Attack Types
BEC/Fraud
Callback Phishing
Credential Phishing
Extortion
Malware/Ransomware
Reconnaissance
Spam
Tactics and Techniques
Encryption
Evasion
Exploit
Free email provider
Free file host
Free subdomain host
HTML smuggling
Image as content
Impersonation: Brand
Impersonation: Employee
Impersonation: VIP
IPFS
ISO
LNK
Lookalike domain
Macros
OneNote
Open redirect
Out of band pivot
PDF
Punycode
QR code
Scripting
Social engineering
Spoofing
Detection Methods
Archive analysis
Content analysis
Computer Vision
Exif analysis
File analysis
Header analysis
HTML analysis
Javascript analysis
Macro analysis
Natural Language Understanding
Optical Character Recognition
OLE analysis
PDF analysis
QR code analysis
Sender analysis
Threat intelligence
URL analysis
URL screenshot
Whois
XML analysis
YARA
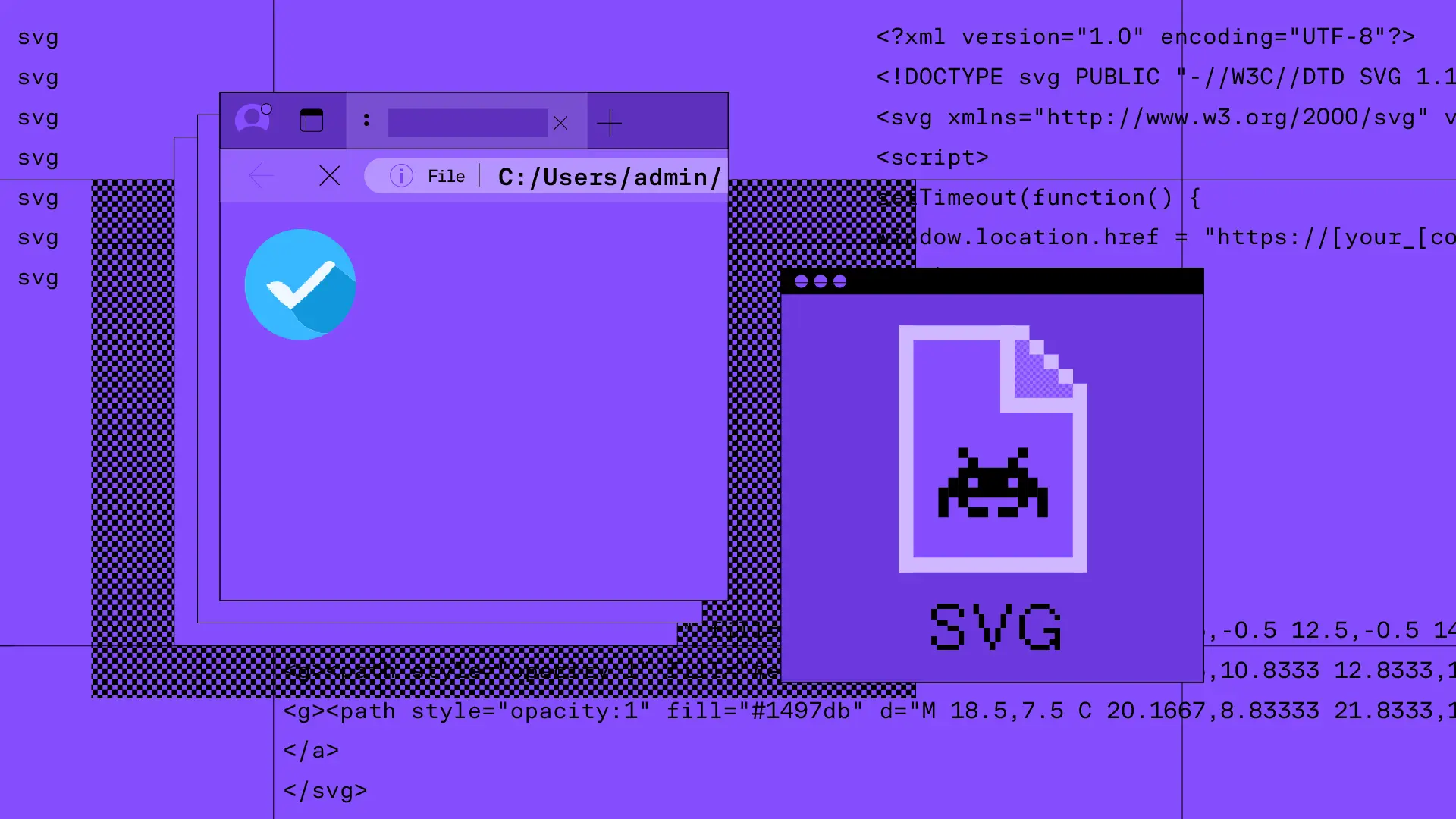
Tactic or Technique: Scripting
Attackers use scripting languages like JavaScript, VBScript, and PowerShell to run malicious code delivered through phishing emails or compromised websites. These scripts can load hidden content, redirect you to phishing pages, or silently steal data in the background.
