- Impersonation: Brand
Attack Types
BEC/Fraud
Callback Phishing
Credential Phishing
Extortion
Malware/Ransomware
Reconnaissance
Spam
Tactics and Techniques
Encryption
Evasion
Exploit
Free email provider
Free file host
Free subdomain host
HTML smuggling
Image as content
Impersonation: Brand
Impersonation: Employee
Impersonation: VIP
IPFS
ISO
LNK
Lookalike domain
Macros
OneNote
Open redirect
Out of band pivot
PDF
Punycode
QR code
Scripting
Social engineering
Spoofing
Detection Methods
Archive analysis
Content analysis
Computer Vision
Exif analysis
File analysis
Header analysis
HTML analysis
Javascript analysis
Macro analysis
Natural Language Understanding
Optical Character Recognition
OLE analysis
PDF analysis
QR code analysis
Sender analysis
Threat intelligence
URL analysis
URL screenshot
Whois
XML analysis
YARA
Tactic or Technique: Impersonation: Brand
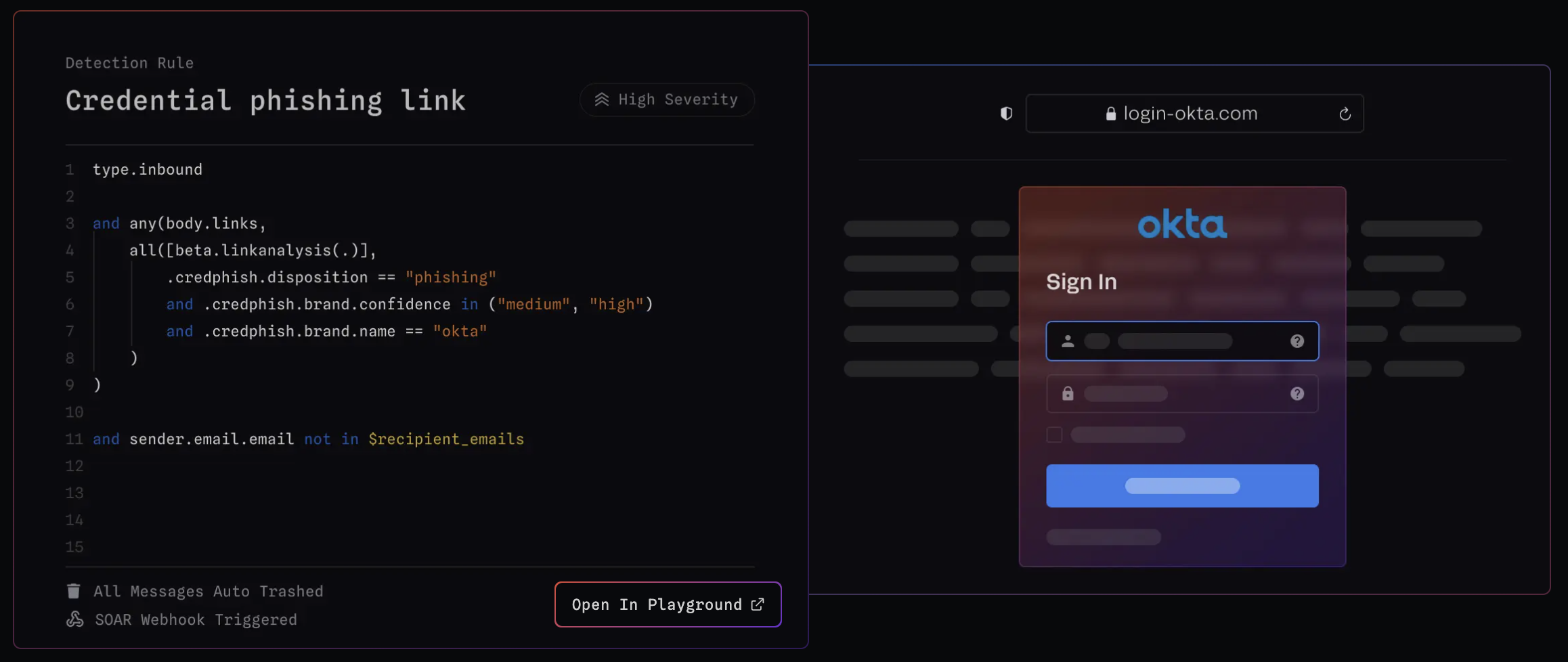
Brand impersonation is a phishing technique where attackers copy the look and feel of trusted companies to make their emails seem legitimate. They recreate logos, colors, templates, and writing styles to mimic well-known brands like Microsoft, Amazon, or PayPal and convince you to trust the message.
They often use lookalike domains to make the links seem real. That could be a small typo, a character swap, or a URL like secure-microsoft[.]com that looks legitimate at first glance. These tricks are meant to get past your defenses and make you more likely to click or respond.
The goal is usually to steal your credentials or convince you to take some kind of action. But over time, these attacks also make it harder to trust what you see in your inbox. Spotting them means looking closely—at the sender address, the way the message is written, and where the links actually go. The differences are subtle, but once you know what to look for, they stand out.
Blog Posts
Tax season email attacks: AdWind RATs and Tycoon 2FA phishing kits · Blog · Sublime Security
Credential phishing Charles Schwab account holders with 2FA bypass · Blog · Sublime Security
Callback phishing via invoice abuse and distribution list relays · Blog · Sublime Security

