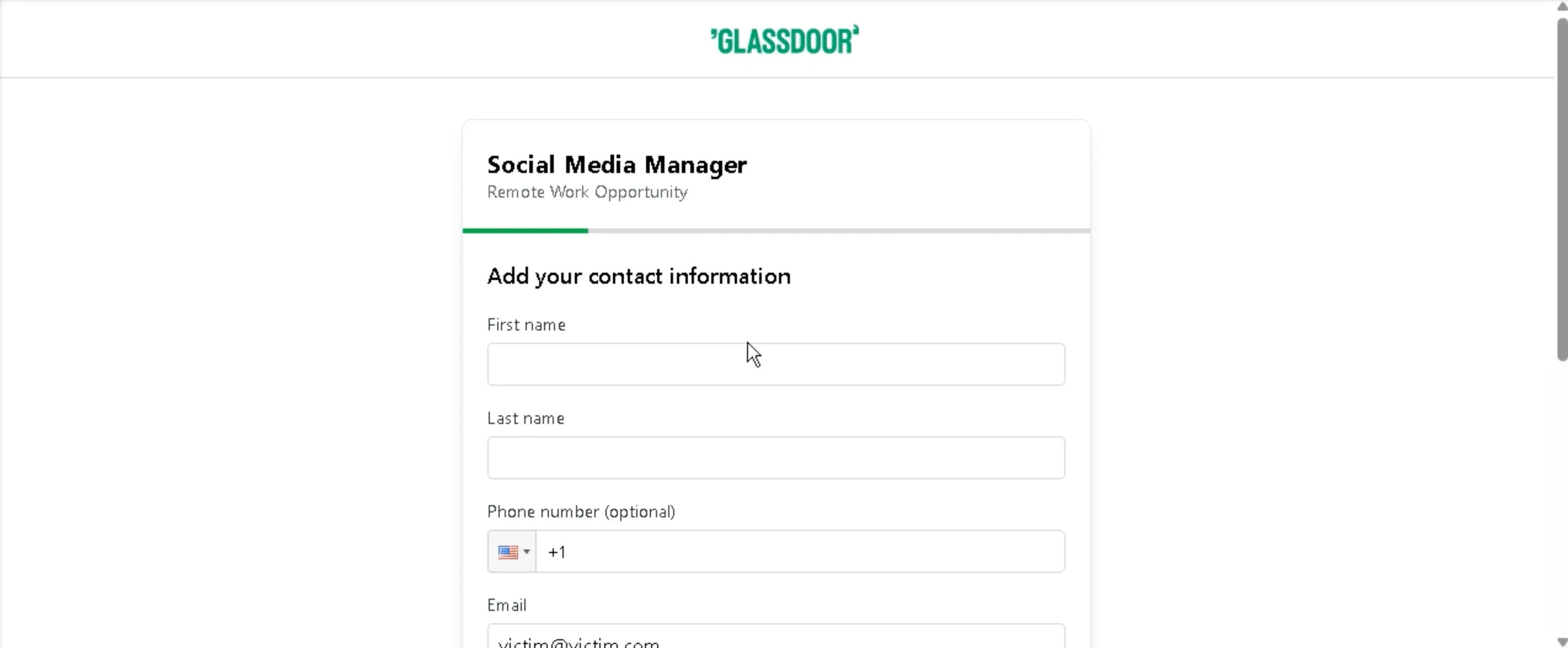
If the victim attempts to login via email, they are taken to a contact form. After filling in the form, the target is taken back to the login window – not logged in.
