- Optical Character Recognition
Attack Types
BEC/Fraud
Callback Phishing
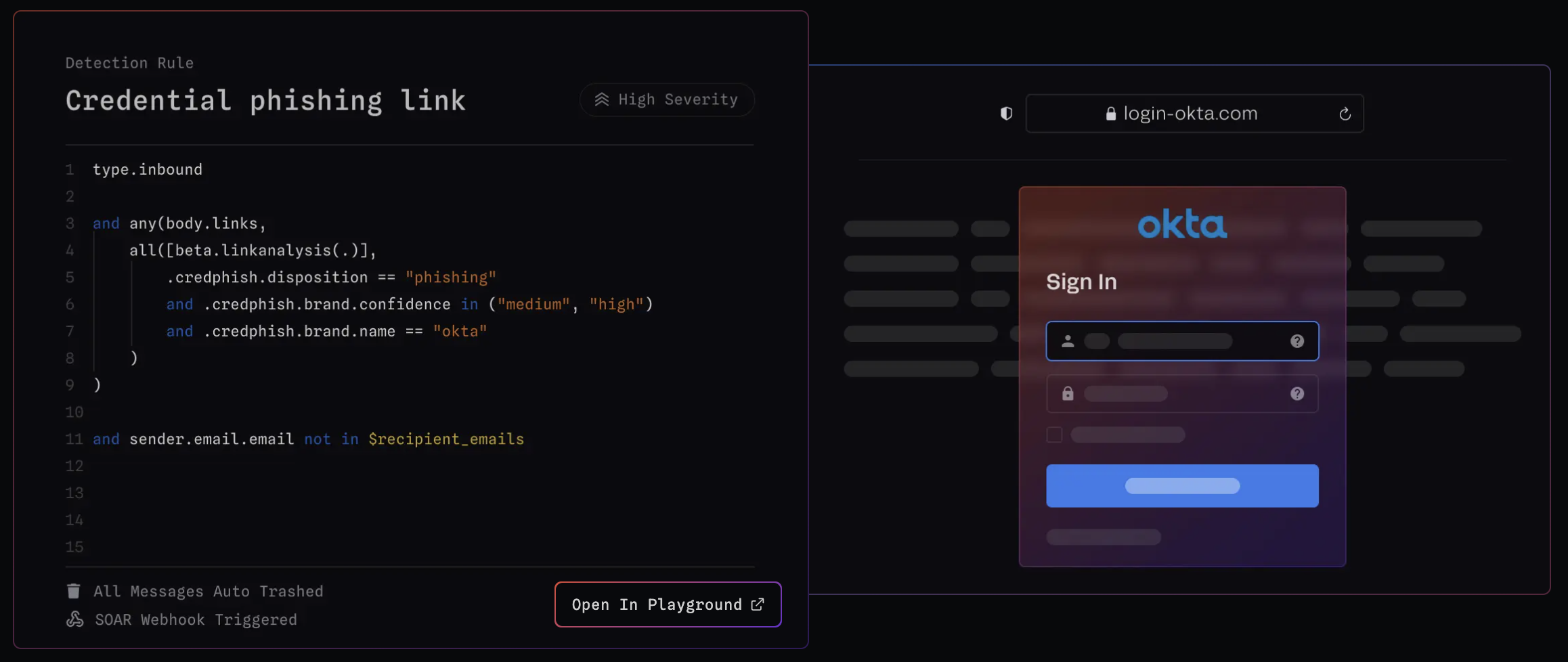
Credential Phishing
Extortion
Malware/Ransomware
Reconnaissance
Spam
Tactics and Techniques
Encryption
Evasion
Exploit
Free email provider
Free file host
Free subdomain host
HTML smuggling
Image as content
Impersonation: Brand
Impersonation: Employee
Impersonation: VIP
IPFS
ISO
LNK
Lookalike domain
Macros
OneNote
Open redirect
Out of band pivot
PDF
Punycode
QR code
Scripting
Social engineering
Spoofing
Detection Methods
Archive analysis
Content analysis
Computer Vision
Exif analysis
File analysis
Header analysis
HTML analysis
Javascript analysis
Macro analysis
Natural Language Understanding
Optical Character Recognition
OLE analysis
PDF analysis
QR code analysis
Sender analysis
Threat intelligence
URL analysis
URL screenshot
Whois
XML analysis
YARA
Detection Method: Optical Character Recognition
OCR (Optical Character Recognition) helps systems read and analyze text in images, screenshots, and scanned documents. This method turns visual text into machine-readable content, allowing your security tools to catch things that would normally slip past text-based filters.
