Attack Types
BEC/Fraud
Callback Phishing
Credential Phishing
Extortion
Malware/Ransomware
Reconnaissance
Spam
Tactics and Techniques
Encryption
Evasion
Exploit
Free email provider
Free file host
Free subdomain host
HTML smuggling
Image as content
Impersonation: Brand
Impersonation: Employee
Impersonation: VIP
IPFS
ISO
LNK
Lookalike domain
Macros
OneNote
Open redirect
Out of band pivot
PDF
Punycode
QR code
Scripting
Social engineering
Spoofing
Detection Methods
Archive analysis
Content analysis
Computer Vision
Exif analysis
File analysis
Header analysis
HTML analysis
Javascript analysis
Macro analysis
Natural Language Understanding
Optical Character Recognition
OLE analysis
PDF analysis
QR code analysis
Sender analysis
Threat intelligence
URL analysis
URL screenshot
Whois
XML analysis
YARA
Tactic or Technique: Evasion
Evasion techniques help attackers sneak past email security filters by hiding or disguising malicious content. These tactics are designed to fool both traditional scanners and newer AI-based systems by changing how the message is structured or displayed.
You might see phishing content buried under blocks of harmless-looking text, or important details shown as images so they can't be scanned. Some messages break up keywords using hidden HTML or use misspelled words and lookalike characters to trick you into missing the signs.
More advanced versions use JavaScript that reveals the payload only after the message has passed through security checks. Others try to confuse AI systems with prompt injection or strange formatting.
These techniques create gaps in protection and give attackers a better chance of reaching your inbox. Spotting them early is key. The more familiar you are with how these tricks work, the easier it is to catch them before they do damage.