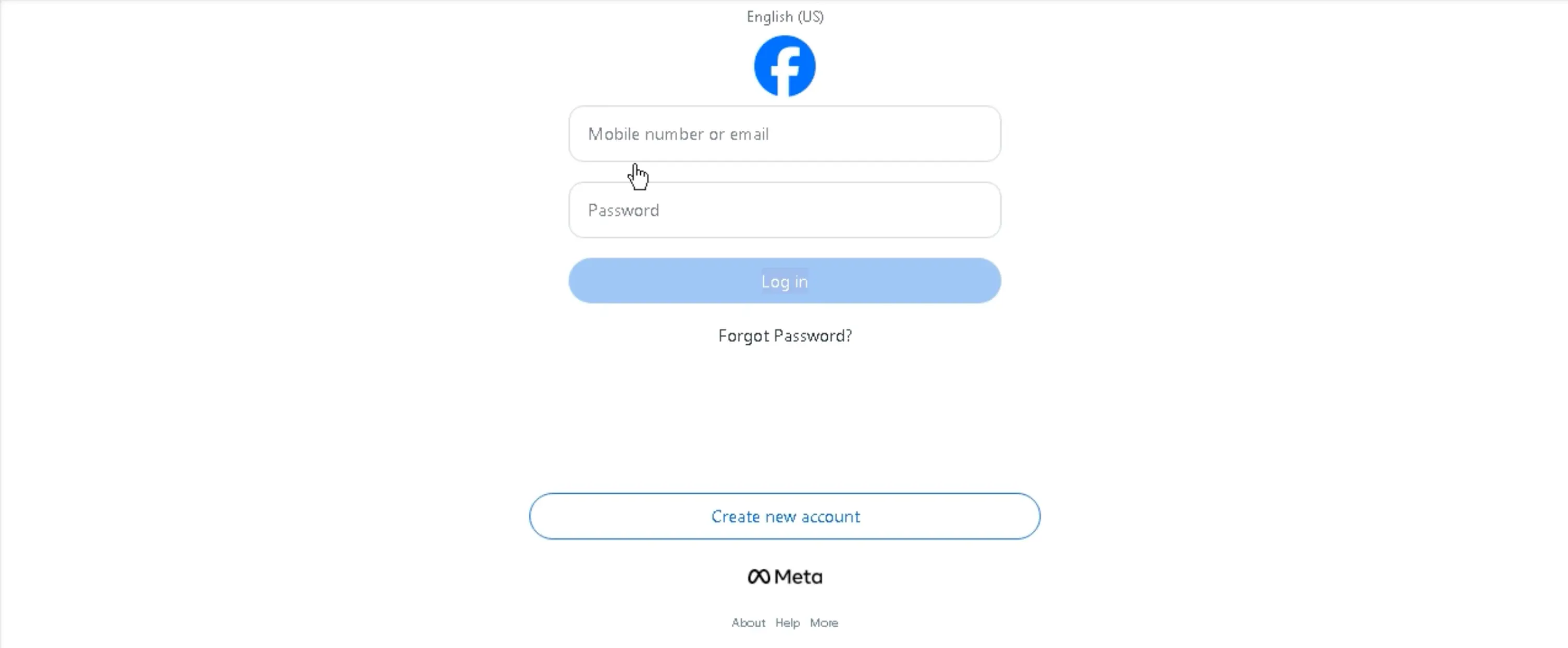
After the email login fails, the victim will be presented with a fake Facebook login.
