- Header analysis
Attack Types
BEC/Fraud
Callback Phishing
Credential Phishing
Extortion
Malware/Ransomware
Reconnaissance
Spam
Tactics and Techniques
Encryption
Evasion
Exploit
Free email provider
Free file host
Free subdomain host
HTML smuggling
Image as content
Impersonation: Brand
Impersonation: Employee
Impersonation: VIP
IPFS
ISO
LNK
Lookalike domain
Macros
OneNote
Open redirect
Out of band pivot
PDF
Punycode
QR code
Scripting
Social engineering
Spoofing
Detection Methods
Archive analysis
Content analysis
Computer Vision
Exif analysis
File analysis
Header analysis
HTML analysis
Javascript analysis
Macro analysis
Natural Language Understanding
Optical Character Recognition
OLE analysis
PDF analysis
QR code analysis
Sender analysis
Threat intelligence
URL analysis
URL screenshot
Whois
XML analysis
YARA
Detection Method: Header analysis
Header analysis inspects the metadata in message headers to find suspicious patterns, anomalies, or inconsistencies that could indicate phishing, spoofing, or other types of malicious activity. It looks at various header fields like routing information, authentication results, and sender verification data to help spot potential threats.
This includes sender authentication headers like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) results to verify the sender's legitimacy. It also checks how the email traveled through mail servers, looking for any unusual routing that might suggest tampering.