Blog Posts
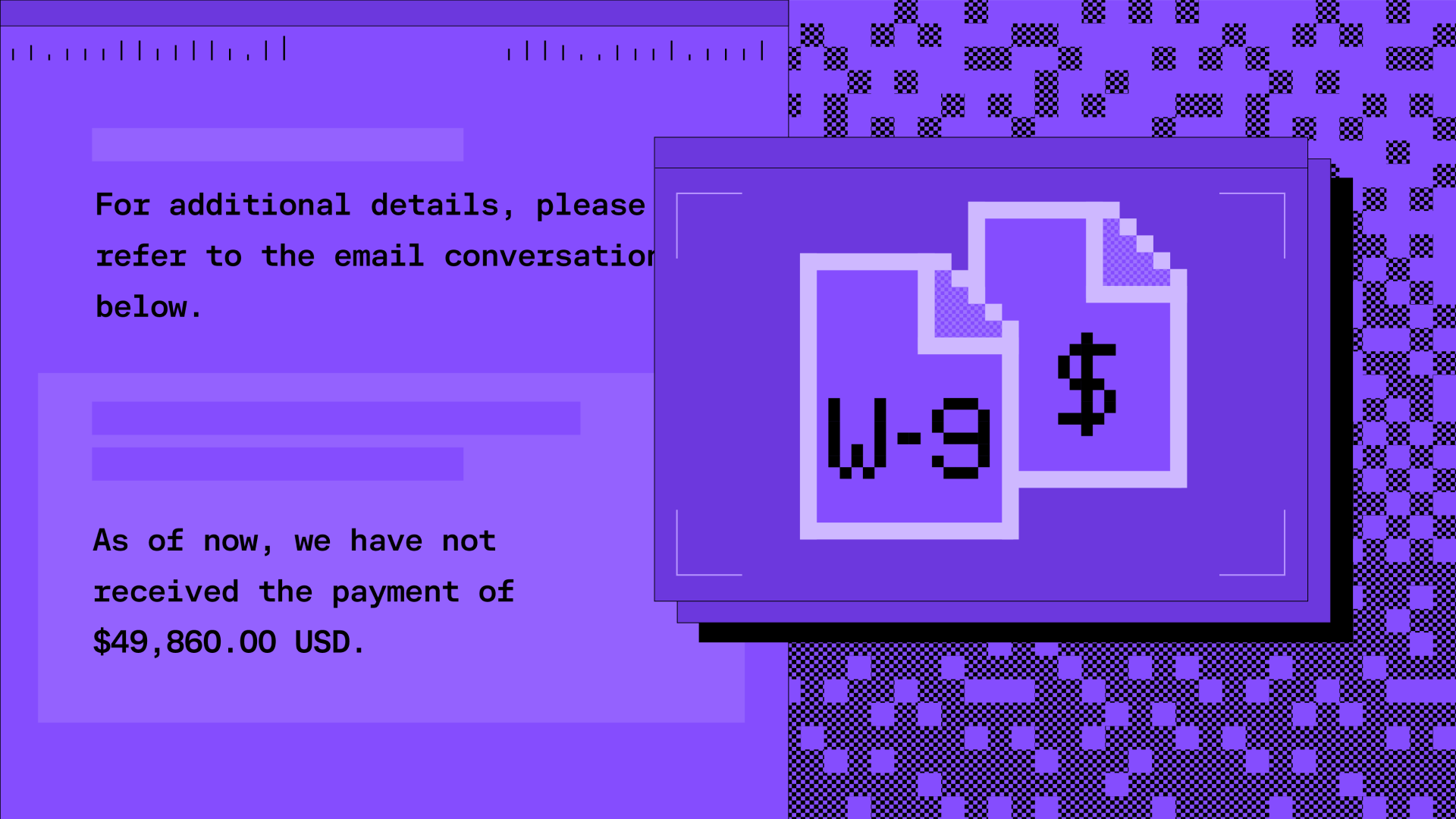
Hiding a $50,000 BEC financial fraud in a fake email thread · Blog · Sublime Security
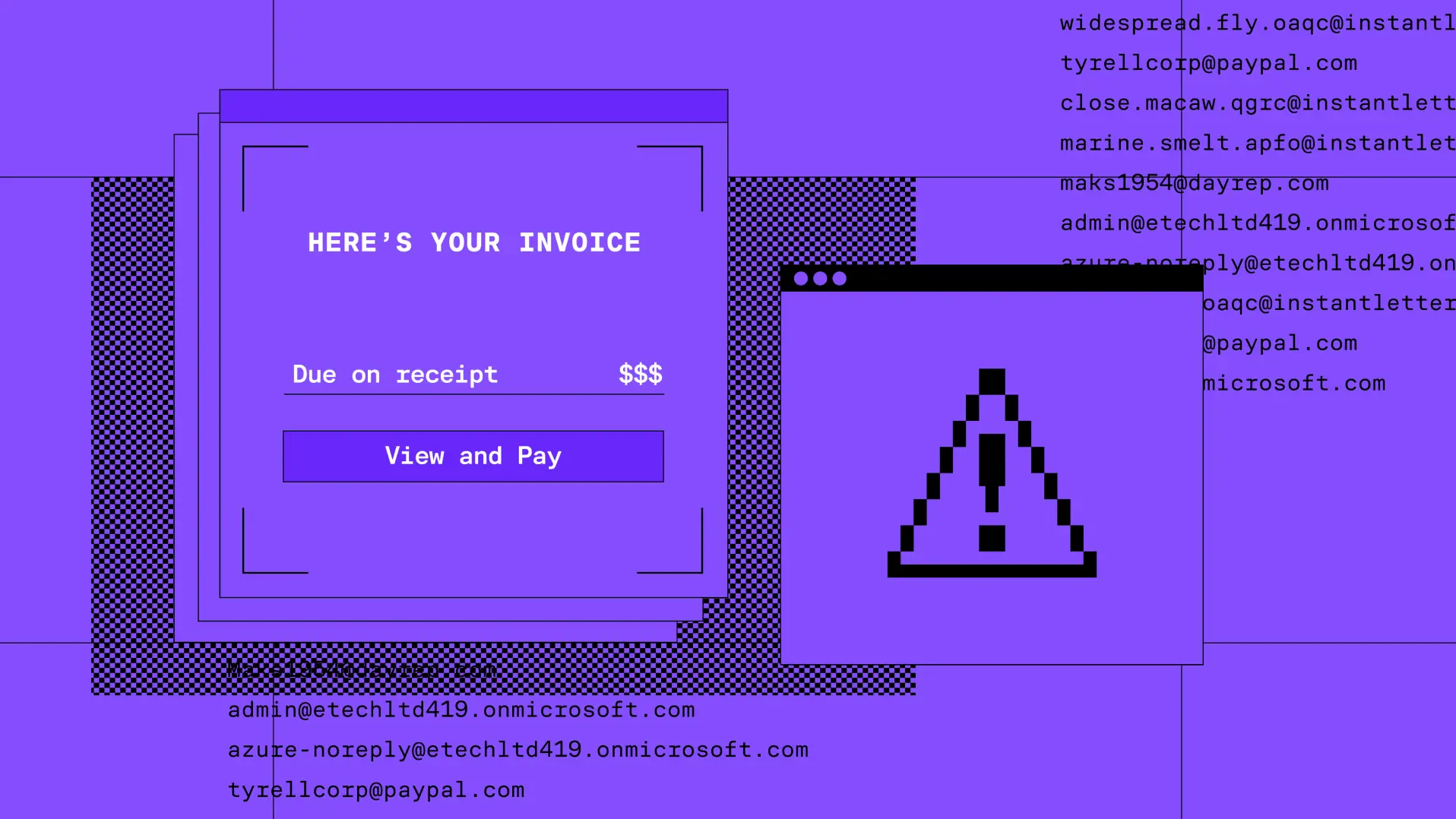
Callback phishing via invoice abuse and distribution list relays · Blog · Sublime Security

Hidden credential phishing within EML attachments · Blog · Sublime Security

Living Off the Land: Credential Phishing via Docusign abuse · Blog · Sublime Security
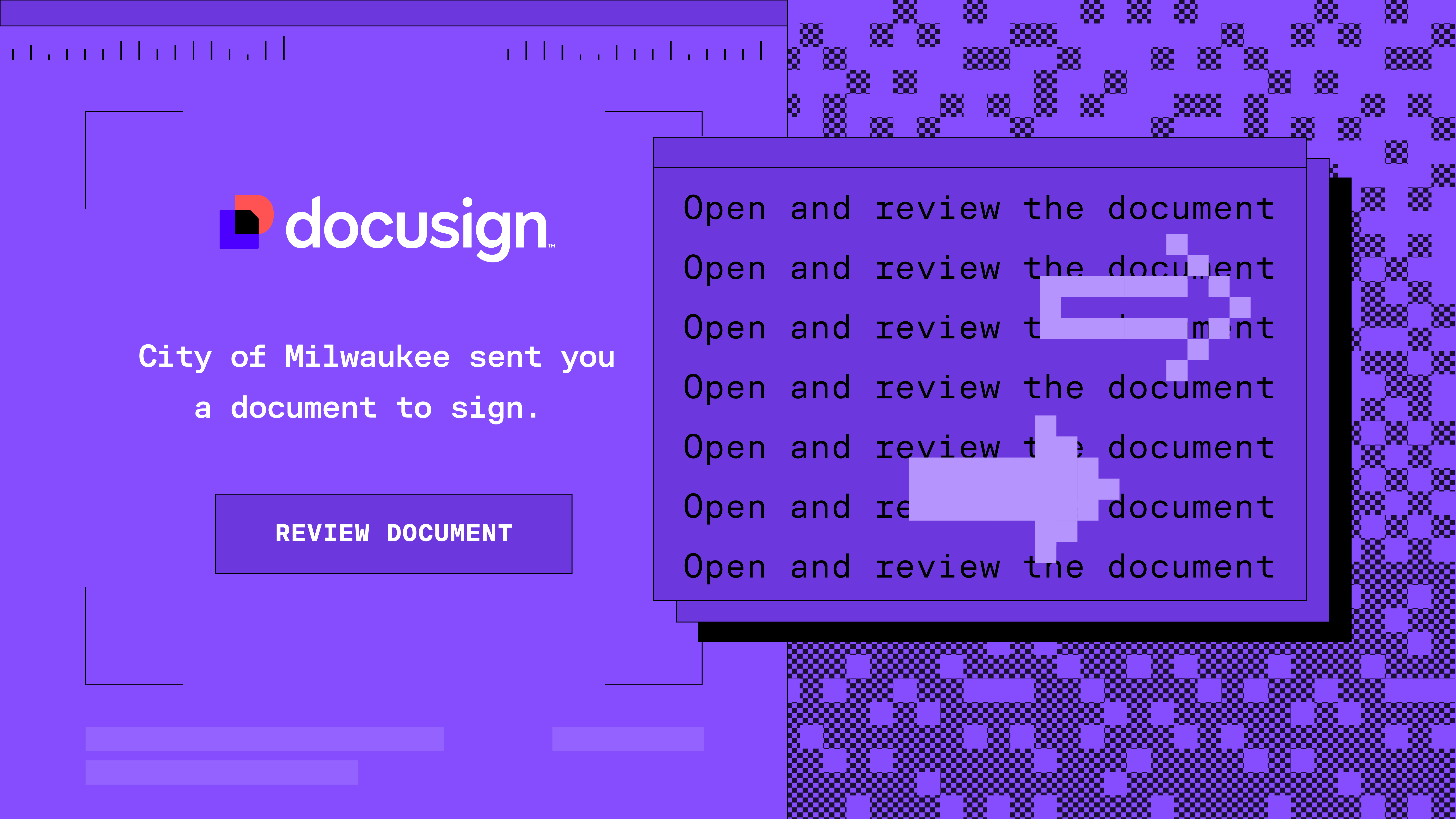
Living Off the Land: Callback Phishing via Docusign comment · Blog · Sublime Security

Gotta Catch 'Em All: Detecting PikaBot Delivery Techniques · Blog · Sublime Security

Detecting QakBot: WSF attachments, OneNote files, and generic attack surface reduction · Blog · Sublime Security
Detection Methods (20):
Natural Language Understanding
Computer Vision
Optical Character Recognition
URL analysis
URL screenshot
Sender analysis
HTML analysis
Content analysis
Header analysis
File analysis
Exif analysis
Threat intelligence
Whois
Javascript analysis
QR code analysis
Archive analysis
Macro analysis
YARA
OLE analysis
XML analysis
Rule Name & Severity | Last Updated | Author | Types, Tactics & Capabilities | |
|---|---|---|---|---|
Link: Figma design deck with credential theft language | 13h ago Mar 4th, 2026 | Sublime Security | /feeds/core/detection-rules/link-figma-design-deck-with-credential-theft-language-87601924 | |
Service abuse: HungerRush domain with SendGrid tracking targeting ProtonMail | 15h ago Mar 4th, 2026 | Sublime Security | /feeds/core/detection-rules/service-abuse-hungerrush-domain-with-sendgrid-tracking-targeting-protonmail-73f62e74 | |