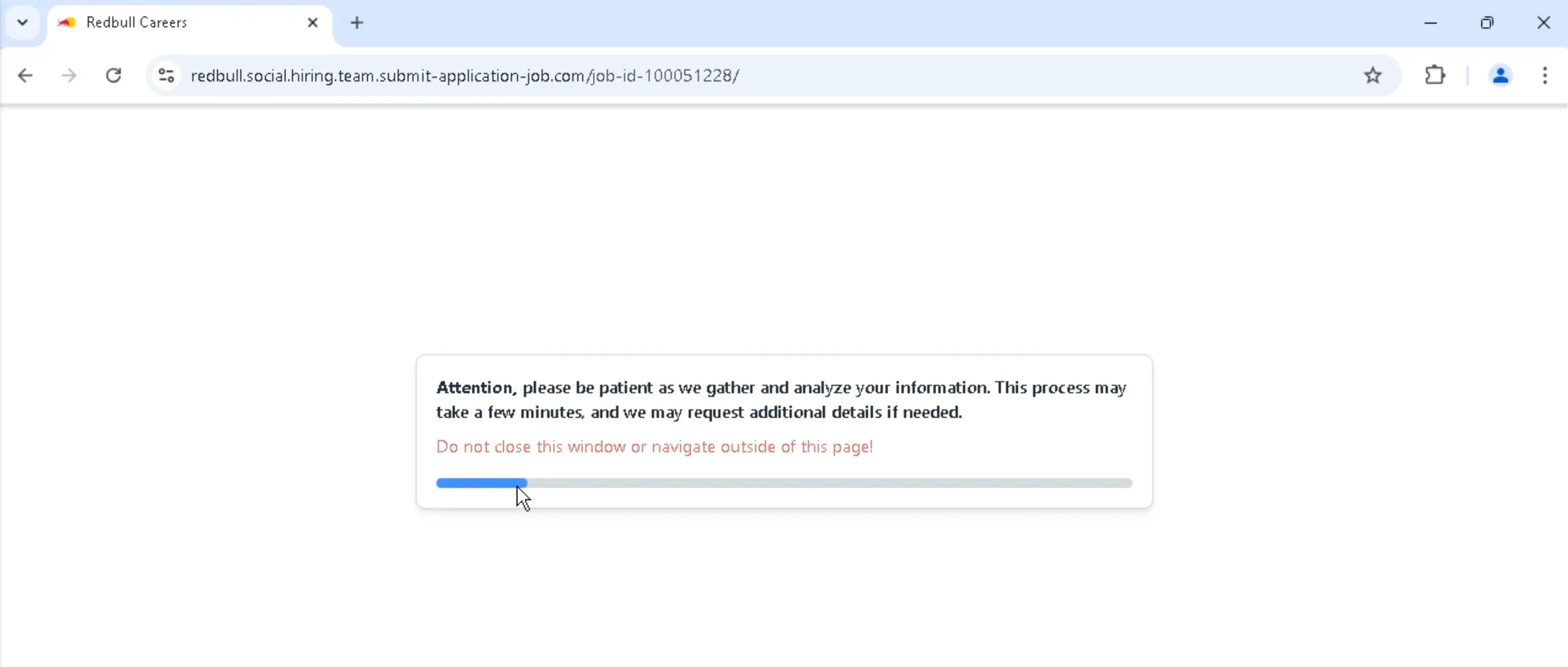
When the victim enters their Facebook credentials and click Log in, they are taken to a fake progress indicator that indicates an analysis is being performed. No analysis is being performed and the progress indicator will never reach 100%.