Header analysis can detect:
- Email spoofing, where attackers forge the sender’s address to appear legitimate
- Mismatched or inconsistent sender details
- Suspicious return paths that don’t match the expected sender
- Unusual routing patterns that stand out from normal email flow
- Authentication failures that signal potential impersonation attempts
For example, attackers might try to forge email headers to make phishing emails appear as if they’re coming from a trusted source like your bank or your company’s internal email. Header analysis helps you catch these attempts by identifying mismatches between the displayed sender and the actual sending server.
Blog Posts
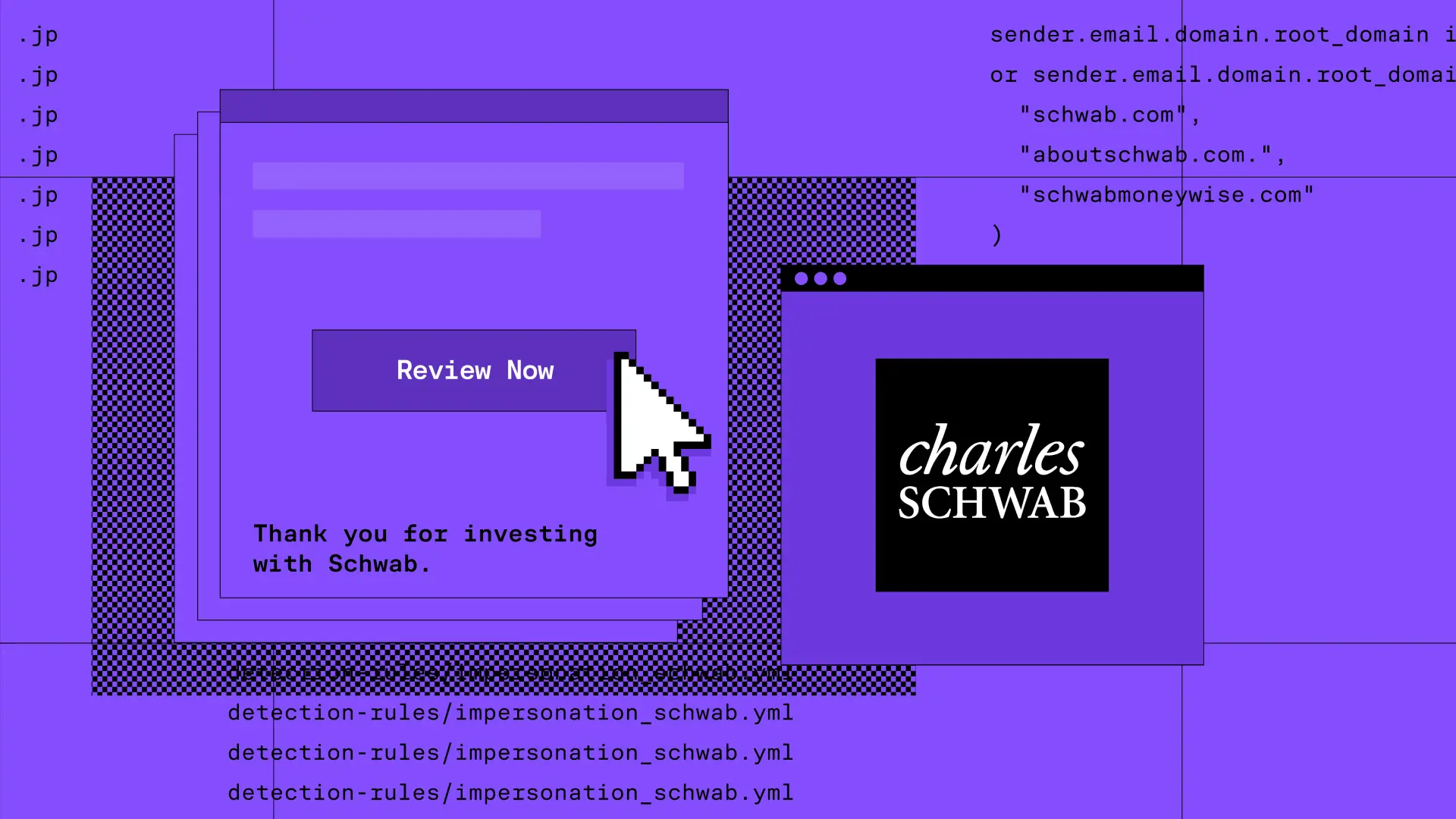
Credential phishing Charles Schwab account holders with 2FA bypass · Blog · Sublime Security
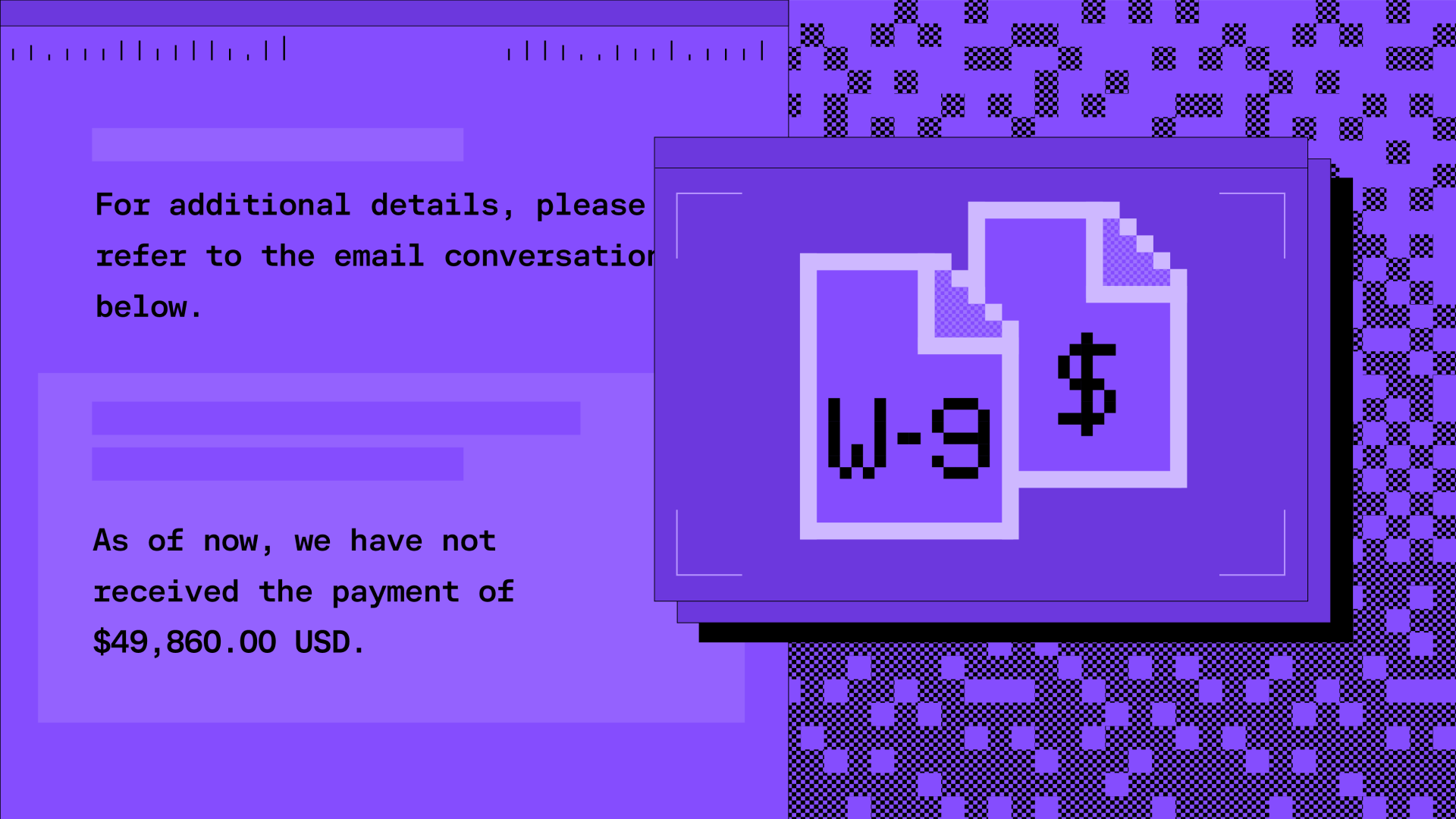
Hiding a $50,000 BEC financial fraud in a fake email thread · Blog · Sublime Security
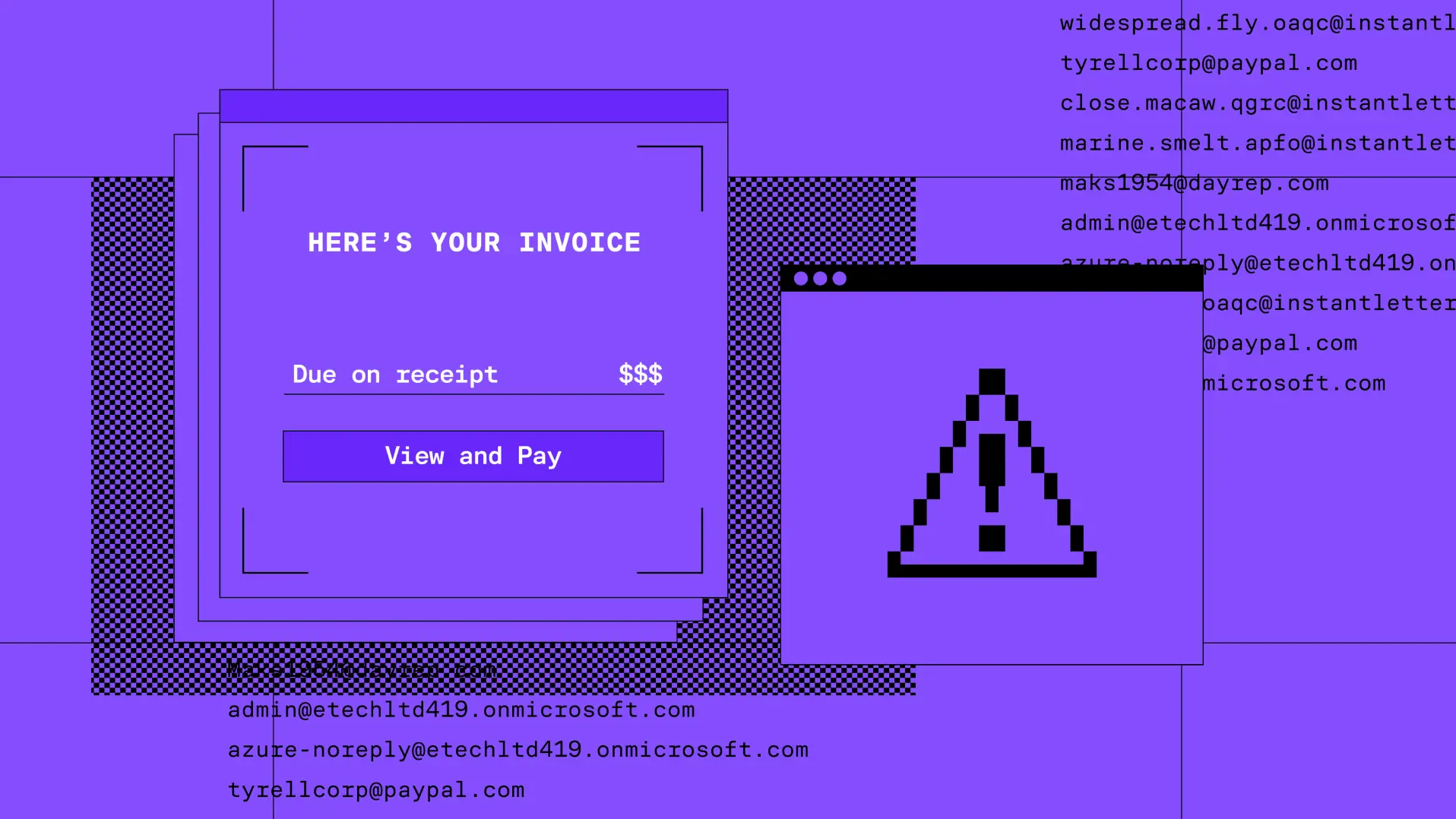
Callback phishing via invoice abuse and distribution list relays · Blog · Sublime Security

Detecting malicious AnonymousFox email messages sent from compromised sites · Blog · Sublime Security

Talking phish over turkey · Blog · Sublime Security

