- URL analysis
Attack Types
BEC/Fraud
Callback Phishing
Credential Phishing
Extortion
Malware/Ransomware
Reconnaissance
Spam
Tactics and Techniques
Encryption
Evasion
Exploit
Free email provider
Free file host
Free subdomain host
HTML smuggling
Image as content
Impersonation: Brand
Impersonation: Employee
Impersonation: VIP
IPFS
ISO
LNK
Lookalike domain
Macros
OneNote
Open redirect
Out of band pivot
PDF
Punycode
QR code
Scripting
Social engineering
Spoofing
Detection Methods
Archive analysis
Content analysis
Computer Vision
Exif analysis
File analysis
Header analysis
HTML analysis
Javascript analysis
Macro analysis
Natural Language Understanding
Optical Character Recognition
OLE analysis
PDF analysis
QR code analysis
Sender analysis
Threat intelligence
URL analysis
URL screenshot
Whois
XML analysis
YARA
Detection Method: URL analysis
URL analysis scans links in emails, attachments, or embedded content to find malicious destinations aimed at stealing your credentials, delivering malware, or launching other types of attacks. This method looks at key factors like the structure of the URL, redirection paths, domain reputation, and what the link shows when clicked.
URL analysis can help you detect:
- Phishing sites pretending to be trusted login pages
- Malicious domains hidden through URL shorteners or redirects
- Login forms on suspicious or newly registered domains
- Brand impersonation using slight domain tweaks (typosquatting or homograph attacks)
- Suspicious URLs with weird characters or unusual patterns
For example, attackers often use redirect chains to hide their final destination from security scanners. With URL analysis, we can follow these redirects to reveal the true destination and assess the potential threat.
Blog Posts
Tax season email attacks: AdWind RATs and Tycoon 2FA phishing kits · Blog · Sublime Security
Hiding a $50,000 BEC financial fraud in a fake email thread · Blog · Sublime Security

Talking phish over turkey · Blog · Sublime Security

Living Off the Land: Credential Phishing via Docusign abuse · Blog · Sublime Security
Living Off the Land: Callback Phishing via Docusign comment · Blog · Sublime Security

Abusing Discord to deliver Agent Tesla malware · Blog · Sublime Security

Gotta Catch 'Em All: Detecting PikaBot Delivery Techniques · Blog · Sublime Security