Sublime's AI-powered detection engine prevented this attack. Some of the top signals for this attack were:
www.redbull@rebrand[.]ly, which make it appear as if the link leads to redbull[.]com when it actually directs to rebrand[.]ly.alexa.redbull-talent-recruiting.redbull[.]com), the sender is messaging-service@post.xero[.]com, and the reply-to is alexa.redbull-talent-recruiting@trustedbds.com.ASA, Sublime’s Autonomous Security Analyst, flagged this email as malicious. Here is ASA’s analysis summary:
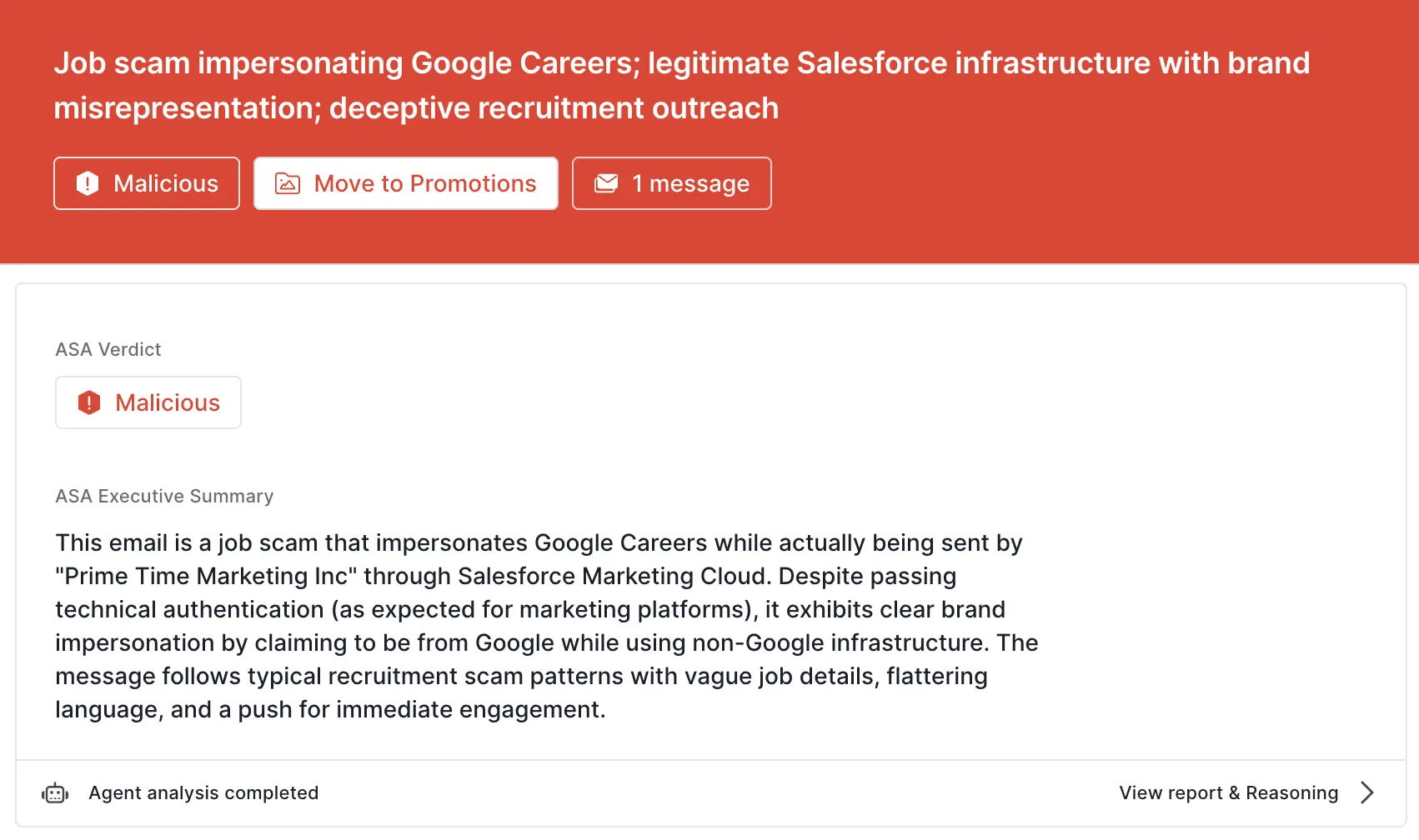
Scams are effective because they offer opportunities too enticing to pass up. That’s why the most effective email security platforms are adaptive, using AI and machine learning to shine a spotlight on the suspicious indicators of the scam.
If you enjoyed this Attack Spotlight, be sure to check our blog every week for new blogs, subscribe to our RSS feed, or sign up for our monthly newsletter. Our newsletter covers the latest blogs, detections, product updates, and more.
Read more Attack Spotlights:
Sublime releases, detections, blogs, events, and more directly to your inbox.
See how Sublime delivers autonomous protection by default, with control on demand.
.svg)