Hidden credential phishing within EML attachments · Blog · Sublime Security

Living Off the Land: Credential Phishing via Docusign abuse · Blog · Sublime Security
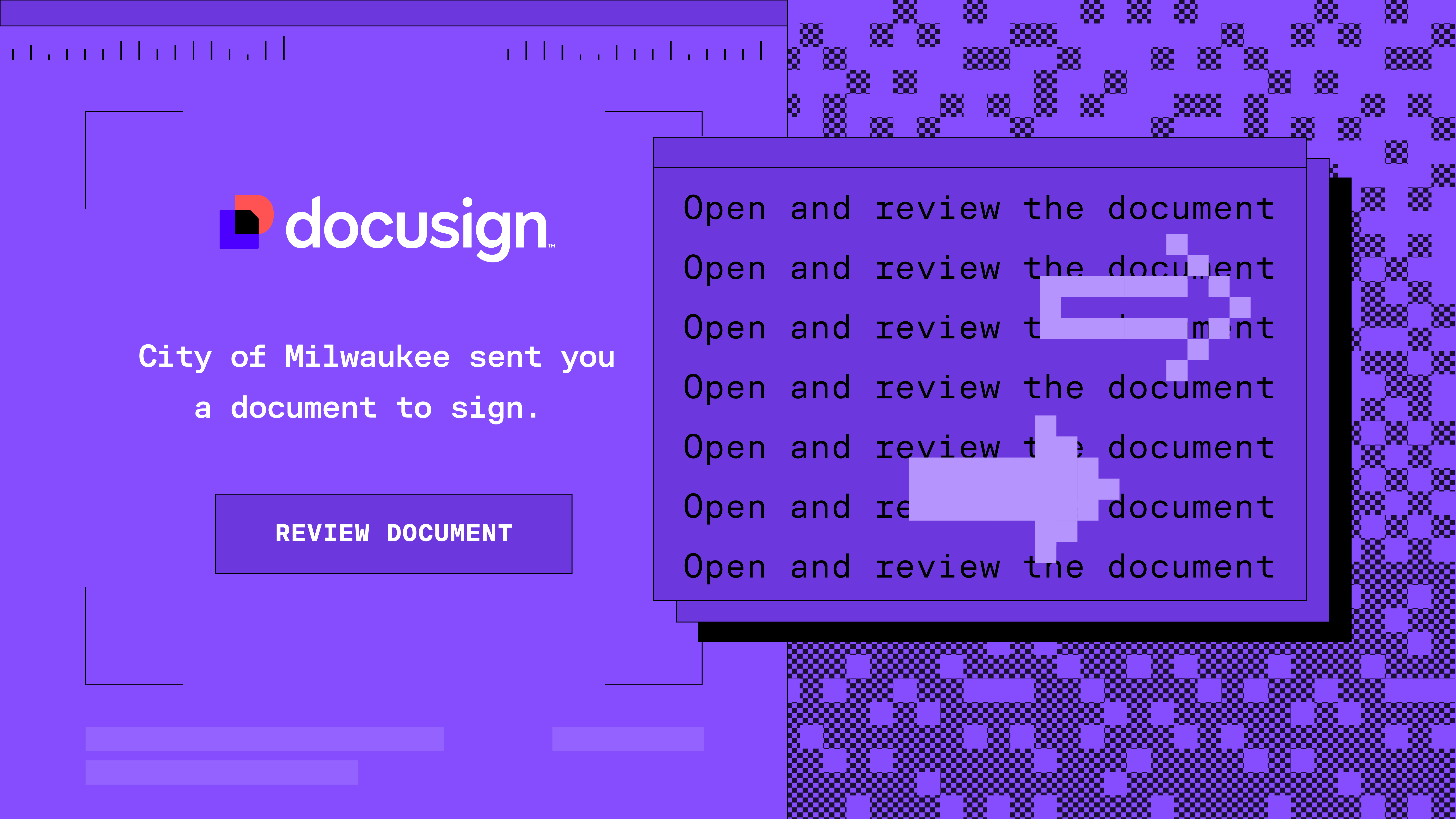
Living Off the Land: Callback Phishing via Docusign comment · Blog · Sublime Security

Adversarial ML: Extortion via LLM Manipulation Tactics · Blog · Sublime Security

QR Code Phishing: Decoding Hidden Threats · Blog · Sublime Security
Attack Types (7):
Tactics & Techniques (21):
Rule Name & Severity | Last Updated | Author | Types, Tactics & Capabilities | |
|---|---|---|---|---|
Brand Impersonation: Disney | 17h ago Mar 4th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-disney-bf90b8fb | |
Service abuse: DocSend share from an unsolicited reply-to address | 19h ago Mar 4th, 2026 | Sublime Security | /feeds/core/detection-rules/service-abuse-docsend-share-from-an-unsolicited-reply-to-address-b377e64c | |
BEC with unusual reply-to or return-path mismatch | 2d ago Mar 3rd, 2026 | Sublime Security | /feeds/core/detection-rules/bec-with-unusual-reply-to-or-return-path-mismatch-83e5e2df | |
Brand impersonation: Chase Bank | 3d ago Mar 2nd, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-chase-bank-c680f1e7 | |
VIP impersonation with w2 request with reply-to mismatch | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/vip-impersonation-with-w2-request-with-reply-to-mismatch-e7e73fad | |