Service abuse: DocSend share from an unsolicited reply-to address | 18h ago Mar 4th, 2026 | Sublime Security | /feeds/core/detection-rules/service-abuse-docsend-share-from-an-unsolicited-reply-to-address-b377e64c | |
BEC with unusual reply-to or return-path mismatch | 2d ago Mar 3rd, 2026 | Sublime Security | /feeds/core/detection-rules/bec-with-unusual-reply-to-or-return-path-mismatch-83e5e2df | |
Link: Direct download of executable file | 3d ago Mar 2nd, 2026 | Sublime Security | /feeds/core/detection-rules/link-direct-download-of-executable-file-dbbfd077 | |
Fake warning banner using confusable characters | 3d ago Mar 2nd, 2026 | Sublime Security | /feeds/core/detection-rules/fake-warning-banner-using-confusable-characters-179ee1ff | |
Attachment: PDF with a suspicious string and single URL | 3d ago Mar 2nd, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-pdf-with-a-suspicious-string-and-single-url-3bdbb7ad | |
Attachment: PDF Object Hash - Encrypted PDFs with fake payment notification | 3d ago Mar 2nd, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-pdf-object-hash-encrypted-pdfs-with-fake-payment-notification-a8a19bae | |
Attachment: Finance themed PDF with observed phishing template | 3d ago Mar 2nd, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-finance-themed-pdf-with-observed-phishing-template-c936f7cc | |
Link: SharePoint OneNote or PDF link with self sender behavior | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/link-sharepoint-onenote-or-pdf-link-with-self-sender-behavior-588e7203 | |
Link: Multistage landing - ClickUp abuse | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/link-multistage-landing-clickup-abuse-78a5d035 | |
