- Content analysis
Attack Types
BEC/Fraud
Callback Phishing
Credential Phishing
Extortion
Malware/Ransomware
Reconnaissance
Spam
Tactics and Techniques
Encryption
Evasion
Exploit
Free email provider
Free file host
Free subdomain host
HTML smuggling
Image as content
Impersonation: Brand
Impersonation: Employee
Impersonation: VIP
IPFS
ISO
LNK
Lookalike domain
Macros
OneNote
Open redirect
Out of band pivot
PDF
Punycode
QR code
Scripting
Social engineering
Spoofing
Detection Methods
Archive analysis
Content analysis
Computer Vision
Exif analysis
File analysis
Header analysis
HTML analysis
Javascript analysis
Macro analysis
Natural Language Understanding
Optical Character Recognition
OLE analysis
PDF analysis
QR code analysis
Sender analysis
Threat intelligence
URL analysis
URL screenshot
Whois
XML analysis
YARA
Detection Method: Content analysis
Content analysis looks at the language and structure of a message to identify signs of phishing, social engineering, and other malicious intent. Instead of scanning for keywords, this method uses natural language understanding (NLU) to detect meaning, intent, and tone across the message.
Content analysis helps detect:
- BEC attempts with urgent messages from executive impersonators
- Credential phishing disguised as login or document notifications
- Callback scams posing as account renewals or fake support
- Extortion threats or blackmail messages
- Financial or personal data requests in suspicious contexts
- Fake job offers targeting employees
- Invoice fraud, payroll fraud, and more
For example, a phishing email may impersonate a CFO asking for a wire transfer. Content analysis can flag the urgent tone, financial context, and impersonation attempt.
Blog Posts
Hiding a $50,000 BEC financial fraud in a fake email thread · Blog · Sublime Security
Callback phishing via invoice abuse and distribution list relays · Blog · Sublime Security

Hidden credential phishing within EML attachments · Blog · Sublime Security

Living Off the Land: Credential Phishing via Docusign abuse · Blog · Sublime Security
Living Off the Land: Callback Phishing via Docusign comment · Blog · Sublime Security

Adversarial ML: Extortion via LLM Manipulation Tactics · Blog · Sublime Security
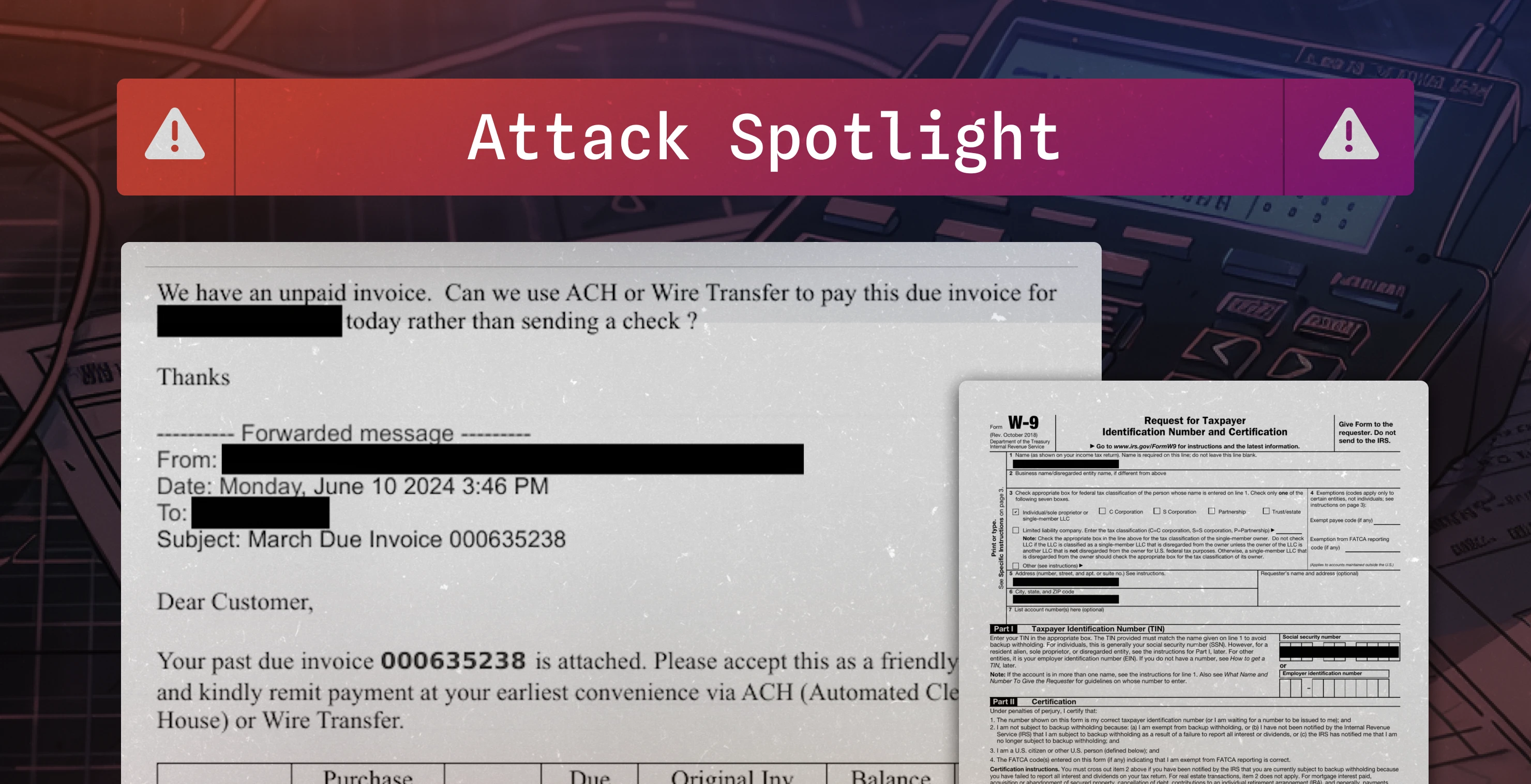
Fake invoice used to conduct $16,800 BEC attempt · Blog · Sublime Security