To avoid detection, attackers often scramble the code using encryption, compression, or multiple layers of encoding. This makes it harder for both security tools and analysts to understand what the script is doing.
Scripting is flexible and often used to fingerprint your browser, deliver customized payloads, or create a connection to an attacker-controlled server. Once that connection is active, the script can pull down more malware, collect sensitive information, or give an attacker continued access to your device.
Blog Posts
Attack Types (4):
Detection Methods (17):
Rule Name & Severity | Last Updated | Author | Types, Tactics & Capabilities | |
|---|---|---|---|---|
Link: JavaScript obfuscation with Telegram bot integration | 8d ago Feb 25th, 2026 | Sublime Security | /feeds/core/detection-rules/link-javascript-obfuscation-with-telegram-bot-integration-032a4485 | |
Attachment: cmd file extension | 24d ago Feb 9th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-cmd-file-extension-a902b8ed | |
Attachment: ICS with embedded Javascript in SVG file | 1mo ago Jan 29th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-ics-with-embedded-javascript-in-svg-file-d5201a19 | |
Attachment: Embedded Javascript in SVG file | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-embedded-javascript-in-svg-file-f70293bc | |
Attachment: HTML smuggling with ROT13 | 1mo ago Jan 12th, 2026 | @Kyle_Parrish_ | /feeds/core/detection-rules/attachment-html-smuggling-with-rot13-6eacc4cf | |
Attachment: Macro with suspected use of COM ShellBrowserWindow object for process creation | 1mo ago Jan 12th, 2026 | @ajpc500 | /feeds/core/detection-rules/attachment-macro-with-suspected-use-of-com-shellbrowserwindow-object-for-process-creation-527fc7f0 | |
Attachment: .csproj with suspicious commands | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-csproj-with-suspicious-commands-fe45b81d | |
Attachment: CVE-2021-40444 - MSHTML Remote Code Execution Vulnerability | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-cve-2021-40444-mshtml-remote-code-execution-vulnerability-8cefcf7f | |
CVE-2023-5631 - Roundcube Webmail XSS via crafted SVG | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/cve-2023-5631-roundcube-webmail-xss-via-crafted-svg-8405d61b | |
Attachment: HTML smuggling with eval and atob via calendar invite | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-html-smuggling-with-eval-and-atob-via-calendar-invite-597c2edd | |
Attachment: HTML smuggling with atob and high entropy via calendar invite | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-html-smuggling-with-atob-and-high-entropy-via-calendar-invite-94d84614 | |
Attachment: EML containing a base64 encoded script | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-eml-containing-a-base64-encoded-script-fc3d9445 | |
Attachment: Encrypted Microsoft Office file (unsolicited) | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-encrypted-microsoft-office-file-unsolicited-1e47e953 | |
Attachment: HTML file contains exclusively Javascript | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-html-file-contains-exclusively-javascript-b6d38168 | |
Attachment: HTML attachment with login portal indicators | 1mo ago Jan 12th, 2026 | @ajpc500 | /feeds/core/detection-rules/attachment-html-attachment-with-login-portal-indicators-3aabf4a7 | |
Attachment: HTML with hidden body | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-html-with-hidden-body-b059a781 | |
Attachment: HTML file with reference to recipient and suspicious patterns | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-html-file-with-reference-to-recipient-and-suspicious-patterns-5333493d | |
Attachment: HTML smuggling with atob and high entropy | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-html-smuggling-with-atob-and-high-entropy-03fcac11 | |
Attachment: HTML smuggling with auto-downloaded file | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-html-smuggling-with-auto-downloaded-file-abf724f5 | |
Attachment: HTML smuggling 'body onload' linking to suspicious destination | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-html-smuggling-body-onload-linking-to-suspicious-destination-c1e2beed |
Page 1 of 4