Attachment: PDF with suspicious link and action-oriented language | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-pdf-with-suspicious-link-and-action-oriented-language-816d33a0 | |
Attachment: PDF with multistage landing - ClickUp abuse | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-pdf-with-multistage-landing-clickup-abuse-0dc40316 | |
Attachment: PDF with ReportLab library and default metadata | 6d ago Feb 27th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-pdf-with-reportlab-library-and-default-metadata-7094bfdd | |
Attachment: Encrypted PDF with credential theft body | 7d ago Feb 26th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-encrypted-pdf-with-credential-theft-body-c9596c9a | |
Headers: risky-recover-production message ID | 7d ago Feb 26th, 2026 | Sublime Security | /feeds/core/detection-rules/headers-risky-recover-production-message-id-4cc0b5dc | |
Reconnaissance: Empty message from uncommon sender | 8d ago Feb 25th, 2026 | Sublime Security | /feeds/core/detection-rules/reconnaissance-empty-message-from-uncommon-sender-b347cdbc | |
Credential theft with 'safe content' deception and social engineering topics | 8d ago Feb 25th, 2026 | Sublime Security | /feeds/core/detection-rules/credential-theft-with-safe-content-deception-and-social-engineering-topics-22ceee0d | |
Link: JavaScript obfuscation with Telegram bot integration | 8d ago Feb 25th, 2026 | Sublime Security | /feeds/core/detection-rules/link-javascript-obfuscation-with-telegram-bot-integration-032a4485 | |
Spam: Sendersrv.com with financial communications and unsubscribe language | 9d ago Feb 24th, 2026 | Sublime Security | /feeds/core/detection-rules/spam-sendersrvcom-with-financial-communications-and-unsubscribe-language-69570820 |
Page 1 of 18