Link: SharePoint OneNote or PDF link with self sender behavior | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/link-sharepoint-onenote-or-pdf-link-with-self-sender-behavior-588e7203 | |
Headers: risky-recover-production message ID | 7d ago Feb 26th, 2026 | Sublime Security | /feeds/core/detection-rules/headers-risky-recover-production-message-id-4cc0b5dc | |
Reconnaissance: Empty message from uncommon sender | 8d ago Feb 25th, 2026 | Sublime Security | /feeds/core/detection-rules/reconnaissance-empty-message-from-uncommon-sender-b347cdbc | |
VIP / Executive impersonation (strict match, untrusted) | 8d ago Feb 25th, 2026 | Sublime Security | /feeds/core/detection-rules/vip-executive-impersonation-strict-match-untrusted-e42c84b7 | |
Brand impersonation: DocuSign | 9d ago Feb 24th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-docusign-4d29235c | |
Spam: Sendersrv.com with financial communications and unsubscribe language | 9d ago Feb 24th, 2026 | Sublime Security | /feeds/core/detection-rules/spam-sendersrvcom-with-financial-communications-and-unsubscribe-language-69570820 | |
Link: Free file hosting with undisclosed recipients | 10d ago Feb 23rd, 2026 | Sublime Security | /feeds/core/detection-rules/link-free-file-hosting-with-undisclosed-recipients-b6281306 | |