Talking phish over turkey · Blog · Sublime Security
Living Off the Land: Callback Phishing via Docusign comment · Blog · Sublime Security

Abusing Discord to deliver Agent Tesla malware · Blog · Sublime Security

QR Code Phishing: Decoding Hidden Threats · Blog · Sublime Security

Call Me Maybe? The Rise of Callback Phishing Emails · Blog · Sublime Security
Detecting Credential Phishing using Deep Learning + MQL · Blog · Sublime Security
Detection Methods (16):
Rule Name & Severity | Last Updated | Author | Types, Tactics & Capabilities | |
|---|---|---|---|---|
Brand Impersonation: Disney | 17h ago Mar 4th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-disney-bf90b8fb | |
Link: Apple App Store link to apps impersonating AI adveristing | 20h ago Mar 4th, 2026 | Sublime Security | /feeds/core/detection-rules/link-apple-app-store-link-to-apps-impersonating-ai-adveristing-19b556e6 | |
Brand impersonation: Chase Bank | 3d ago Mar 2nd, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-chase-bank-c680f1e7 | |
Brand impersonation: Zoom via HTML styling | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-zoom-via-html-styling-b717920d | |
Brand impersonation: DocuSign | 9d ago Feb 24th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-docusign-4d29235c | |
Brand impersonation: Meta and subsidiaries | 10d ago Feb 23rd, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-meta-and-subsidiaries-e38f1e3b | |
Brand impersonation: Survey request with credential theft indicators | 13d ago Feb 20th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-survey-request-with-credential-theft-indicators-ea1c0e09 | |
Cloud storage impersonation with credential theft indicators | 13d ago Feb 20th, 2026 | Sublime Security | /feeds/core/detection-rules/cloud-storage-impersonation-with-credential-theft-indicators-4c20f72c | |
Brand impersonation: Gusto | 15d ago Feb 18th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-gusto-54025c1c | |
Link: WordPress login page with Blogspot Binance scam | 16d ago Feb 17th, 2026 | Sublime Security | /feeds/core/detection-rules/link-wordpress-login-page-with-blogspot-binance-scam-909dfae5 | |
Impersonation: Recipient organization in sender display name with credential theft image | 16d ago Feb 17th, 2026 | Sublime Security | /feeds/core/detection-rules/impersonation-recipient-organization-in-sender-display-name-with-credential-theft-image-6abfb20e | |
Brand impersonation: American Express (AMEX) | 16d ago Feb 17th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-american-express-amex-992a9fa9 | |
Brand impersonation: Punchbowl | 20d ago Feb 13th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-punchbowl-58937ba0 | |
Brand Impersonation: PayPal | 20d ago Feb 13th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-paypal-a6b2ceee | |
Credential phishing: Tax form impersonation with payment request | 20d ago Feb 13th, 2026 | Sublime Security | /feeds/core/detection-rules/credential-phishing-tax-form-impersonation-with-payment-request-717695cf | |
Brand impersonation: Amazon | 20d ago Feb 13th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-amazon-13fc967d | |
Brand impersonation: USPS | 20d ago Feb 13th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-usps-28b9130a | |
Brand impersonation: TikTok | 21d ago Feb 12th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-tiktok-aaacc8b7 | |
Brand impersonation: Dropbox | 21d ago Feb 12th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-dropbox-61f11d12 | |
Brand impersonation: Google Meet with malicious link | 21d ago Feb 12th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-google-meet-with-malicious-link-d488d85a |
Page 1 of 13