OCR can help you detect:
- Phishing text hidden in images to bypass text-based filters
- Suspicious language or instructions in scanned documents
- QR codes with malicious links
- Brand impersonation attempts using image-based logos or text
- Requests for sensitive information disguised in images
For example, attackers often embed fake login prompts or instructions to call a "customer support" number in images. These tricks are designed to bypass traditional security filters, but OCR can extract and analyze the text to flag it as malicious before it reaches you.
Blog Posts
Tactics & Techniques (15):
Rule Name & Severity | Last Updated | Author | Types, Tactics & Capabilities | |
|---|---|---|---|---|
Link: Figma design deck with credential theft language | 13h ago Mar 4th, 2026 | Sublime Security | /feeds/core/detection-rules/link-figma-design-deck-with-credential-theft-language-87601924 | |
Cloud storage impersonation with credential theft indicators | 13d ago Feb 20th, 2026 | Sublime Security | /feeds/core/detection-rules/cloud-storage-impersonation-with-credential-theft-indicators-4c20f72c | |
Impersonation: Recipient organization in sender display name with credential theft image | 16d ago Feb 17th, 2026 | Sublime Security | /feeds/core/detection-rules/impersonation-recipient-organization-in-sender-display-name-with-credential-theft-image-6abfb20e | |
Brand impersonation: TikTok | 21d ago Feb 12th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-tiktok-aaacc8b7 | |
Brand impersonation: Fake Fax | 28d ago Feb 5th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-fake-fax-2a96b90a | |
Attachment: Legal themed message or PDF with suspicious indicators | 28d ago Feb 5th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-legal-themed-message-or-pdf-with-suspicious-indicators-19133301 | |
Attachment: Office file with document sharing and browser instruction lures | 1mo ago Jan 29th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-office-file-with-document-sharing-and-browser-instruction-lures-b1250a4b | |
Link: Microsoft Dynamics 365 form phishing | 1mo ago Jan 27th, 2026 | Sublime Security | /feeds/core/detection-rules/link-microsoft-dynamics-365-form-phishing-f72b9085 | |
Attachment: Fake lawyer & sports agent identities | 1mo ago Jan 26th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-fake-lawyer-and-sports-agent-identities-7d3a2478 | |
Callback phishing in body or attachment (untrusted sender) | 1mo ago Jan 22nd, 2026 | Sublime Security | /feeds/core/detection-rules/callback-phishing-in-body-or-attachment-untrusted-sender-b93c6f94 | |
Attachment: Invoice and W-9 PDFs with suspicious creators | 1mo ago Jan 21st, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-invoice-and-w-9-pdfs-with-suspicious-creators-305d6e32 | |
Brand impersonation: SendGrid | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-sendgrid-d800124f | |
Open Redirect: Google domain with /url path and suspicious indicators | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/open-redirect-google-domain-with-url-path-and-suspicious-indicators-fc5adf74 | |
Link to auto-downloaded file with Google Drive branding | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/link-to-auto-downloaded-file-with-google-drive-branding-4b5343be | |
Brand impersonation: Microsoft with low reputation links | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/brand-impersonation-microsoft-with-low-reputation-links-b59201b6 | |
Link: Multistage landing - Abused Adobe Acrobat hosted PDF | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/link-multistage-landing-abused-adobe-acrobat-hosted-pdf-609081ef | |
Link: Multistage landing - Scribd document | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/link-multistage-landing-scribd-document-afa9807d | |
Suspicious recipient pattern and language with low reputation link to login | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/suspicious-recipient-pattern-and-language-with-low-reputation-link-to-login-a8ea0402 | |
Attachment: Microsoft 365 credential phishing | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-microsoft-365-credential-phishing-edce0229 | |
Attachment: PDF with credential theft language and link to a free subdomain (unsolicited) | 1mo ago Jan 12th, 2026 | Sublime Security | /feeds/core/detection-rules/attachment-pdf-with-credential-theft-language-and-link-to-a-free-subdomain-unsolicited-90f4ef4e |
Page 1 of 4