QR Code Phishing: Decoding Hidden Threats · Blog · Sublime Security

Call Me Maybe? The Rise of Callback Phishing Emails · Blog · Sublime Security

Detecting QakBot: WSF attachments, OneNote files, and generic attack surface reduction · Blog · Sublime Security
Attack Types (7):
Tactics & Techniques (26):
Evasion
Impersonation: Brand
Social engineering
Free file host
Free email provider
PDF
Impersonation: VIP
Free subdomain host
Open redirect
Encryption
Scripting
Spoofing
Image as content
Lookalike domain
Impersonation: Employee
Out of band pivot
Exploit
Macros
Credential Phishing
HTML smuggling
HTML injection
QR code
LNK
OneNote
IPFS
ISO
Rule Name & Severity | Last Updated | Author | Types, Tactics & Capabilities | |
|---|---|---|---|---|
Service abuse: HungerRush domain with SendGrid tracking targeting ProtonMail | 14h ago Mar 4th, 2026 | Sublime Security | /feeds/core/detection-rules/service-abuse-hungerrush-domain-with-sendgrid-tracking-targeting-protonmail-73f62e74 | |
Brand Impersonation: Disney | 16h ago Mar 4th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-disney-bf90b8fb | |
Service abuse: DocSend share from an unsolicited reply-to address | 17h ago Mar 4th, 2026 | Sublime Security | /feeds/core/detection-rules/service-abuse-docsend-share-from-an-unsolicited-reply-to-address-b377e64c | |
Link: Apple App Store link to apps impersonating AI adveristing | 19h ago Mar 4th, 2026 | Sublime Security | /feeds/core/detection-rules/link-apple-app-store-link-to-apps-impersonating-ai-adveristing-19b556e6 | |
BEC with unusual reply-to or return-path mismatch | 2d ago Mar 3rd, 2026 | Sublime Security | /feeds/core/detection-rules/bec-with-unusual-reply-to-or-return-path-mismatch-83e5e2df | |
Fake warning banner using confusable characters | 3d ago Mar 2nd, 2026 | Sublime Security | /feeds/core/detection-rules/fake-warning-banner-using-confusable-characters-179ee1ff | |
Attachment: PDF with a suspicious string and single URL | 3d ago Mar 2nd, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-pdf-with-a-suspicious-string-and-single-url-3bdbb7ad | |
Attachment: Finance themed PDF with observed phishing template | 3d ago Mar 2nd, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-finance-themed-pdf-with-observed-phishing-template-c936f7cc | |
VIP impersonation with w2 request with reply-to mismatch | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/vip-impersonation-with-w2-request-with-reply-to-mismatch-e7e73fad | |
Link: Multistage landing - ClickUp abuse | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/link-multistage-landing-clickup-abuse-78a5d035 | |
Attachment: PDF with suspicious link and action-oriented language | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-pdf-with-suspicious-link-and-action-oriented-language-816d33a0 | |
Brand impersonation: Zoom via HTML styling | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-zoom-via-html-styling-b717920d | |
Attachment: Encrypted PDF with credential theft body | 7d ago Feb 26th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-encrypted-pdf-with-credential-theft-body-c9596c9a | |
Reconnaissance: Empty message from uncommon sender | 8d ago Feb 25th, 2026 | Sublime Security | /feeds/core/detection-rules/reconnaissance-empty-message-from-uncommon-sender-b347cdbc | |
Credential theft with 'safe content' deception and social engineering topics | 8d ago Feb 25th, 2026 | Sublime Security | /feeds/core/detection-rules/credential-theft-with-safe-content-deception-and-social-engineering-topics-22ceee0d | |
Link: JavaScript obfuscation with Telegram bot integration | 8d ago Feb 25th, 2026 | Sublime Security | /feeds/core/detection-rules/link-javascript-obfuscation-with-telegram-bot-integration-032a4485 | |
Spam: Sendersrv.com with financial communications and unsubscribe language | 9d ago Feb 24th, 2026 | Sublime Security | /feeds/core/detection-rules/spam-sendersrvcom-with-financial-communications-and-unsubscribe-language-69570820 | |
Tax Form: W-8BEN solicitation | 10d ago Feb 23rd, 2026 | Sublime Security | /feeds/core/detection-rules/tax-form-w-8ben-solicitation-a64edb69 | |
Reconnaissance: Email address harvesting attempt | 10d ago Feb 23rd, 2026 | Sublime Security | /feeds/core/detection-rules/reconnaissance-email-address-harvesting-attempt-bb31efbc | |
Link: Suspicious URL with recipient targeting and special characters | 12d ago Feb 21st, 2026 | Sublime Security | /feeds/core/detection-rules/link-suspicious-url-with-recipient-targeting-and-special-characters-e808be3a |
Page 1 of 24