Brand impersonation: Meta and subsidiaries | 10d ago Feb 23rd, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-meta-and-subsidiaries-e38f1e3b | |
Tax Form: W-8BEN solicitation | 10d ago Feb 23rd, 2026 | Sublime Security | /feeds/core/detection-rules/tax-form-w-8ben-solicitation-a64edb69 | |
Reconnaissance: Email address harvesting attempt | 10d ago Feb 23rd, 2026 | Sublime Security | /feeds/core/detection-rules/reconnaissance-email-address-harvesting-attempt-bb31efbc | |
Brand impersonation: Survey request with credential theft indicators | 13d ago Feb 20th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-survey-request-with-credential-theft-indicators-ea1c0e09 | |
Cloud storage impersonation with credential theft indicators | 13d ago Feb 20th, 2026 | Sublime Security | /feeds/core/detection-rules/cloud-storage-impersonation-with-credential-theft-indicators-4c20f72c | |
Brand impersonation: Gusto | 15d ago Feb 18th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-gusto-54025c1c | |
Brand impersonation: American Express (AMEX) | 16d ago Feb 17th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-american-express-amex-992a9fa9 | |
File sharing link with a suspicious subject | 16d ago Feb 17th, 2026 | Sublime Security | /feeds/core/detection-rules/file-sharing-link-with-a-suspicious-subject-a306e2a6 |
Page 1 of 18