QR Code Phishing: Decoding Hidden Threats · Blog · Sublime Security
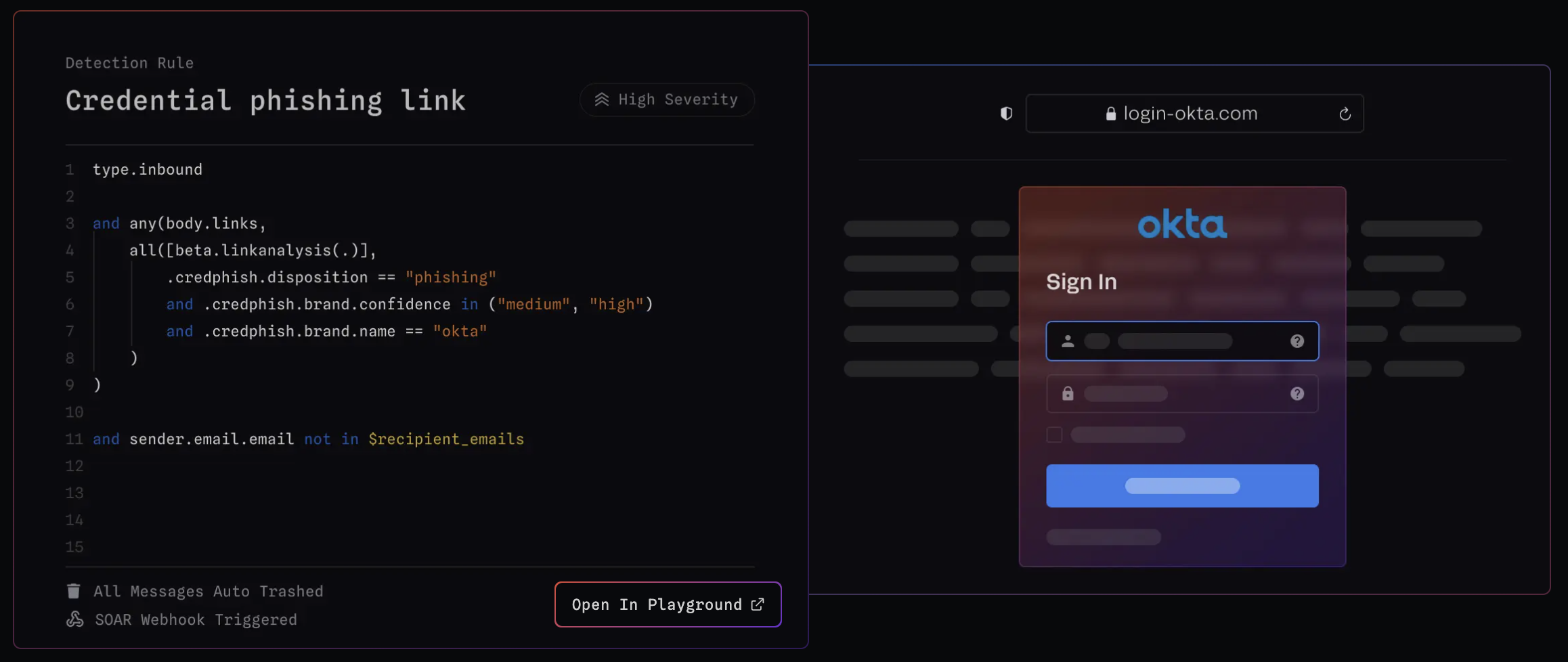
Detecting Credential Phishing using Deep Learning + MQL · Blog · Sublime Security
Tactics & Techniques (25):
Evasion
Free file host
Social engineering
Impersonation: Brand
PDF
QR code
Encryption
OneNote
Free subdomain host
Open redirect
Scripting
Lookalike domain
Spoofing
Free email provider
Image as content
Impersonation: Employee
Credential Phishing
Out of band pivot
HTML smuggling
Impersonation: VIP
Exploit
IPFS
HTML injection
LNK
Punycode
Rule Name & Severity | Last Updated | Author | Types, Tactics & Capabilities | |
|---|---|---|---|---|
Link: Figma design deck with credential theft language | 13h ago Mar 4th, 2026 | Sublime Security | /feeds/core/detection-rules/link-figma-design-deck-with-credential-theft-language-87601924 | |
Link: Apple App Store link to apps impersonating AI adveristing | 20h ago Mar 4th, 2026 | Sublime Security | /feeds/core/detection-rules/link-apple-app-store-link-to-apps-impersonating-ai-adveristing-19b556e6 | |
Attachment: PDF with recipient email in link | 2d ago Mar 3rd, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-pdf-with-recipient-email-in-link-0399d08f | |
Link: Direct download of executable file | 3d ago Mar 2nd, 2026 | Sublime Security | /feeds/core/detection-rules/link-direct-download-of-executable-file-dbbfd077 | |
Link: Google Forms link with credential theft language | 3d ago Mar 2nd, 2026 | Sublime Security | /feeds/core/detection-rules/link-google-forms-link-with-credential-theft-language-0cad40e2 | |
Attachment: PDF with a suspicious string and single URL | 3d ago Mar 2nd, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-pdf-with-a-suspicious-string-and-single-url-3bdbb7ad | |
Link: SharePoint OneNote or PDF link with self sender behavior | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/link-sharepoint-onenote-or-pdf-link-with-self-sender-behavior-588e7203 | |
Link: Multistage landing - ClickUp abuse | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/link-multistage-landing-clickup-abuse-78a5d035 | |
Attachment: PDF with suspicious link and action-oriented language | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-pdf-with-suspicious-link-and-action-oriented-language-816d33a0 | |
Attachment: PDF with multistage landing - ClickUp abuse | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-pdf-with-multistage-landing-clickup-abuse-0dc40316 | |
Link: JavaScript obfuscation with Telegram bot integration | 8d ago Feb 25th, 2026 | Sublime Security | /feeds/core/detection-rules/link-javascript-obfuscation-with-telegram-bot-integration-032a4485 | |
Brand impersonation: DocuSign | 9d ago Feb 24th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-docusign-4d29235c | |
Link: URL redirecting to blob URL | 9d ago Feb 24th, 2026 | Sublime Security | /feeds/core/detection-rules/link-url-redirecting-to-blob-url-1677135b | |
Link: Free file hosting with undisclosed recipients | 10d ago Feb 23rd, 2026 | Sublime Security | /feeds/core/detection-rules/link-free-file-hosting-with-undisclosed-recipients-b6281306 | |
Tax Form: W-8BEN solicitation | 10d ago Feb 23rd, 2026 | Sublime Security | /feeds/core/detection-rules/tax-form-w-8ben-solicitation-a64edb69 | |
Reconnaissance: Email address harvesting attempt | 10d ago Feb 23rd, 2026 | Sublime Security | /feeds/core/detection-rules/reconnaissance-email-address-harvesting-attempt-bb31efbc | |
Attachment: QR code with recipient targeting and special characters | 12d ago Feb 21st, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-qr-code-with-recipient-targeting-and-special-characters-fc9e1c09 | |
Link: Suspicious URL with recipient targeting and special characters | 12d ago Feb 21st, 2026 | Sublime Security | /feeds/core/detection-rules/link-suspicious-url-with-recipient-targeting-and-special-characters-e808be3a | |
Attachment: QR code with suspicious URL patterns in EML file | 12d ago Feb 21st, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-qr-code-with-suspicious-url-patterns-in-eml-file-2289acd5 | |
Cloud storage impersonation with credential theft indicators | 13d ago Feb 20th, 2026 | Sublime Security | /feeds/core/detection-rules/cloud-storage-impersonation-with-credential-theft-indicators-4c20f72c |
Page 1 of 20